PlayCrypt Analysis
1.Overview
Recently, Antiy CERT has monitored an active trend of PLAY ransomware incidents. PLAY ransomware, also known as PlayCrypt, was developed and operated by Balloonfly[1] and was first discovered in June 2022. The ransomware is mainly spread through phishing emails and vulnerabilities, and adopts the Double Extortion mode of “threatening to expose enterprise data + encrypting data”. Since November 3, 2022, the Balloonfly attack group has been posting victim information and stolen data on a Tor-specific Dedicated Leak Site (DLS). As of October 16, 2023, Open Source Intelligence has disclosed information on a total of 223 victims (including 196 posted by the DLS). Attackers remove victim information and stolen data when their needs are met or for other reasons, and the actual number of victims far exceeds this number.
PLAY ransomware uses the “RSA+AES” method to encrypt files, and no publicly available decryption tools have been found. After a successful attack, the attacker will ask the victim to contact him or her via a dark web address or e-mail.
Table 1-1 PLAY Ransomware Overview
|
Family name |
PLAY(aka PlayCrypt) |
|
First seen |
June 2022 |
|
Mode of transmission |
Phishing emails, exploits, etc |
|
Encrypted files’s extension |
.PLAY |
|
Encryption Method |
“RSA+AES” |
|
Decryption tool |
No public decryption tools were |
|
How and how much the ransom is paid |
Contact via dark web address or |
|
Encryption system |
Windows |
|
Double Extortion |
Yes |
|
Ransom note |
|
2.Protection recommendations
In response to ransomware attacks, Antiy recommends that individuals and enterprises take the following protective measures:
2.1 Personal Protection
1. Enhance the awareness of network security: Maintain good habits of using the Internet and actively learn the knowledge related to network security;
2. Confirm the content of the email: Check the sender’s email address, verify the identity information, be cautious about emails asking for account passwords, and avoid directly clicking links in suspicious emails and running attachments;
3. Install Endpoint Protection: Install anti-virus software. It is recommended that users of Antiy Intelligent Endpoint Protection system enable the ransomware defense tool module (enabled by default);
4. Strengthen password strength: Avoid using weak passwords, it is recommended to use passwords of 16 digits or longer, including combinations of uppercase and lowercase letters, numbers and symbols, and avoid multiple servers using the same password;
5. Change the password regularly: Change the system password regularly to avoid the intrusion of the system due to password leakage;
6. Update patches in time: It is recommended to enable automatic updates to install system patches, and vulnerable parts such as servers, databases, and middleware should update system patches in time;
7. Close high-risk ports: The principle of minimizing external services is adopted. It is recommended to close high-risk ports such as 135, 139, 445 and 3389, if there is no need to use them;
8. Close PowerShell: If you do not use the PowerShell command line tool, it is recommended to close it;
9. Regular data backup: Regularly back up important files, and the backup data should be isolated from the host.
2.2 Enterprise Protection
1. Network security training and security drills: Regularly carry out network security training and security drills to improve employees’ network security awareness;
2. Install Endpoint Protection system: Install anti-virus software, it is recommended to install the Antiy Intelligent Endpoint Protection system for different platforms;
3. Update patches in time: It is recommended to enable automatic updates to install system patches, and vulnerable parts such as servers, databases, and middleware should update system patches in time;
4. Enable logs: Enable key log collection functions (security logs, system logs, PowerShell logs, IIS logs, error logs, access logs, transmission logs, and cookie logs) to provide a basis for tracing security events.
5. Set IP whitelist rules: Configure Windows Firewall with Advanced Security, set inbound rules for remote desktop connections, and add the IP address or IP address range to the rule to prevent brute force attacks from IP outside the rules;
6. Host reinforcement: Perform penetration testing and security reinforcement for the system;
7. Deploy an Intrusion Detection System (IDS): Deploy traffic monitoring software or devices to facilitate the discovery and tracing of ransomware. Antiy Persistent Threat Detection System (PTD) takes network traffic as the detection and analysis object, can accurately detect known massive malicious code and network attack activities, and effectively discover suspicious network behaviors, assets and various unknown threats.
8. Disaster preparedness: Establish a security disaster preparedness plan to ensure that the backup business system can be quickly activated when a security incident occurs;
9. Antiy service: If you suffer a ransomware attack, it is recommended to disconnect the network in time, and protect the site and wait for the security engineer to check the computer. Antiy 7*24 hours service hotline: 400-840-9234.
It has been verified that Antiy Intelligent Endpoint Protection system (IEP) can effectively detect and kill PLAY ransomware.
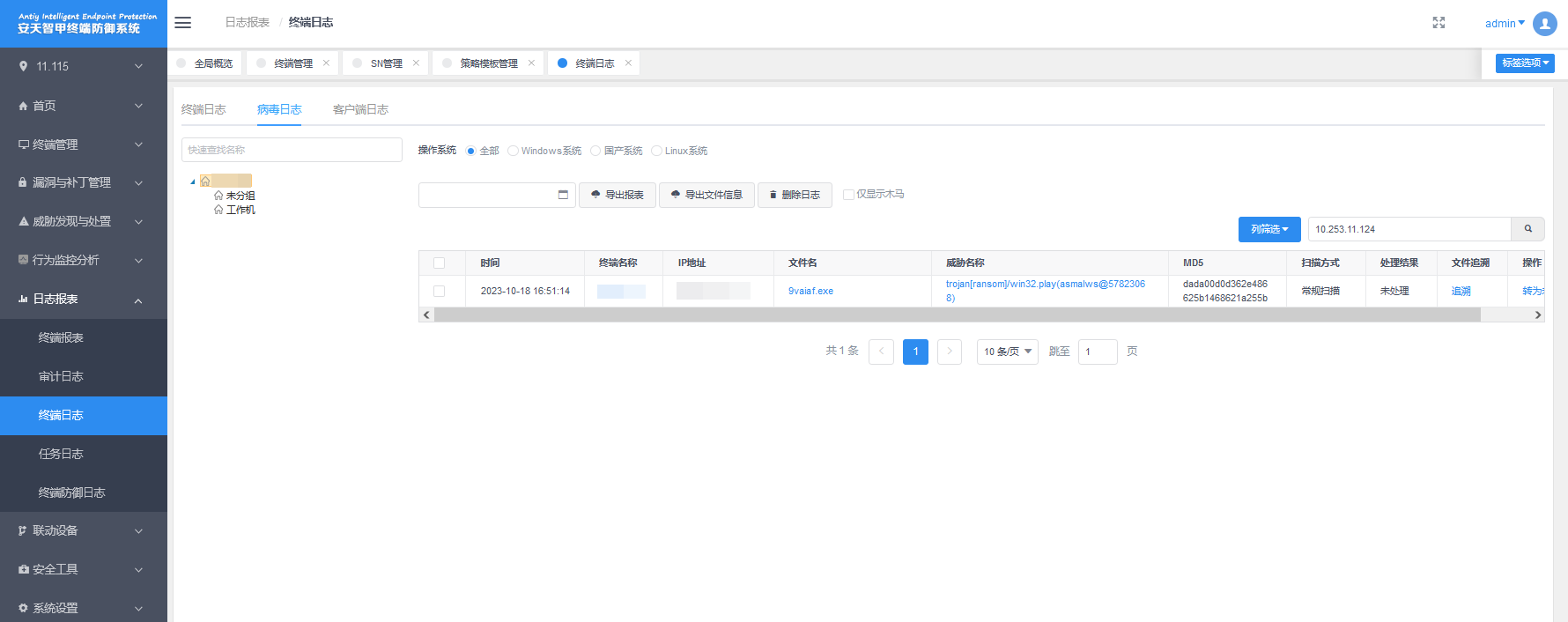
Figure 2-1 Antiy Intelligent Endpoint Protection system can effectively detect and kill PLAY ransomware
3.Disposal Recommendations
When the computer is infected with ransomware, do not panic, immediately carry out the following emergency work to reduce the harm caused by ransomware: Disconnect from the Internet, classify and dispose of them, report in time, troubleshooting and reinforcement, and contact professional services.
1. First, disconnect the computer infected with the ransomware from the network to prevent the ransomware from spreading laterally and continuing to infect other computer on the LAN.
2. Do not restart the computer, maybe there are logical problems in the writing of individual ransomware, and it is possible to retrieve some encrypted files without restarting.
3. Don’t rush to reinstall the system or format the hard drive to destroy the encrypted files. Backup the encrypted documents first. Encrypted files are not infectious and can be copied to any computer for backup storage, but the possibility of recovery is extremely small. You can consider whether to wait for the decryption programme according to the situation, and a small portion of ransomware decryption tools will be released for various reasons.
4. Although the type of ransomware family can be determined from information such as extension and ransom note, it is still impossible to accurately determine the type of ransomware due to the temporary absence of the specific process of how ransomware is encrypted and spread within the user’s network. Although it is possible to obtain functionally similar virus samples from threat intelligence databases and confirm them by simulating the infection process, the positioning of the infection process and the source of infection needs to be refined, and it is recommended to locate and trace by security services.
4.Recent cases of data leakage by PLAY ransomware
Since November 3, 2022, the Balloonfly attack group operating the PLAY ransomware has successively released victim information and stolen data on Tor’s Dedicated Leak Site (DLS), and as of October 16, 2023, its DLS has released information on a total of 196 victim units. After the ransom payment time is exceeded, some of the stolen data will be released, about 5G in size, and the content involved: personal data, customer documents, contracts, recruitment information, tax, financial information and other sensitive information.
The following are the recent victim cases released by the organizations behind the PLAY ransomware.
4.1 American information services company Hughes Gill Cochrane
The attackers updated their DLS with information related to Hughes Gill Cochrane, a American information services company, on Oct. 10, 2023, releasing a total 5G data on some of the stolen files including personal data, customer documents, contracts, job postings, tax, financial information, and etc.
4.2 Australian finance company NachtExpress Austria GmbH
The attackers updated their DLS with information related to NachtExpress Austria GmbH, a Australian financial company, on October 9, 2023, releasing a total 5G data on some of the stolen files including customer documents, contracts, job postings, ID cards, passports, payroll, tax, financial information, and etc.
4.3 British logistics company WCM Europe
The attackers updated their DLS with information related to WCM Europe, a British logistics company, on October 9, 2023, releasing a total 5G data on some of the files stolen, including customer documents, contracts, job postings, ID cards, payroll, tax, financial information, and etc.
5.Data statistics
PLAY ransomware has been active since June 2022, with a total of 223 successful attacks, except for 196 published by dark web addresses, the remaining 27 times are data monitored by Antiy CERT, and the main targets of the ransomware group are European and American countries.
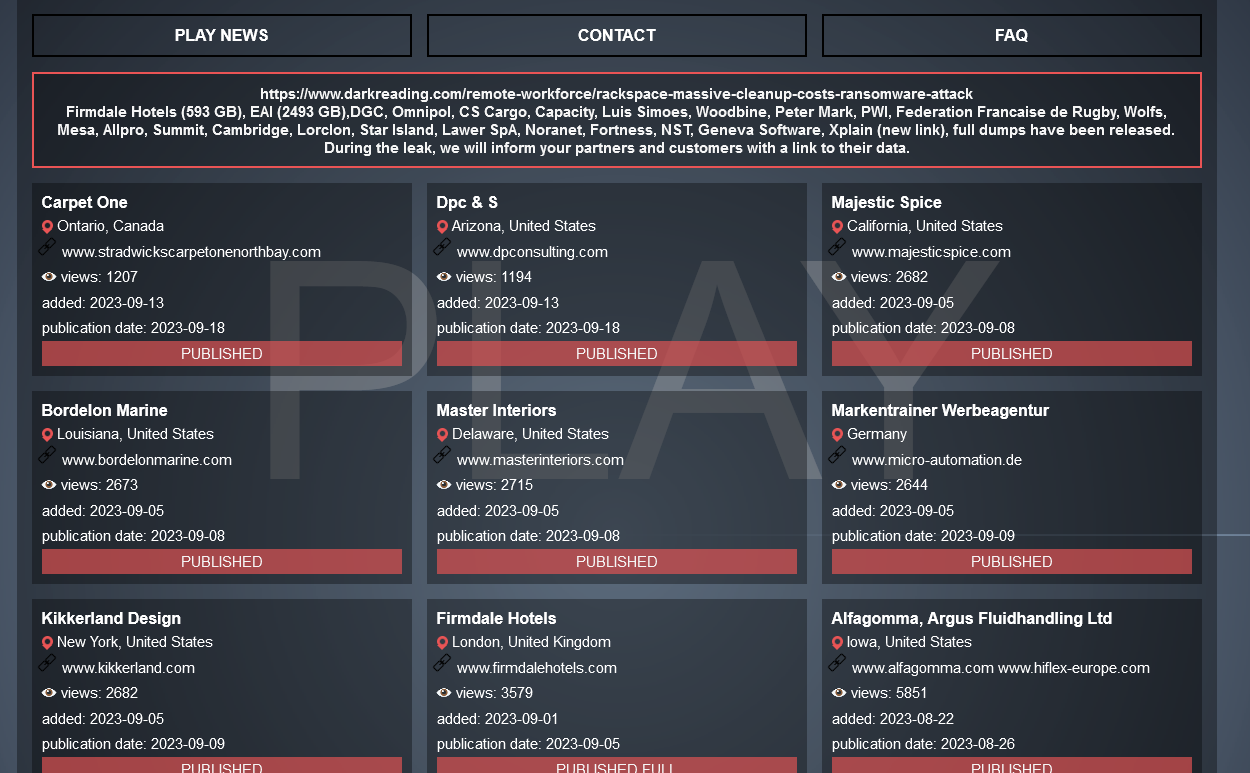
Figure 5-1 The attacker publishes some of the victim’s information at the dark web address
According to the information gathered, Antiy CERT collated the attacks of the PLAY ransomware between January and September 2023 and found that since May, the ransomware group has begun to frequent attacks, and the number of successful attacks per month has exceeded 20.

Figure 5-2 Number of successful attacks per month
6.Sample analysis
The ransomware uses the “RSA+AES” method for file and key encryption, and the encrypted file format is
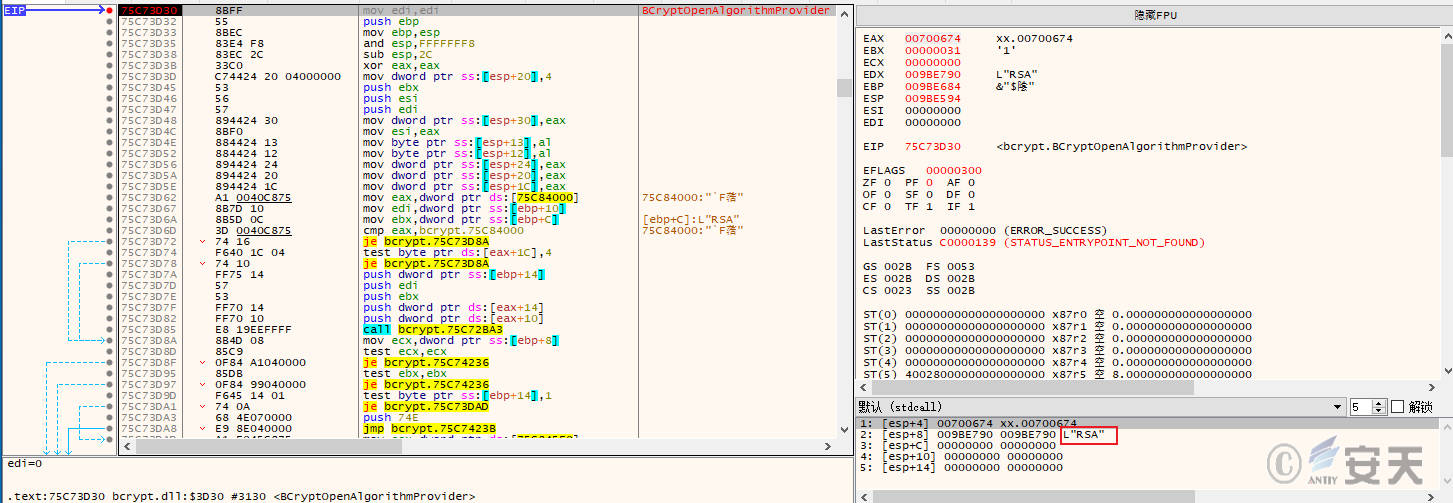
Figure 6-1 RSA algorithm
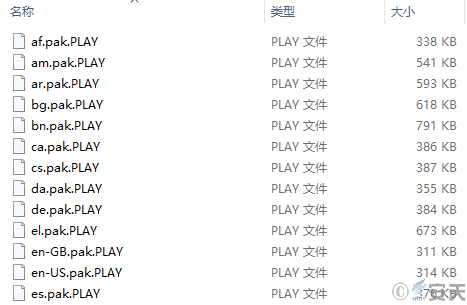
Figure 6-2 Encrypted files
The ransomware does not encrypt RAM and CD-ROM type storage, does not encrypt files named ReadMe.txt and bootmgr, does not encrypt files suffixed with PLAY, exe, msi, dll, lnk, sys, and deletes shadow copies.
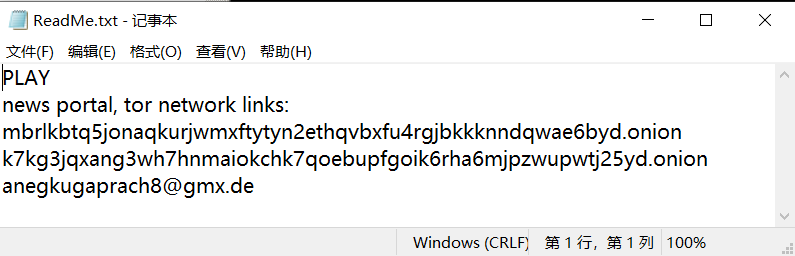
During encryption, a ransom note named “ReadMe.txt” is released at the root of each disk, which gives the dark web address and the attacker’s email address, as follows:
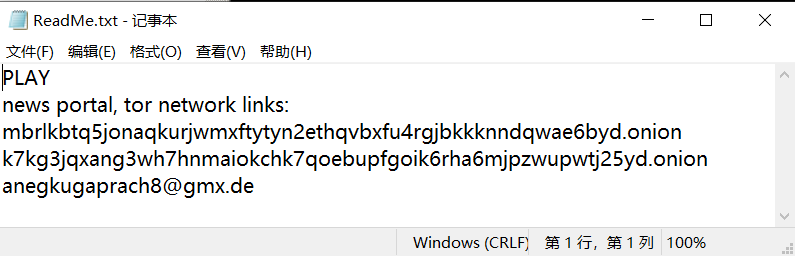
Figure 6-3 Content of ransom note
7.IoCs
|
IoCs |
|
5EA71206B0701FDFCEF38DC1080BEA3B |
|
8B7E28AB198C36E6CC75F95A9C513399 |
|
FFDBF029182D045C20D694E794755694 |
|
7B14F0CF56A38C8123F6FF9041159F0A |
|
DEE1B66AD2797868EDC4C5C7BB1A4603 |
|
mbrlkbta5jonaqkurjwmxftytyn2ethqvbxfu4rgjbkkknndqwae6byd.onion |
|
k7kg3jqxang3wh7hnmaiokchk7qoebupfgoik6rha6mjpzwupwtj25yd.onion |
|
anegkugaprach8@gmx.de |
8.Appendix 1: References
[1] Play Ransomware Group Using New Custom Data-Gathering Tools
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/play-ransomware-volume-shadow-copy