Analysis on DDoS Attack Organization- “Chicken_mm”
ShadowHunter Team of Antiy Labs
| Abstract |
This article focuses on a cross-platform DDoS attack organization called “Chicken_mm” and gives an analysis. DDoS tools developed by this organization use SSH weak passwords and server vulnerabilities to control many Linux chickens. The malware of this organization can be traced back to 2009. This article mainly analyzes the controlling end, the generator and Windows and Linux variants in controlled end of this tool and makes a display of the homologous analysis and network infection of these samples.
Key findings
- This organization can be traced back to 2009 at least;
- Nicknames of two developers;
- May use SVN to develop collaboratively;
- Homologous analysis of strings, debugging information and configuration files;
- Windows version generator, Linux version generator and controller;
Four Windows version variants in controlled end, five Linux version variants;
Copyright
This copyright belongs to Antiy Labs which allows free use but for commercial use. When reprint, the article’s copyright, citations and links should be noted to ensure the integrity of it. When used in commercial purposes, please contact with Antiy Labs for authorization. Contact email: resource@antiy.cn.
1. Introduction
ShadowHunter team of Antiy Labs found a new malware whose system mutex’s name is “Chicken_Mutex_MM” and it is named as the “chicken_mm” in 2014. The main function of this sample is to collect basic information of the server and does DDoS attack. Through a correlative analysis, we found that its derived variants also had cross-platform ability, mainly including two versions as Windows and Linux system. The Windows version samples appeared as early as December 2009. The developers of “chicken_mm” adopted the SVN to develop collaboratively which evolved continuously for five years. Along with the increase of Linux server in domestic and the multi-limitations of Windows system, the hackers who are engaged in the DDoS before begin to change from Windows to Linux so that the attacked Linux servers increase dramatically. At the same time, it is the bandwidth advantages of the Linux server and the features of long-term online that make the DDoS attack more powerful.
Some variants of this sample has been mentioned in the previously reports, but most of the reports only introduced some certain variants without a comprehensively and deeply description of this organization. This article will post it to you in detail.
1.1 Brief Outline of its Operation
The organization of “chicken_mm” has been operating for more than four years so far. It mainly deals with the development and sales of DDoS tools. It is said that the organization has two developers at least. The developer named “Chen” (nickname) should be the main one whose nickname has been existed in multiple versions of the variants. The other developer named “maomao” (nickname) should be the assistant. The developed software is spread in a secret way such as building the hacker BBS and so on., and it is mainly sold to domestic private server maintenance personnel and the hackers who blackmail users by DDoS attacks with part of the cracked versions being spread out at the same time.
1.2 Evolved Variants of “Chicken_mm”
The Windows variants that intercepted by Antiy Labs mainly have four types, namely: Chicken, rjshell, svchost and IntergrateCHK, the evolution time of whom can be seen from their complied time (see figure 2). The windows version began to exist in December 2009; the October 2012 version and November 2013 version had two peaks in the transmission; Linux version began in April 2013 which supported both 32-bit and 64-bit; In the late 2013, Linux suffered a fierce attack and its version variants were mainly classified by the end numbers, including 10771, 10991, 36000, 58000, and M4 (see figure 3). At present, the mainly active charged end that being detected is Linux machine.

Figure 2 intercept variant sample

Figure 3 variant starting time
2. Analysis of Malware
2.1 Composition of Malware
2.1.1 Generator
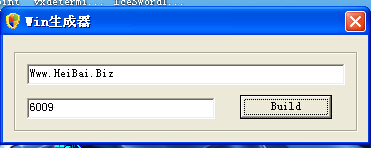
The generator is detected in the sample library. The sample containing an interface from which we found the generator of Windows version variants. The complied time of the generator is 23:57:00 on October 10, 2013 with a default generated end 6009 and a generated variant called IntergrateCHK.
Linux chicken generator is as simple as it and the Linux variant generated by 10991 is variant xudp which is attacked by the UDP flood DDoS. This variant appears in the Amazon EC2 server and multiple Linux systems in China.
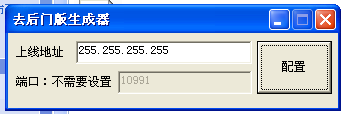
Figure 5 Xudp version 10991 generator
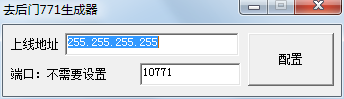
Figure 6 10771 generator
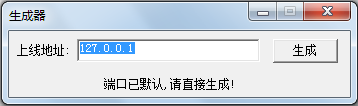 Figure 7 M3 generator
Figure 7 M3 generator
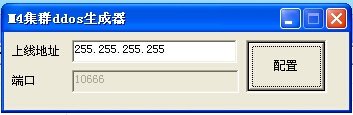
Figure 8 M4 generator
2.1.2 Controlling End
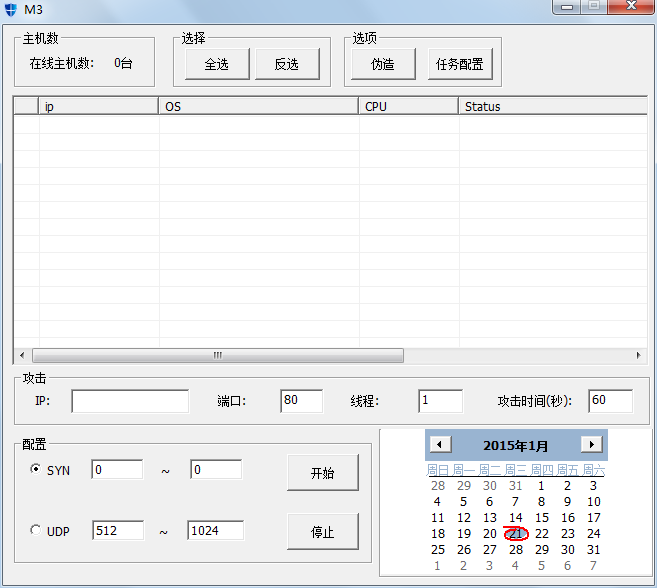
Figure 9 M3 controlling end
From the controlling end, we can see the list of the monitoring machine which contains the name of controlled end, operating system, CPU and network speed information. It has the function of half-connection, SYN flood, UDP flood attack function as well as batch forging.
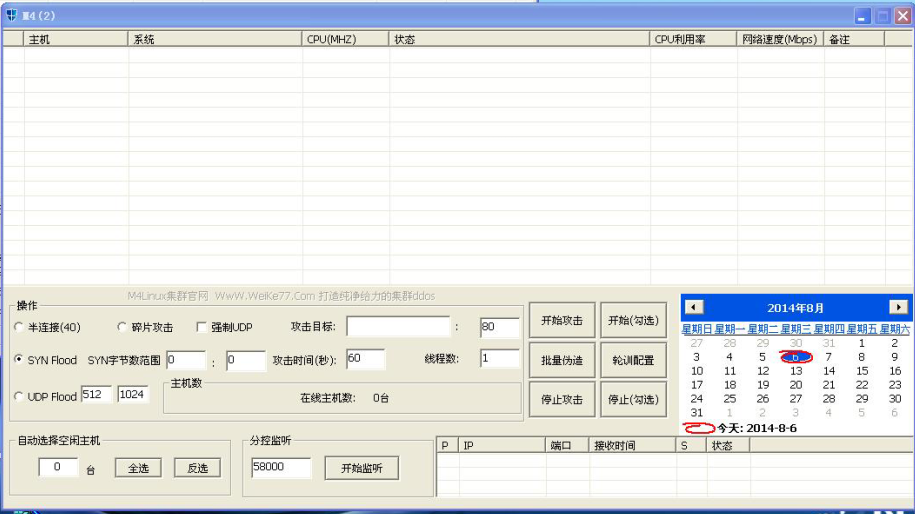
Figure 10 M4controlling end Manger
2.1.3 Controlled End
- Chicken Variant
After an automatic analysis and execution, Chicken variants in windows controlled end will create Chicken_mutex_mm mutex and release the c: \ mm ini (c: \ xmit ini) configuration file which is mainly used to save forged IP and end configuration file, get CPU information, make a DNS request as well as send machine related information to the controlled end at same time.
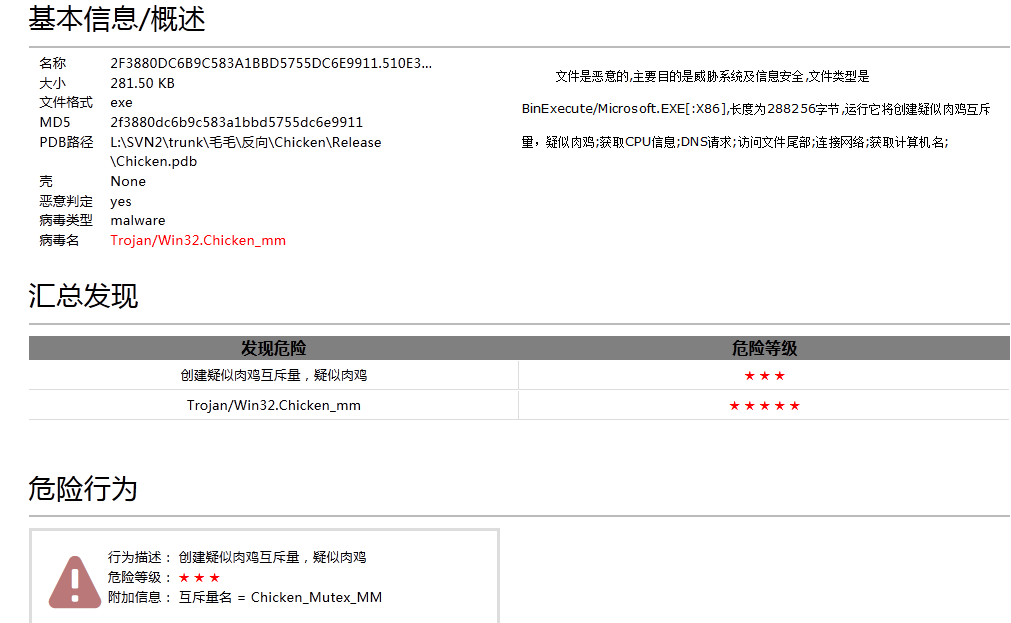
Figure 11 Chicken variant automatic analysis
The analysis of character string is as follows:
Table 1 variant character string
| Character String | Introduction |
| Chicken_Mutex_MM | Chicken_mm mutex |
| \Chicken\Release\Chicken.pdb | PDB information |
| L:\SVN2\trunk\ | PDB path |
| HARDWARE\DESCRIPTION\System\CentralProcessor\0
HARDWARE\DESCRIPTION\System\CentralProcessor\%d |
CPU information |
| \Processor(%d)\%% Processor Time
PdhGetFormattedCounterValue |
Being used to check usage rate of single core CPU |
| JanFebMarAprMayJunJulAugSepOctNovDec
SunMonTueWedThuFriSat |
Date |
| Windows NT
Windows 2000 Windows XP Windows Server 2003 Windows Vista Windows Server 2008 Windows 7 Windows Server 2008 R2 Windows 32s Windows Unknown |
System version |
- IntergrateCHK Variant
IntergrateCHK variant in windows controlled end will release the configuration file.fake.cfg of the forged end IP. While the fake configuration of Chicken variant is mm. Ini with the same content and form with IntergrateCHK variant.
First line: 0 is a signal for attack, 0 means stop, 1means attack;
Second line: 192.168.50.132:192.168.50.132 is the IP of LAN fake package;
Third line: 10000:60000 is the fake package end;
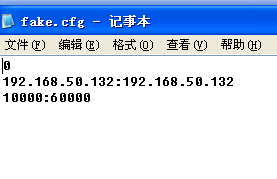
Figure12 fake.cfg configuration
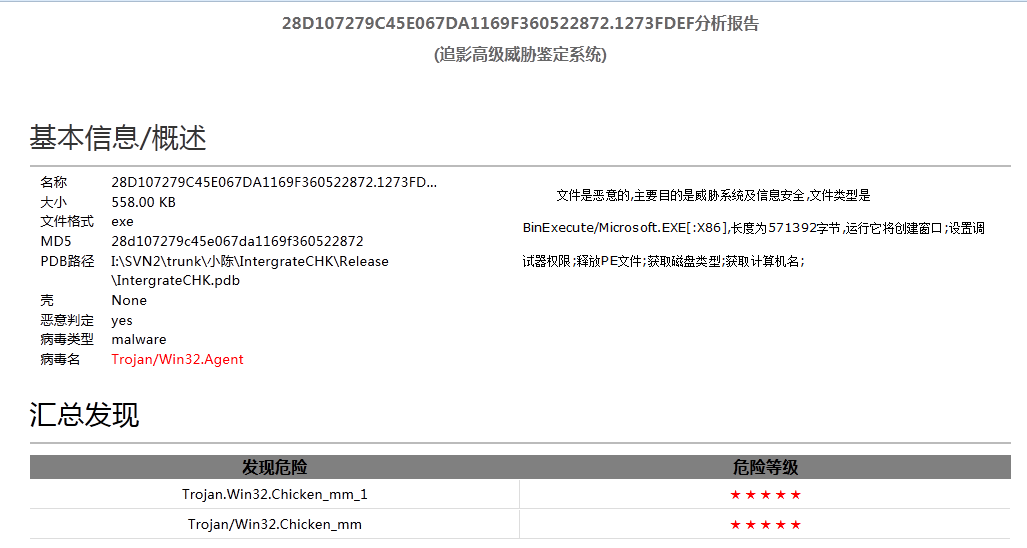
Figure13 IntergrateCHK variant automatic analysis
- svchost x64 Variant
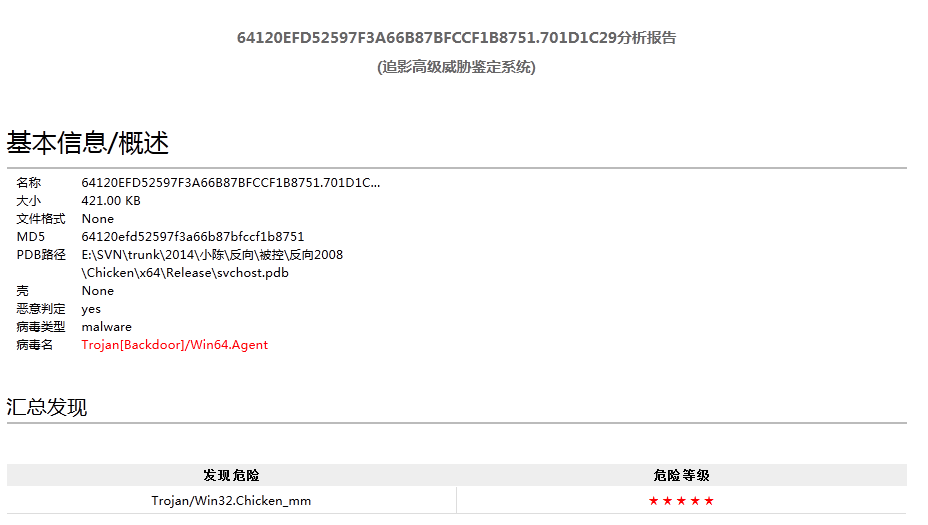
Figure 14 Windows 64-bit svchost controlled end automatic analysis
- Linux Variant
Linux is written by c + + with the function of extracting information and waiting for attack after instructions. The latest version can enlarge the DNS attack ability and part of Linux will also release fake. cfg configuration file. Through an analysis of “Antiy shadowhunter automated analysis system (http://zhuiying.antiy.cn/)”, the controlled sample of Linux variant: 22D0FA8571E1691CF2FFB1B20C1D536A is found to have some operations, such as getting system network card, CPU, memory information, releasing ELF files and access to the domain name zj.passwd1.com and reverse connection and so on.
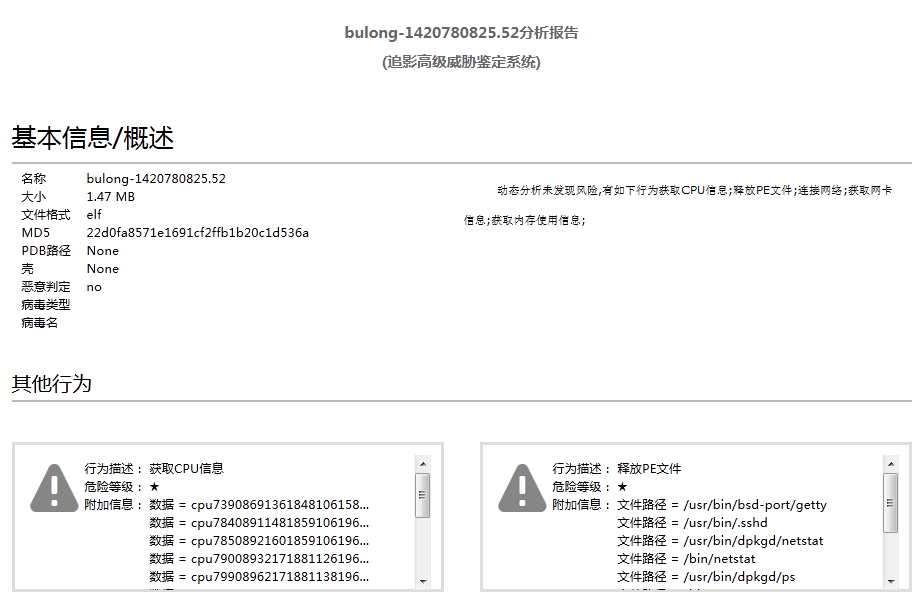
Figure 15 Linux automatic analysis
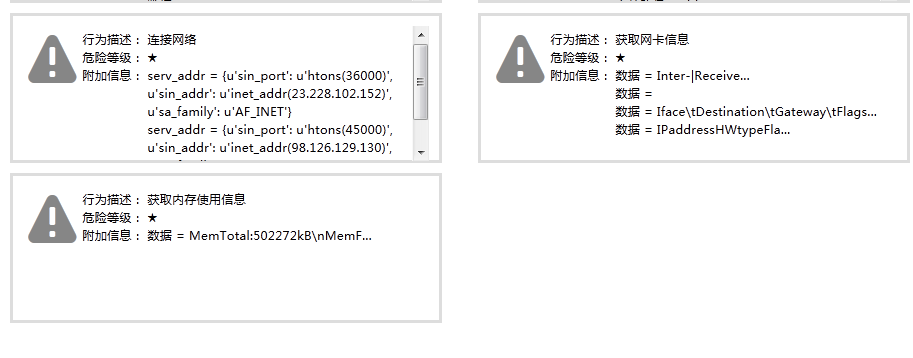
Figure16 Linux act
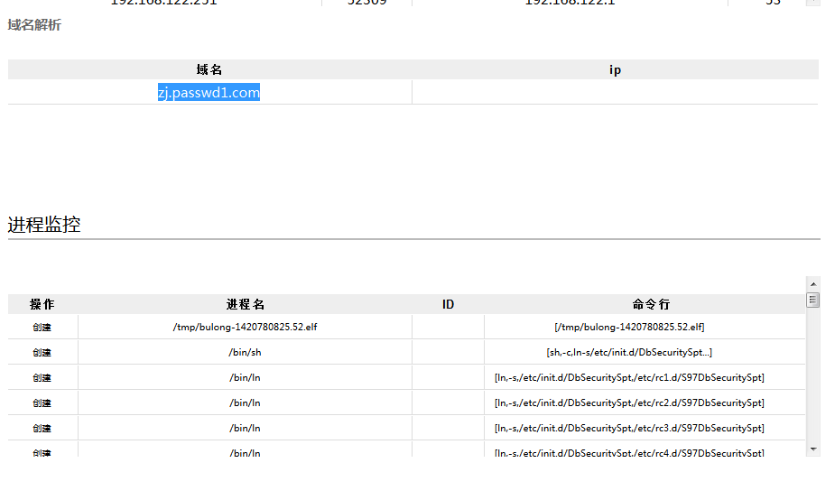
Figure17 domain and process operation
2.2 Homologous Analysis of Malware
According to the character string, debugging information, configuration files, configuration form and path and other information, we can find the homologous relation between the variant samples. Through this information, the controlling end, Windows variant and Linux version variants can be connected, and the controlling end 10771, 10991, 58000, the M4 and Windows controlled end and Linux version controlled end are also associated.
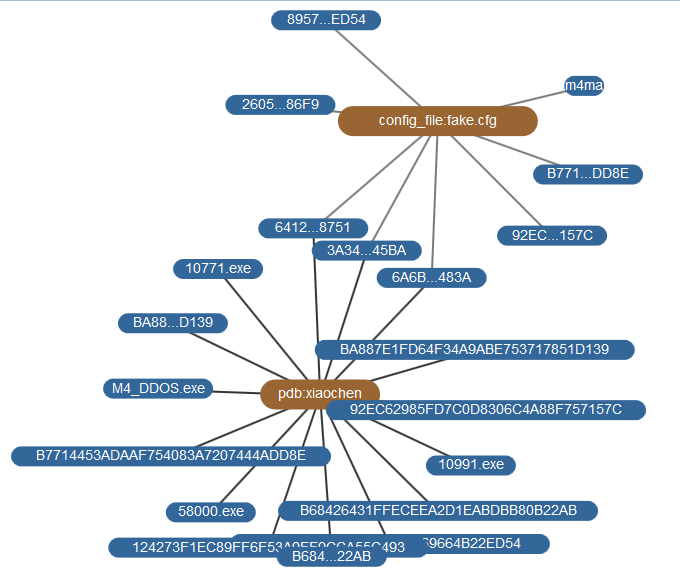
Figure 18 atlas of homologous analysis of malware
2.3 Information of Developers
Through the path “SVN \ trunk” in the debugging information contained in samples, we can infer that the DDoS tools developers write share code by SVN. There is some messy code in some of debugging path. Through an analysis, it is the developers’ Chinese nicknames “Chen” and “maomao” with some Chinese characters “fan xiang” and “bei kong” added behind, indicating that the developed component code is a reverse connection controlled end.
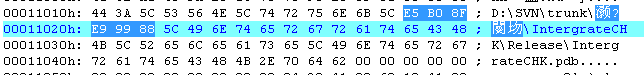
Figure 19 controlling end containing pdb
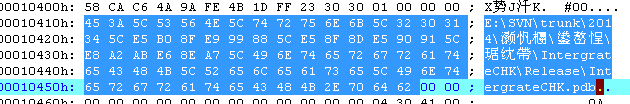 Figure20 controlling end containing pdb
Figure20 controlling end containing pdb
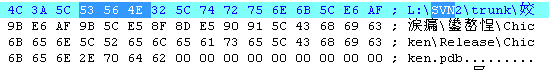
Figure21 controlling end containing pdb
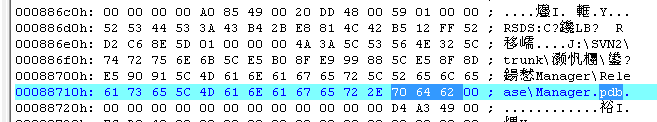
Figure22 controlling end containing pdb
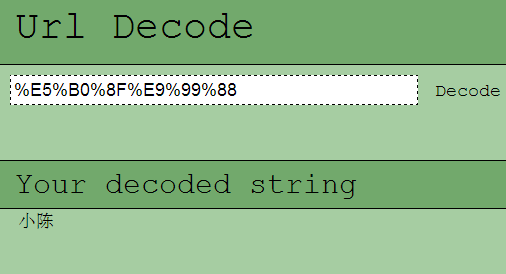
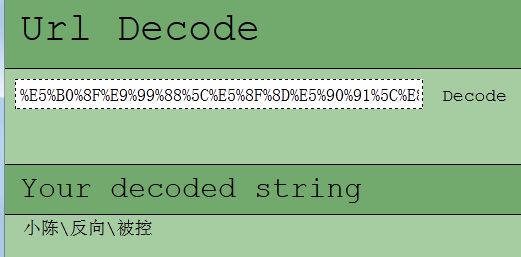
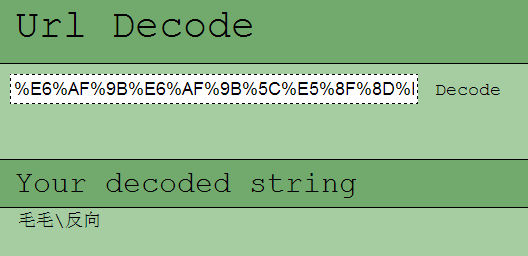
The messy code is written by URL, the decoding form is as follows:
Figure 23 URL encoding and decoding
Contains PDB information:
“J:\SVN2\trunk\毛毛-并发\反向\Chicken\Release\Chicken.pdb”
“E:\SVN\trunk\2014\小陈\反向\被控\IntergrateCHK\Release\IntergrateCHK.pdb”
“J:\SVN2\trunk\小陈\反向\Manager\Release\Manager.pdb”
After a judgment,it mainly use the way of building hacker BBS to sell attack software:
Figure 24 QQ sales screen-nap
3. Network Control and Infection
Domain and control IP used by attacker:
fymy.8800.org
kk.netbot.cc 70.39.77.126
yqv.3322.org 115.221.42.158
lindashuaiddos.f3322.org 222.186.52.153
192.161.177.203
98.126.193.143
61.153.104.230
198.148.92.100
111.cf22.com
syn.netbot.cc
DNS jj94.3322.org 42.51.4.216
ttlatale.3322.org
aaa.swhk.net
75.148my.com
199.36.72.222
4. Summary
As the Linux server proportion is increasingly higher, chickens attacked by DDoS have shifted from Windows to Linux system which includes smart cameras, NVR and so on, except for Linux server for the Web.
5. References
[1] New DDos Malware Targets Linux and Windows Systems
http://www.networkworld.com/article/2172819/smb/new-ddos-malware-targets-Linux-and-Windows-systems.html
[2] A quick look at a (new?) cross-platform DDoS botnet
http://www.cert.pl/news/7849/langswitch_lang/en
[3] versatile-ddos-trojan-for-Linux
https://securelist.com/analysis/publications/64361/versatile-ddos-trojan-for-Linux/
[4] Securelist – Information about Viruses, Hackers and Spam
https://securelist.com/blog/65192/elasticsearch-vuln-abuse-on-amazon-cloud-and-more-for-ddos-and-profit/
[5] http://www.v2ex.com/t/121336
[6] http://longgeek.com/2014/04/08/hacked-internal-openstack-cloud-platform/
[7] http://mo2g.com/view/81/
[8] http://blog.malwaremustdie.org/2013/12/lets-be-more-serious-about-dns-amp-elf.html
[9] Another look at cross platform DDos
http://sempersecurus.blogspot.com/2013/12/another-look-at-cross-platform-ddos.html
[10] Linux.BackDoor.Gates.5 — yet another Linux Trojan
http://news.drweb.com/?i=5801&c=5&lng=en&p=0
[11] http://bbs.appstar.com.cn/thread-10205-1-1.html
[12] Some tools to monitor BillGates CnC servers
https://github.com/ValdikSS/billgates-botnet-tracker
[13] http://tieba.baidu.com/p/2817141932
[14] http://blog.csdn.net/aaqqxx1910/article/details/41010279,2014.11.11
[15] http://www.v2ex.com/t/119848