Antiy Comprehensive Solution
Background and Challenge
With the rapid evolution and complexity of IT scenarios in institutions and enterprises, the threat entrances and targets that may be attacked are constantly increasing, and the difficulty of the responses after attacks is increased further. Traditional security architecture based on single-point protection and border deployment cannot meet the need anymore. At the same time, the businesses of institutions and companies have become highly dependent on the IT environment, and the losses caused by cyber-attacks are more and more.
Advanced threats and attacks aiming at high-value information targets are seriously threatening critical infrastructures, key institutions and companies with large data assets of China. Such attacks are widely using Zero-day vulnerability, advanced customized Trojans, covert channels, social engineering targeted attacks and other means, with difficulty to find, analyze, trace and protect the characteristics of the traditional security system.
Based on 17 years constantly competition with threats and accumulation of technologies, Antiy has formed a security defense capability from network borders, traffic, and endpoints to the overall situation awareness. In order to monitor and defend against different kinds of threats effectively, Antiy builds a strong security defense system through various layers of defense capabilities and forms in-depth defense system and solutions.
Product Deployment Plan
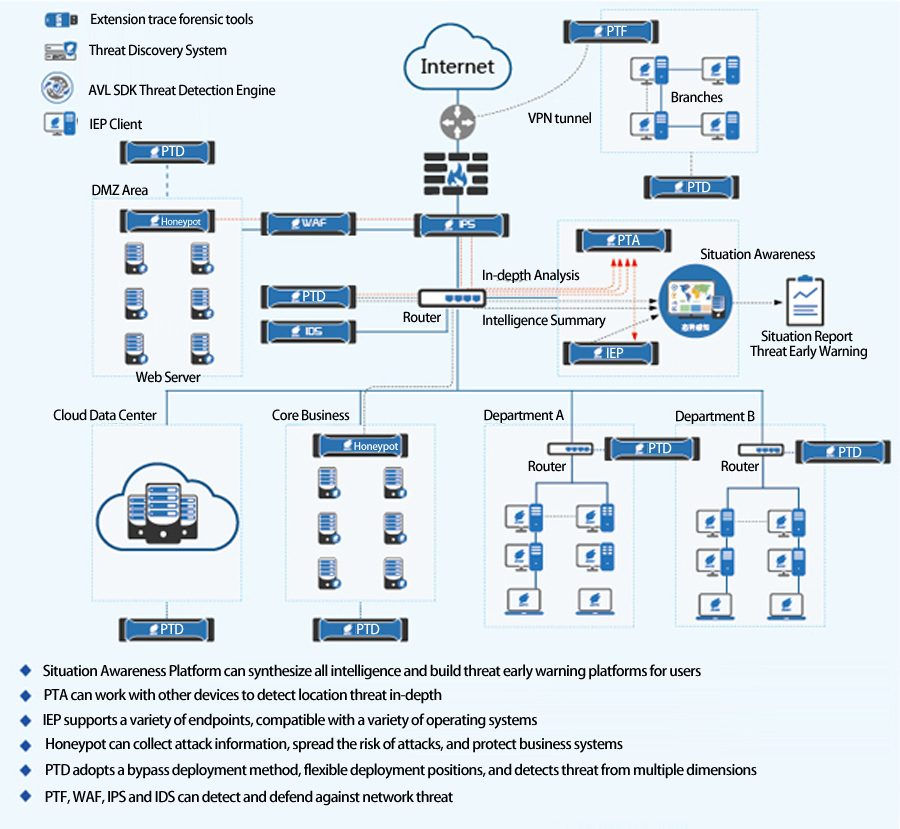
1. In-depth defense of security domain, key protection for core assets
Building defense at the security domain network boundary and terminal boundary, firstly, filtering known threats (known malicious behavior, known malicious code) and trusted objects to reduce the potential attackers enormously. According to the captured risk payload and suspicious files to have a comprehensive intelligent processing and combining deep static vector judgment and dynamic analysis, discovering unknown threats and handling them. The newly discovered unknown threat information can be used as threat beacon output to achieve system-wide sharing, improve overall protection efficiency, and form a multi-layer security deployment structure.
For different security level assets in user’s network, this solution can adopt different level protection measures to protect the core assets and key information of customers.
2. Flexible deployment, high return on investment
Implement flexible deployment of defense in depth by supporting vectors including “priority to Internet export traffic monitoring”, “priority to key areas export traffic monitoring”, “priority to high-risk endpoint defense”, and “periodic monitoring of the traffic through suspected high-risk areas”.
3. Discover unknown threats in time, present the comprehensive security situation
Whole network traffic and endpoint security detection and monitoring can intelligently monitor and track unknown threats and abnormal behaviors to realize timely discovery of unknown threats by using the powerful multi-object detection and multi-vector output capabilities of Antiy Next Generation Threat Detection Engine, together with investigation and forensics tools.
Antiy helps users to demonstrate the overall network security situation and major threats, high-risk nodes and risk areas that need more attention, and to “see” threats and recognize them by the automatic recording and analysis of network attack information, threat types, threat distribution scope, threat sources, victim hosts, development trends, threat history, etc..
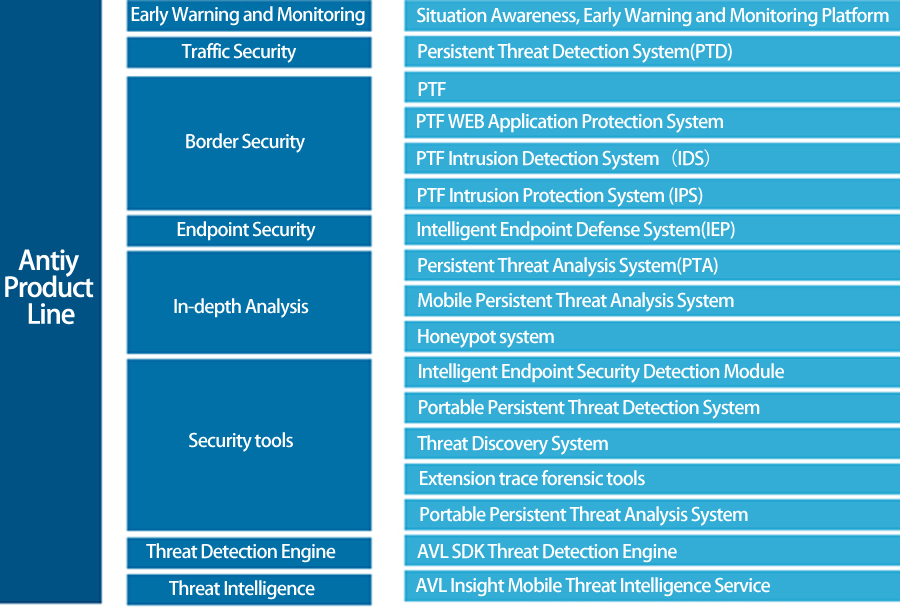
Security Product Line
System Architecture
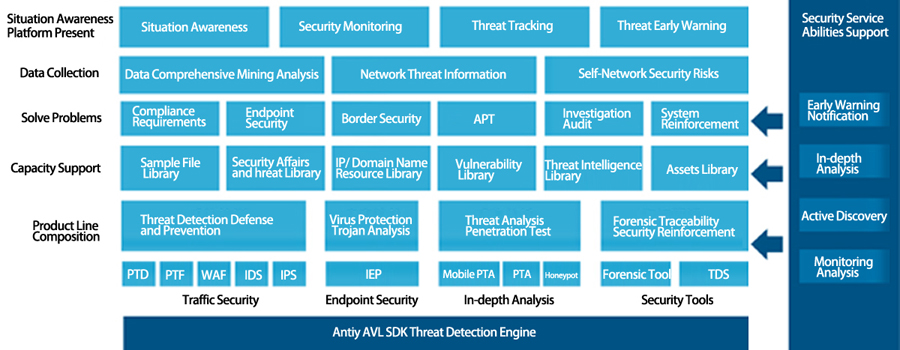
User Value
Complete localization processing capability, independent of vendor cloud capabilities, avoiding conflicts of security and confidentiality.
Complement with traditional security defense systems and reinforce monitoring and defense capabilities of advanced threats.
Ability to detect email attachments and various format files, discover “latent” malicious code and provide corresponding disposal capabilities.
Discover unknown threats and dispose timely by using dynamic identification and intelligent learning technology, the response and disposition speed of threats is superior to traditional security protection measures.
Detection and analysis of network traffic, discovery of malicious behavior and interception, and the ability to in-depth reveal the details of execution of malicious code and dynamic and static vectors. For unknown threats or abnormal behaviors, traceability and tracking can be performed across the entire network to achieve timely stop loss, effective early warning, correlation analysis, and effective evaluation.
