Antiy Responses to Ransomware WannaCry FAQ 3
Antiy Responses to Ransomware WannaCry FAQ 3
Antiy CERT
1.Why WannaCry is named “魔窟” in Chinese?
After the outbreak of WannaCry ransomware, there appears several version of Chinese name for the ransomware, such as “香菇”, “不哭”,but these names can not reflect the relative nature of the ransomware more precise, it also brings confusion to public and media to know the relevant threats. Such as the word fright doesn’t mean “cry”, while it is the abbreviation of encryption. In relative experts’ suggestion, the security engineers of the two provider that took systematic response to this incident in the first time in China (Antiy and 360 ) decided to name the threat “魔窟” in the subsequent documentation of the worm, WannayCry is derived from EternalBlue — the weaponized vulnerability of NSA, and it spread very fast via exploit. Its serial number in Microsoft is MS17-010 and the patch for WannayCry is published by Microsoft too. “魔” can indicate the seriousness of the threat, “窟” can reflect its spread characteristics of in use of the EternalBlue related vulnerability. It’s the second time that the Chinese capacity-based security vendors based on the principle of mutual recognition of the results to name a threat in Chinese.
2. Is there invalid version 2.0 of the switch domain name of WannaCry?
On May 13th, MalwareTech from the UK found that the worm had set an abort condition, that is, the worm will exit if it accesses the switch domain name (it’s also called kill-switch domain name in some organizations), and files will not be encrypted either; if it doesn’t access switch domain name , a series of malicious action will follow. The switch domain name was not registered at that time, so “MalwareTech” registered the domain name to block the spread of the malicious code. May 14th, some netizen said WannaCry 2.0 has appeared and switch domain name has been invalid in blocking the worm. After combining with the monitoring data and sample set, Antiy analysis team pointed out that until 10 p.m. on May 14, 2014, there isn’t any invalid version of the switch domain name. But through the sample exchange channel we found that other switch domain names have been tampered. This information is in fact a statement of the false positives of Kaspersky. In fact, the virus does have two versions, the version 1.0 was caught by Antiy on March 29th, and there isn’t any active spread module, and it isn’t confined to switch domain name, moreover the EternalBlue hasn’t been leaked at that time. Its version 2.0 is what we know as WannaCry. In the earlier report of Antiy, we have pointed out that WannaCry is made up of two parts-spread frameworks and the encryption module. The spread framework can contain by switch domain name, and the encryption module as the version 1.0 shows itself cannot spread (see the sample collection list of the previous analysis report of Antiy).
After a deep analysis of the relevant events, Antiy believes that the origin of this oolong event is the false positives (has been removed at noon on the 13th) that Costin·Raiu published on Twitter. Other sites have forwarding the corresponding content:
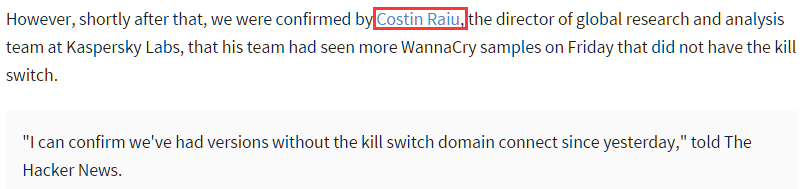
Later, Kaspersky clarified the relevant news:
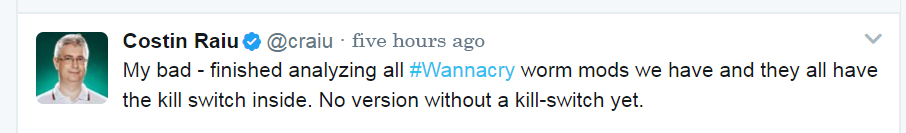
The HASH of the so-called invalid version 2.0 of the switch domain name is as below: “84C82835A5D21BBCF75A61706D8AB549”,only on the premise of embarking the matrix whose HASHES are “D5DCD28612F4D6FFCA0CFEAEFD606BCF” and “db349b97c37d22f5ea1d1841e3c89eb4” can this version spread, and the switch domain name is effective to the matrix.
At the same time we see that the attacker can modify the current worm to invalid version through changing its switch domain name or other principles of the switch domain name. While to other attackers, even if there is no source cade, they can made the switch domain into invalid via modify a few bytes of binary. Two samples of the modified version have been found by Antiy from its background sample pool, the modified switch domain name is “www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”, but we didn’t find any relative data of the samples on the network side, so we can not confirm the facticity of the two samples. Obviously, only count on the bug that the attacker left behind and the established conditions of switch domain name to take action is unreliable. Meanwhile, Antiy believes a good choice for the intranet users to kill the worm is directly contact the relevant domain, we still recommend users to analysis kill-switch domain through internal DNS (see “Boot Guide Against WannyCry”).
3. Can WannaCry spread through USB flash disk?
According to the present analysis, we believe that after the operation of WannaCry, it may copy a program module “@WanaDecryptor@.exe” that displays the ransom information to the USB disk that was inserted into the computer at that time, but this procedure will not lead to secondary transmission. WannaCry also has a language module that is responsible for displaying ransom information. This language set has 28 files which corresponding to 28 languages; the ransom page is shown to users after the module is loaded. WannaCry will scan the files in the drive and directory, if there exists a file with the specified suffix that can be encrypted, the program “@WanaDecryptor@.exe” will be placed in the drive or the folder later. If there is any USB disk inserted into the computer, this program will be copied to the USB disk. If the USB disk is inserted to other computers that didn’t infect by the virus, this program will not automatically execute because there isn’t any entrance-like Autoruan.inf. If a normal user executes the file, a prompt will also pop up and the user may get into a panic. But the module does not have data encryption and scanning infection function, and there is no other playload download function. Therefore, the worm will copy part of the program module to the USB disk, and there isn’t any secondary transmission.
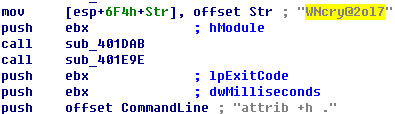
4. Does “Wannacry” have the default decryption password “WNcry@2ol7”?
The Wannacry worm does have such a password setting, but it is not used to encrypt user files. It is a built-in ZIP resource data decompression password of WannaCry ransomware.when running, the sample will use “WNcry @ 2ol7” as a decompression code, extract the sample of its own resource data and release to the current path, theses data containing extortion information, extortion background desktop , extortion form, language configuration, encrypted DLL and Key as well as other documents.
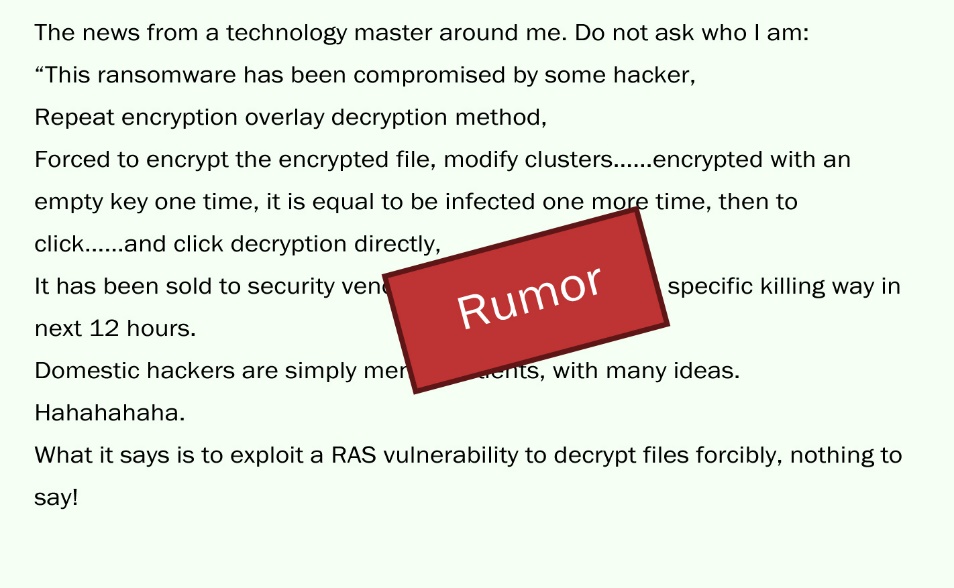
In addition, the online spread encrypted file of the virus existing “repeat encryption to override decryption method”. Obviously, only a little knowledge of the modern encryption algorithm can they see this message is purely crap, not excluding the “IQ fishing post.”
5. Why Wannacry data encryption part can be restored?
“Wannacry” worm’s encryption damage mechanism is as follows: first read the original file, then encrypt, last generate a new encrypted file. At this point, the original file and the encrypted file co-exist (as shown in the red part).
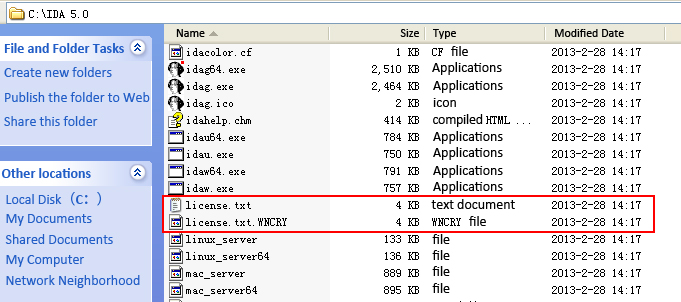
After that, the worm will move the unencrypted original file to the% Temp% directory and change the file name into a sequence number and modify the extension as WNCRYT, moving it twice. From the attacker’s intent, the restored file by the recovery tool presumably is not in the original directory, and does not match with the original name, resulting in ignoring and giving up by users.
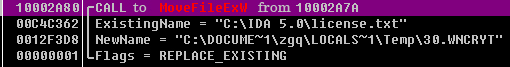
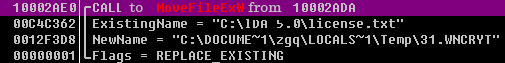
At this point, the original file does not exist, but the virus also tries to perform the following two operations, deleting the original file again.
![]()
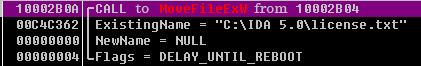
The sample will periodically call taskdl.exe (the main module released), deleting WNCRYT in % Temp% directory, while other ransomware is mainly used in the original sector for file coverage. So the ransomware can restore some of the files through file data.
6. Whether there were some mis-judgements and mistakes made by Antiy in previous analysis?
After the outbreak of the worm, according to our own observed information, customers’ phone call and mail, as well as the relevant threat intelligence information, Antiy made the conclusion that education network is the hardest hit field. In view of the “China Education and Research Network” itself is to serve our universities and research institutes of the network operating system, after currently continuous follow-up analysis, Antiy rectifies that the previous provided judgement of education network serious infected, not equivalent to the serious infection within “China Education and Research Network”. From currently acquired information, indeed, there are many colleges and universities infected with the virus, but confirmed by relevant information department that the university network (especially the student bedroom), often provided by a number of operators, including a certain percentage of infection which is not the cause from “China Education and Research Network”. Pondering the current situation and risks, we deem that the current risk areas should be concerned about is intranet and special equipment in part of the large-scale enterprises, some of which are superstitious physical isolation, but lacking effective means of basic governance, for the complexity of the network, uncontrollable exports, and ineffective isolation network. And the internal node basically is not effective to complete the security policy reinforcement, patch and upgrade security software version and feature library on time, resulting in rapid expansion after a single point infection. This should be the focus of follow-up emergency response and disposal.
We want to stress again that a comprehensive port shielding and temporary killing and so on, of course, is an effective emergency strategy, but from the perspective of government and enterprise network security, the enduring way is constructing basic security architecture and defense system, reinforcing node system configuration and timely upgrading patch, comprehensively deploying capacity-based security vendors to develop host protection and antivirus products and timely update synchronization
In addition, due to time constraints and our limited capacity, Antiy has made some mistakes in previous report on clerical errors and statements, as the following two:
(1) mistakenly the vulnerability number “MS17-010” written as “MS17-101”.
(2) the ransomware does not encrypt the executable program, while the first version of the report missed a word “不”, leading to the opposite meaning.
But we found in the follow-up reports on the topic, some of the vendors quoted the mistake into their reports. Although this is a relatively minor one, we truly feel sorry for misleading other teams and institutions. Therefore, it is necessary to right it.
Scan the following QR code to read this report, you can see extra surprises.

